
Safety researchers analyzing the exercise of the lately emerged 3AM ransomware operation uncovered shut connections with notorious teams, such because the Conti syndicate and the Royal ransomware gang.
3AM, additionally spelled ThreeAM, has additionally been attempting out a brand new extortion tactic: sharing information of a knowledge leak with the sufferer’s social media followers and utilizing bots to answer to high-ranking accounts on X (previously Twitter) with messages pointing to information leaks.
3AM tied to Conti cybercrime syndicate
The 3AM ransomware gang’s exercise was first documented publicly in mid-September when the Menace Hunter Crew at Symantec, now a part of Broadcom, revealed that they observed risk actors switching to ThreeAM ransomware after failing to deploy the LockBit malware.
In keeping with researchers at French cybersecurity firm Intrinsec, ThreeAM is probably going linked to the Royal ransomware group – now rebranded as Blacksuit, a gang of former members of Crew 2 throughout the Conti syndicate.
The hyperlink between 3AM ransomware and the Conti syndicate turned stronger as Intrinsec progressed of their investigation of the group’s techniques, infrastructure utilized in assaults, and communication channels.
In a report shared with BleepingComputer, Intrinsec says that their evaluation of the risk actor revealed “a big overlap” in communication channels, infrastructure, and techniques, strategies, and procedures (TTPs) between 3AM and the Conti syndicate.
Utilizing an IP handle that Symantec listed as a community indicator of compromise (185.202.0[.]111) of their report on the risk actor’s assault, Intrinsec researchers discovered on VirusTotal a PowerShell script for dropping Cobalt Strike that had been detected since 2020.
In one other discovering, Intrinsec noticed a SOCKS4 proxy on TCP port 8000 that’s sometimes used for tunneling communication. The researchers word that “the signature related to this Socks4 service was displayed on two IP addresses exhibiting such a proxy hallmark since mid-2022.”
“This timeline of exercise is in step with the one recognized for Zeon ransomware, which was noticed in September 2022 in accordance with Development Micro however may have first spiked even earlier in late January 2022″ – Intrinsec
Moreover, Intrinsec analysts recognized a TLS certificates for an RDP service on a machine known as “DESKTOP-TCRDU4C” that’s related to assaults from mid-2022, a few of them leveraging the IcedID malware dropper in campaings from Royal ransomware.
Beforehand, IcedID was used to ship ransomware from XingLocker, which rebranded as Quantum, and Conti teams.
The researchers additionally discovered that the HTML content material from 3AM’s information leak website within the Tor community had been listed by the Shodan platform for internet-connected servers, that means that it was out there over the clear net.
Shodan confirmed an IP handle related to an “nginx product that may very well be used to proxy community site visitors upstream in the direction of a real server,” the researcher mentioned.
Following the path, Intrinsec observed that the identical Apache httpd banner on the server was current on 27 different servers, all hosted by a company known as “UAB Cherry Servers.”
Cherry Servers is a Lithuanian internet hosting firm that has a comparatively low fraud danger, however risk intelligence providers have seen the corporate’s prospects internet hosting malware, comparable to Cobalt Strike.
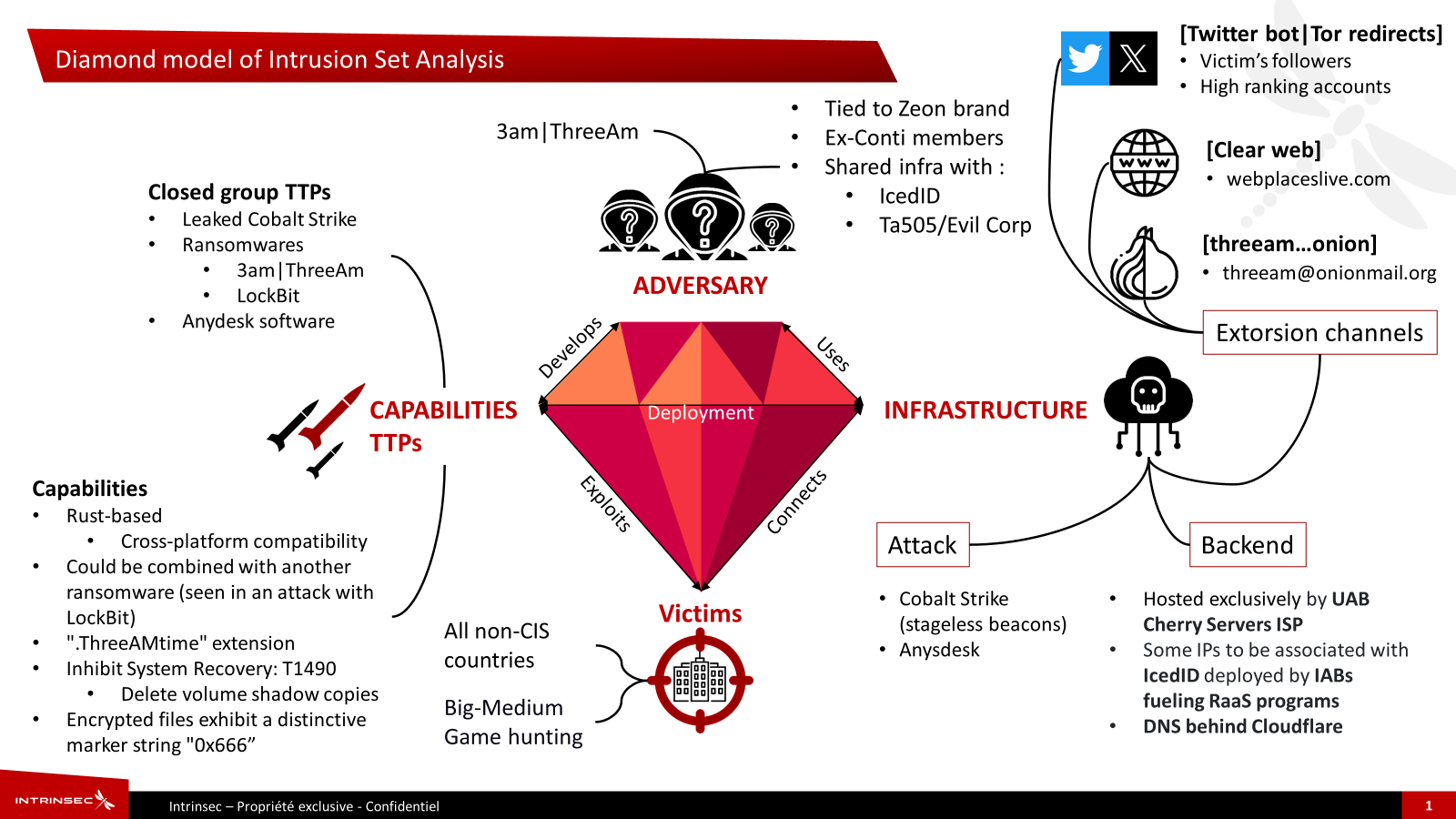
supply: Intrinsec
A better evaluation revealed that six of the 27 servers shared the identical port, protocol, Apache product with the identical model, autonomous system (AS16125), group, and the textual content “llc” indicating a ‘restricted legal responsibility firm’.
Aside from this, the domains on the analyzed IP addresses had TLS certificates from Google Belief Providers LLC and had been transferred to Cloudflare.
Intrinsec discovered the identical IP subnet in a report from cybersecurity and managed providers firm Bridewell final April, which notes that the ALPHV/BlackCat ransomware operation hosted its backend infrastructure solely on the UAB Cherry Servers ISP, used IP addresses in the identical subnet, and a few of them have been related to the IcedID malware that had been used for Conti assaults.
Intrinsec’s technical discovering aligns with risk intelligence from RedSense saying that ALPHV is an allied group that’s not a part of the Conti syndicate however may assist the gang in varied methods to hold out assaults.
Testing Twitter bots to stress sufferer
Digging for extra public details about ThreeAM, Intrinsec’s cyber risk intelligence group found that the gang probably examined a brand new extortion method utilizing automated replies on X (previously Twitter) to broadcast information of their profitable assaults.
The risk actor arrange an X/Twitter account final 12 months on August 10 and used it to go away “quite a few replies” mentioning one in every of its victims and redirecting to the information leak website.
3AM ransomware replied with a hyperlink to 3AM’s information leak website on Tor community to tweets from the sufferer in addition to varied accounts, some with lots of of hundreds of followers, comparable to the instance beneath.
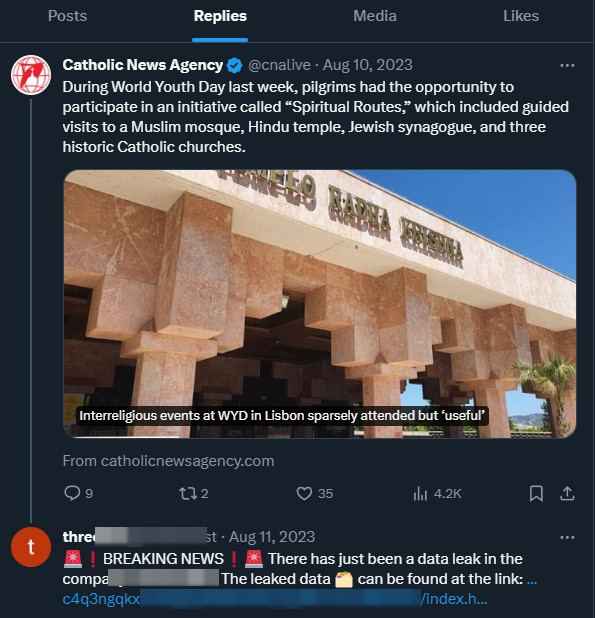
supply: BleepingComputer
This tactic was probably employed to unfold the information of the assault and subsequent information leak and to break the enterprise repute of the sufferer – a U.S. firm offering automated packaging providers.
Intrinsec researchers decided that ThreeAM used the identical message in an automatic vogue to reply to a number of tweets from among the sufferer’s followers.
“We assess with good confidence that an X/Twitter bot was probably used to conduct such a reputation and disgrace marketing campaign,” Intrinsec writes within the non-public report shared with BleepingComputer.
Pointing to this idea is the elevated quantity and frequency of ThreeAM replies, generally as many as 86 per day, properly over the typical of an actual consumer, and round 4 per minute.
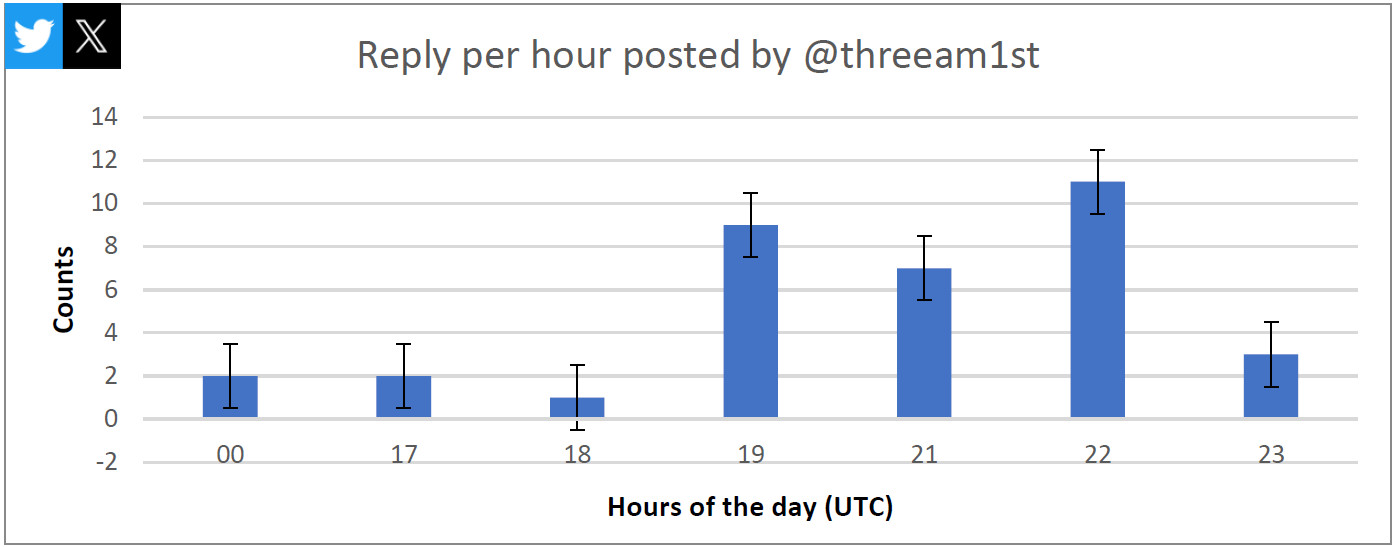
supply: Intrinsec
It’s price noting that this tactic seems to have been employed solely with one 3AM sufferer, probably as a result of it didn’t yield the outcomes the risk actor anticipated.
A take a look at 3AM’s information leak website within the Tor community reveals an inventory of 19 victims who didn’t pay the ransom and whose information the risk actor leaked. Surprisingly, 3AM’s website appears to be like similar to the one the LockBit ransomware operation makes use of.
Intrinsec notes that “though ThreeAM intrusion units appear to be a much less refined subgroup of Royal” and the gang shows much less operational safety it shouldn’t be underestimated and it may nonetheless deploy numerous assaults.
The Conti syndicate
The Conti cybercrime syndicate was the most important and most aggressive ransomware operation between 2020 and when it shut down in Could 2022 following a knowledge breach often called Conti Leaks.
Throughout one in every of its best hacking sprees, the operation’s associates compromised greater than 40 organizations in a little bit beneath a month, the quickest assaults taking simply three days from preliminary entry to encrypting techniques.
The syndicate break up into a number of cells and the ransomware model dissolved however lots of its members and associates partnered with different operations, contributing with skilled people for all phases of an assault, from goal evaluation and preliminary entry, to negotiations, infrastructure, builders, and operators.
One continuation is Royal ransomware, “the direct inheritor of Conti,” in accordance with RedSense cyber risk intelligence researcher Yelisey Bohuslavskiy, a closed operation with members understanding each other personally.
Due to a publish on a hacker discussion board, some researchers speculate that one of many leaders of the Royal group is a risk actor calling themselves Baddie. Nonetheless, no different proof has been disclosed publicly about this and ransomware as of late is a always shifting scene, and Baddie may have simply been working with a number of ransomware-as-a-service (RaaS) operations, Bohuslavskiy says.
On a scene as chaotic as associates working with a number of RaaS teams, it’s tough to trace the members of a selected gang or tie them to an operation.


