
Roughly 38% of purposes utilizing the Apache Log4j library are utilizing a model weak to safety points, together with Log4Shell, a essential vulnerability recognized as CVE-2021-44228 that carries the utmost severity score, regardless of patches being out there for greater than two years.
Log4Shell is an unauthenticated distant code execution (RCE) flaw that permits taking full management over programs with Log4j 2.0-beta9 and as much as 2.15.0.
The flaw was found as an actively exploited zero-day on December 10, 2021, and its widespread impression, ease of exploitation, and large safety implications acted as an open invitation to menace actors.
The circumstance prompted an intensive marketing campaign to inform affected challenge maintainers and system directors, however regardless of quite a few warnings, a major variety of organizations continued to make use of weak variations lengthy after patches turned out there.
Two years after the vulnerability was disclosed and fixes have been launched, there are many targets nonetheless weak to Log4Shell.
A report from utility safety firm Veracode, based mostly on information collected between August 15 and November 15, highlights that previous issues can persist for an intensive intervals.
Solidified assault floor
Veracode gathered information for 90 days from 3,866 organizations that use 38,278 purposes counting on Log4j with variations between 1.1 and three.0.0-alpha1.
Of these apps, 2.8% use Log4J variants 2.0-beta9 via 2.15.0, that are straight weak to Log4Shell .
One other 3.8% use Log4j 2.17.0, which, though not weak to Log4Shell, is inclined to CVE-2021-44832, a distant code execution flaw that was fastened in model 2.17.1 of the framework.
Lastly, 32% are utilizing Log4j model 1.2.x, which has reached the top of assist since August 2015. These variations are weak to a number of extreme vulnerabilities revealed till 2022, together with CVE-2022-23307, CVE-2022-23305, and CVE-2022-23302.
In complete, Veracode discovered that about 38% of the apps inside its visibility use an insecure Log4j model.
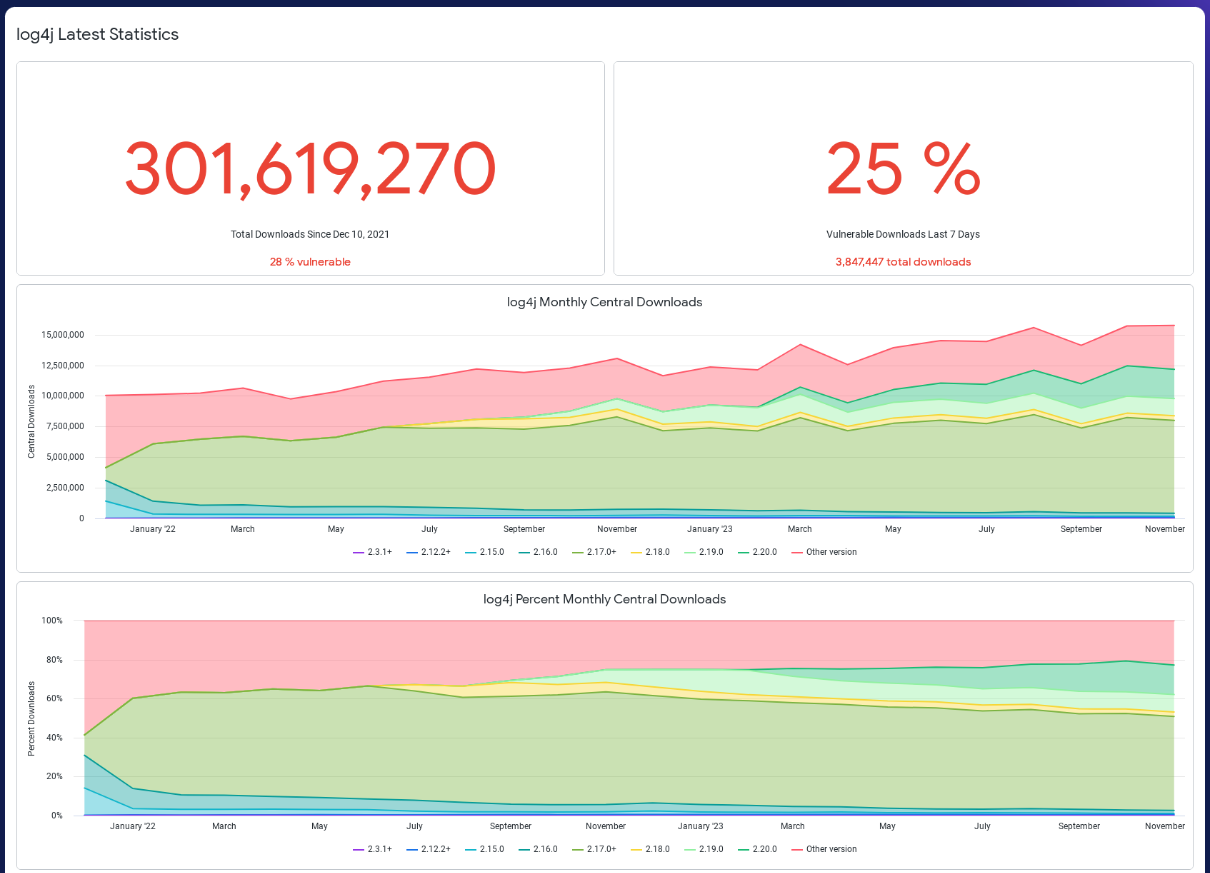
That is near what software program provide chain administration specialists at Sonatype report on their Log4j dashboard, the place 25% of the library’s downloads previously week concern weak variations.
Unhealthy safety practices
The continuous use of outdated library variations signifies an ongoing drawback, which Veracode attributes to builders desirous to keep away from pointless issues.
In keeping with Veracode’s findings, 79% of builders decide by no means to replace third-party libraries after their preliminary inclusion of their code base to keep away from breaking performance.
That is true even when 65% of open-source library updates include minor modifications and fixes unlikely to trigger purposeful issues.
Furthermore, the examine confirmed that it takes 50% of initiatives over 65 days to deal with high-severity flaws. It takes 13.7 instances longer than common to repair half of what’s of their backlog when understaffed and over seven months to deal with 50% of it when missing info.
Sadly, Veracode’s information reveals that Log4Shell has not been the wake-up name many within the safety business hoped it will be.
As a substitute, Log4j alone continues to be a supply of danger in 1 out of three circumstances and will very simply be one of many a number of methods attackers can leverage to compromise a given goal.
The advice for firms is to scan their surroundings, discover the variations of open-source libraries in use, after which develop an emergency improve plan for all of them.


