
The Pc Emergency Response Crew in Ukraine (CERT-UA) is warning a couple of PurpleFox malware marketing campaign that has contaminated at the least 2,000 computer systems within the nation.
The precise affect of this widespread an infection and whether or not it has affected state organizations or common individuals’s computer systems hasn’t been decided, however the company has shared detailed data on tips on how to find infections and take away the malware.
PurpleFox (or ‘DirtyMoe’) is a modular Home windows botnet malware first noticed in 2018 that comes with a rootkit module permitting it to cover and persist between gadget reboots.
It may be used as a downloader that introduces stronger second-stage payloads on compromised techniques, affords its operators backdoor capabilities, and may act as a distributed denial of service (DDoS) bot.
In October 2021, researchers observed that new variations of PurpleFox switched to utilizing WebSocket for command and management (C2) communications for stealth. In January 2022, a marketing campaign unfold the malware beneath the guise of a Telegram desktop app.
Ukrainian an infection wave
CERT-UA used IoCs shared by Avast and TrendMicro to determine PurpleFox malware infections on Ukrainian computer systems, monitoring the exercise beneath the identifier ‘UAC-0027.’
“Within the strategy of an in depth examine of the cyber risk, analysis was carried out on the samples of malicious software program obtained, the traits of the working infrastructure of the management servers have been recognized, and greater than 2000 contaminated computer systems within the Ukrainian section of the web have been found,” explains CERT-UA in a machine-translated safety warning.
CERT-UA says PurpleFox sometimes infects techniques when victims launch laced MSI installers and highlights its self-propagation capabilities utilizing exploits for identified flaws and password brute-forcing.
The company recommends isolating techniques that run outdated OS variations and software program utilizing VLAN or bodily community segmentation with incoming/outgoing filtering to forestall spreading.
CERT-UA monitored contaminated hosts between January 20 and 31, 2024, detecting 486 intermediate management server IP addresses, most of that are positioned in China.
CERT-UA notes that PurpleFox’s elimination is difficult attributable to its use of a rootkit, however there are nonetheless efficient strategies that may assist detect and uproot the malware.
First, to find PurpleFox infections, customers are really helpful to do the next:
- Study community connections to “excessive” (10000+) ports utilizing the IP handle record within the report’s appendix.
- Use regedit.exe to test for the next registry values:
- WindowsXP: HKEY_LOCAL_MACHINEControlSet001ServicesAC0[0-9]
- Windows7: HKEY_LOCAL_MACHINESoftwareMicrosoftDirectPlay8Direct3D
- Analyze “Utility” log in Occasion Viewer for occasion IDs 1040 and 1042, supply: “MsiInstaller”
- Test “C:Program Information” for folders with random names, e.g., “C:Program FilesdvhvA”
- Confirm the persistent execution of the malware, which makes use of companies and shops information in particular directories, impeded by a rootkit from detection/elimination. Key areas are:
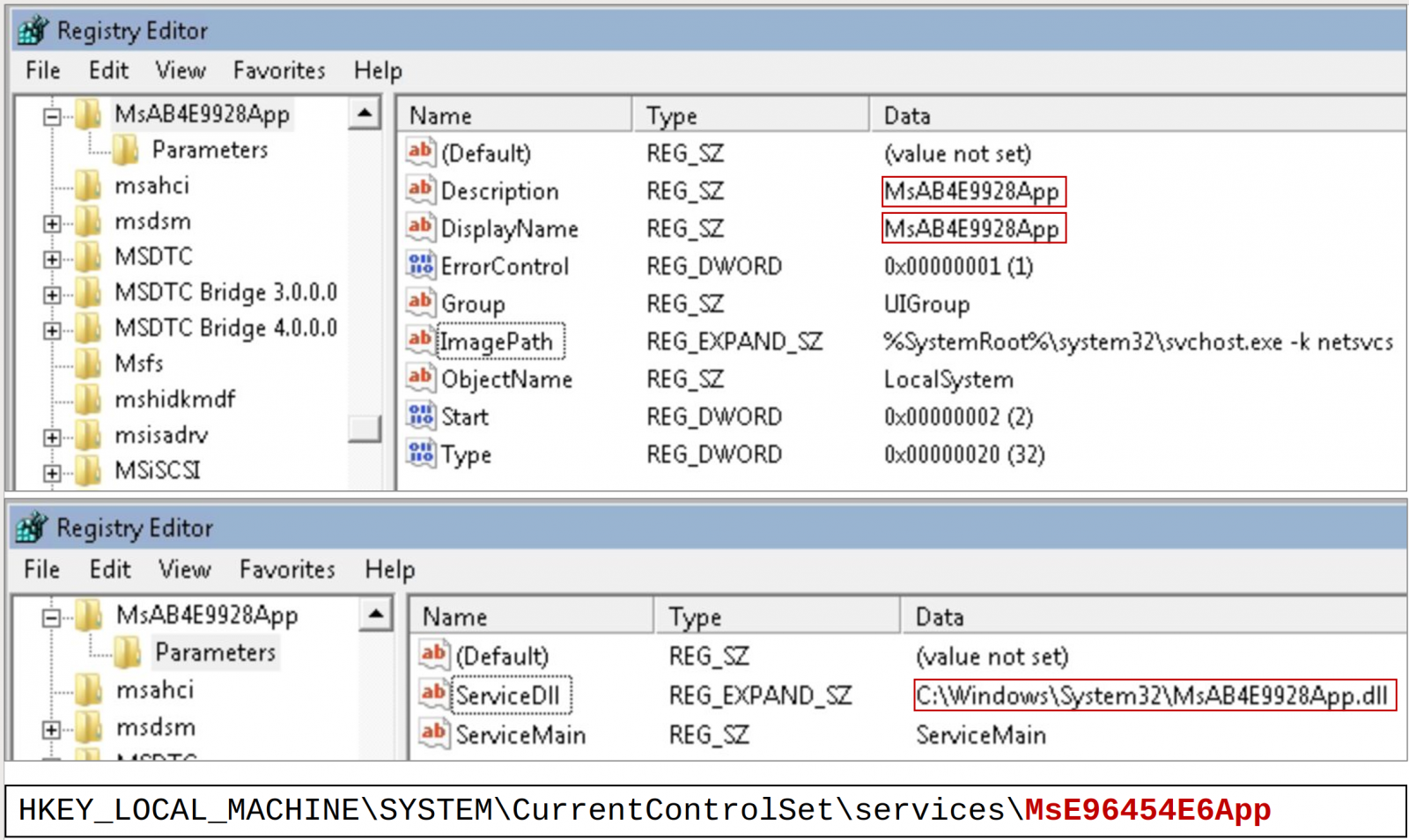
- HKEY_LOCAL_MACHINESystemControlSet001servicesMsXXXXXXXXApp
- C:WindowsSystem32MsXXXXXXXXApp.dll
- C:WindowsAppPatchDBXXXXXXXXMK.sdb, RCXXXXXXXXMS.sdb, TKXXXXXXXXMS.sdb
- (the place XXXXXXXX is a random [A-F0-9]{8} sequence, e.g., “MsBA4B6B3AApp.dll”)
If any of the above signifies PurpleFox an infection, CERT-UA suggests both utilizing Avast Free AV to run a “SMART” scan and distant all modules or carry out the next steps:
- Boot from LiveUSB or join the contaminated drive to a different pc
- Manually delete “MsXXXXXXXXApp.dll” and “.sdb” modules
- Boot usually and take away the service from the registry
For disk operations:
- Use lsblk and fdisk -lu /dev/sda to determine partitions
- Mount the system partition in read-write mode: mount -orw,offset=$((512*206848)) /dev/sda /mnt/
- Search and take away information in /mnt/Home windows/AppPatch and /mnt/Home windows/System32 (e.g., ls -lat /mnt/Home windows/AppPatch/ and rm -rf /mnt/Home windows/AppPatch/RC2EE39E00MS.sdb)
- Unmount with umount /mnt/
After cleansing, to keep away from re-infection from PurpleFox, which could be very seemingly if there are nonetheless contaminated machines on the identical community, allow the firewall on Home windows and create a rule to dam incoming site visitors from ports 135, 137, 139, and 445.


