
It has been a quiet week, with even menace actors showing to take a while off for the vacations. We didn’t see a lot analysis launched on ransomware this week, with many of the information specializing in new assaults and LockBit associates more and more concentrating on hospitals.
These assaults embody ones towards Yakult Australia and the Ohio Lottery by the brand new DragonForce ransomware operation.
Essentially the most regarding information is that LockBit associates more and more goal hospitals in assaults, although the ransomware operation says it is towards the foundations.
In December 2022, one week earlier than Christmas, a LockBit affiliate attacked the Hospital for Sick Kids (SickKids) in Toronto, inflicting diagnostic and therapy delays. The ransomware operation stated this was towards the foundations and issued a free decryptor.
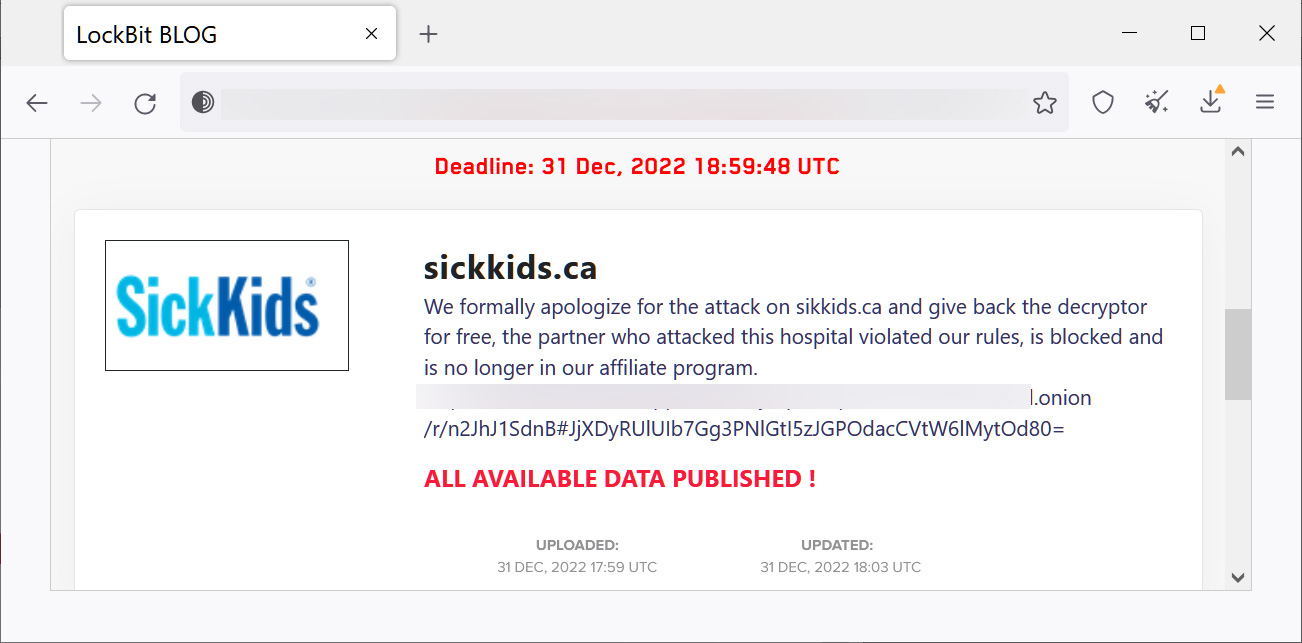
Supply: BleepingComputer
Nonetheless, this week, we realized that LockBit attacked three hospitals in Germany, disrupting emergency room providers.
We additionally realized about two New York hospitals in search of a court docket order to have Boston cloud storage firm Wasabi Applied sciences return stolen information saved on one in every of its servers by the LockBit ransomware gang.
Based on a court docket order, the Carthage Space Hospital and Claxton-Hepburn Medical Middle had been attacked in September, with the LockBit affiliate renting cloud storage at Wasabi to retailer stolen information.
The 2 hospitals now request that the courts drive Wasabi to supply and delete the information from their servers. The court docket paperwork point out that Wasabi is already working with the FBI and has shared a duplicate of the stolen information with them.
Lastly, Microsoft as soon as once more disabled the MSIX ms-appinstaller protocol handler after deactivating it in February 2022 after which enabling it once more in 2023 for some unknown motive.
Nonetheless, as malware campaigns proceed to abuse this function, which might result in ransomware assaults, the function has once more been disabled.
Contributors and those that supplied new ransomware info and tales this week embody: @malwrhunterteam, @serghei, @demonslay335, @BleepinComputer, @Ionut_Ilascu, @Seifreed, @fwosar, @LawrenceAbrams, @billtoulas, @MsftSecIntel, @DarkWebInformer, @BrettCallow, @pcrisk, and @Fortinet.
December twenty seventh 2023
Yakult Australia confirms ‘cyber incident’ after 95 GB information leak
Yakult Australia, producer of a probiotic milk drink, has confirmed experiencing a “cyber incident” in a press release to BleepingComputer. Each the corporate’s Australian and New Zealand IT methods have been affected.
Ohio Lottery hit by cyberattack claimed by DragonForce ransomware
The Ohio Lottery was compelled to close down some key methods after a cyberattack affected an undisclosed variety of inside purposes on Christmas Eve.
Lockbit ransomware disrupts emergency care at German hospitals
German hospital community Katholische Hospitalvereinigung Ostwestfalen (KHO) has confirmed that current service disruptions at three hospitals had been attributable to a Lockbit ransomware assault.
New STOP ransomware variant
PCrisk discovered a brand new STOP ransomware variant that appends the .cdmx extension.
New ransomware variant
PCrisk discovered a brand new ransomware variant that appends the .Tisak extension and drops a ransom be aware named Tisak_Help.txt.
December twenty eighth 2023
Microsoft disables MSIX protocol handler abused in malware assaults
Microsoft has once more disabled the MSIX ms-appinstaller protocol handler after a number of financially motivated menace teams abused it to contaminate Home windows customers with malware.
New Reside Crew ransomware
PCrisk discovered a brand new Reside Crew ransomware that appends the .LIVE and drops a ransom be aware named FILE RECOVERY_ID_[victim’s_ID].txt.
New SNet ransomware
PCrisk discovered a brand new ransomware variant that appends the .SNet extension and drops a ransom be aware named DecryptNote.txt.
Ransomware Roundup – 8base
8base is a financially motivated ransomware variant almost certainly primarily based on the Phobos ransomware. Per our FortiRecon info, the 8base ransomware first appeared in Might 2023.
December twenty ninth, 2023
Hospitals ask courts to drive cloud storage agency to return stolen information
Two not-for-profit hospitals in New York are in search of a court docket order to retrieve information stolen in an August ransomware assault that is now saved on the servers of a Boston cloud storage firm.
That is it for this week! Hope everybody has a pleasant weekend!


