Government abstract
Within the present cyber panorama, adversaries generally make use of phishing because the main method to compromise enterprise safety. The susceptibility of human conduct makes people the weakest hyperlink within the safety chain. Consequently, there may be an pressing want for sturdy cybersecurity measures. Phishing, which capitalizes on exploiting human conduct and vulnerabilities, stays the adversary’s best choice. To counter this risk successfully, ongoing training and consciousness initiatives are important. Organizations should acknowledge and tackle the pivotal function of human vulnerability in cybersecurity.
Throughout common enterprise hours, an alarm was generated as a result of a buyer’s consumer that had interacted with a probably malicious phishing hyperlink. This prompted an intensive investigation performed by analysts that concerned leveraging a number of Open-Supply Intelligence (OSINT) instruments reminiscent of VirusTotal and URLscan.io. By way of a meticulous examination, analysts have been in a position to unveil suspicious scripts throughout the phishing webpage’s Doc Object Mannequin (DOM) that pinpointed an try to exfiltrate consumer credentials. This detailed evaluation emphasizes the significance of proactive cybersecurity measures and showcases the effectiveness of analysts leveraging OSINT instruments together with their experience to precisely assess threats inside buyer’s environments.
Investigation
The alarm
The Managed Detection and Response (MDR) Safety Operations Heart (SOC) initially obtained an alarm triggered by a probably malicious URL {that a} consumer obtained of their inbox. Workplace 365’s risk intelligence feed flagged this URL as probably malicious. The preliminary steps in addressing this alarm contain two key actions.
First, it’s essential to find out the scope of impression on the client’s atmosphere by assessing what number of different customers obtained the identical URL. Second, an intensive validation course of is crucial to verify whether or not the URL is certainly malicious. These preliminary steps lay the inspiration for a complete response to safeguard the safety of the atmosphere.
To find out what number of customers obtained the identical URL, a complete search throughout the buyer’s atmosphere revealed that no different customers obtained the identical URL. In consequence, just one consumer is affected, suggesting that that is an remoted incident and doesn’t seem like a part of a focused assault on the client’s atmosphere. With this understanding, the main focus can now shift to the second step: Validating the status of the URL.
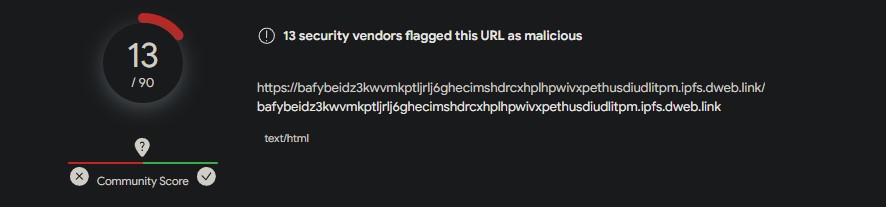
By using the OSINT software VirusTotal and inputting the URL obtained by the consumer, we intention to evaluate its potential risk degree. VirusTotal aggregates outcomes from numerous safety distributors to supply a complete evaluation. Within the present analysis, 13 out of 90 safety distributors classify this URL as malicious. It is vital to notice that whereas the variety of distributors flagging the URL is a key issue, a conclusive willpower of malicious intent sometimes considers a consensus amongst a good portion of those distributors. A better variety of detections by various safety platforms strengthens the arrogance in labeling the URL as malicious.
With a probably malicious URL recognized, it’s crucial to delve deeper to determine the underlying causes for its malicious status. Analysts will make the most of a software reminiscent of URLscan.io for this goal. URLscan.io serves as a sandbox, offering a risk-free atmosphere for visiting web sites. This software is instrumental in conducting an intensive examination to uncover the nuances contributing to the URL’s malicious classification.
After getting into our recognized malicious URL into URLscan.io, we are able to look at the webpage supposed for our buyer’s consumer. Upon visiting this URL, a PDF file is ready for consumer obtain. Nonetheless, a mere screenshot of the webpage is inadequate to supply a definitive status. To acquire extra perception, we should delve deeper into the webpage by analyzing its DOM.
The DOM includes the important parts of a webpage, encompassing HTML, CSS, and JavaScript that outline the construction, presentation, and conduct of the web page. URLscan.io facilitates a handy examination of the DOM. In reviewing the DOM, explicit consideration is given to figuring out any malicious scripts that could be current. The main target is usually on looking for the HTML tags, which denote script components inside a webpage.
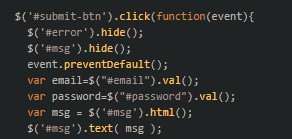
Within the analysis of the DOM related to the possibly malicious URL, a number of tags are noticed. Inside these tags, it turns into obvious that upon the consumer’s interplay with the “obtain all” button, a immediate will request them to enter their electronic mail and password.
That is the beginning of the script that defines the e-mail and password variables.
Persevering with by the script, extra regarding code emerges. Whereas the consumer is prompted to enter electronic mail and password data, it turns into obvious that the adversary has crafted code designed to falsely declare that the entered electronic mail and/or password is inaccurate, even when it isn’t. This conduct aligns with typical phishing actions, the place malicious actors try to induce customers to enter their credentials a number of instances. This tactic goals to take advantage of potential typos or errors within the entered data, guaranteeing that the adversary in the end obtains the proper credentials from the sufferer.
After the consumer submits their credentials, the consumer’s electronic mail and password are transmitted to the web site “hxxps://btmalta.cam/wefmail/electronic mail (1).php” by way of an AJAX POST request. Within the context of net growth, an AJAX (Asynchronous JavaScript and XML) POST is a method that enables information to be despatched to a server asynchronously with out requiring a web page refresh. Sadly, malicious actors exploit this performance to surreptitiously transmit delicate consumer data, as noticed on this occasion.
Conducting OSINT on the aforementioned web site (“hxxps://btmalta.cam/wefmail/electronic mail (1).php”) reveals a malicious status, notably marked by its comparatively current creation, being solely 80 days previous from the registry date. The registration age of a website is a helpful consider assessing its credibility. On this case, the mixture of a newly registered area and indications of malicious exercise raises important considerations. It strongly means that the adversary is probably going using this area to gather the user-entered electronic mail and password intentionally.
Contemplating the aforementioned particulars, it turns into extra evident that it is a credible phishing try focusing on one in all our prospects’ customers. The tactic of knowledge transmission, the malicious status of the area, and its current registration collectively underscore the severity of the scenario.
Buyer interplay
After the findings have been noticed, an investigation was created for the client to evaluate. If the client’s affected consumer entered any credential data, this implies the consumer account needs to be thought of compromised. Since this affected a consumer throughout the prospects Office365 atmosphere, it was advisable for the client comply with the rules set by Microsoft in an occasion of an electronic mail account compromise: Responding to a compromised electronic mail account
fight towards phishing makes an attempt
Within the ongoing battle towards phishing makes an attempt, implementing efficient methods is paramount to fortifying cybersecurity defenses. Listed beneath are among the many key practices and countermeasures to safeguard your group from falling sufferer to malicious phishing actions.
- Be sure that customers undergo common safety coaching to study concerning the risks of potential phishing makes an attempt.
- Make use of processes that enable customers to report potential phishing emails that they obtain.
- Guarantee customers are correctly using Multi-Issue Authentication (MFA)
- Guarantee robust password insurance policies are in place to forestall any weak or insecure passwords from getting used.
- To examine to see in case your password or electronic mail has ever been concerned in an information breach you need to use the free software https://haveibeenpwned.com/ to examine.