Authored by Dexter Shin
MoqHao is a well known Android malware household related to the Roaming Mantis risk actor group first found in 2015. McAfee Cellular Analysis Group has additionally posted a number of articles associated to this malware household that historically targets Asian nations similar to Korea and Japan.
Lately McAfee Cellular Analysis Group discovered that MoqHao started distributing variants utilizing very harmful method. Principally, the distribution methodology is similar. They ship a hyperlink to obtain the malicious app by way of the SMS message. Typical MoqHao requires customers to put in and launch the app to get their desired function, however this new variant requires no execution. Whereas the app is put in, their malicious exercise begins robotically. This system was launched in a earlier publish however the distinction is that this harmful method is now being abused by different well-known lively malware campaigns like MoqHao. Now we have already reported this system to Google and they’re already engaged on the implementation of mitigations to stop such a auto-execution in a future Android model. Android customers are at the moment protected by Google Play Defend, which is on by default on Android gadgets with Google Play Providers. Google Play Defend can warn customers or block apps identified to exhibit malicious conduct, even when these apps come from sources outdoors of Play. McAfee Cellular Safety detects this risk as Android/MoqHao.
How it’s distributed
MoqHao is distributed by way of phishing SMS messages (also referred to as Smishing). When a consumer receives an SMS message containing a malicious hyperlink and clicks it, the gadget downloads the malicious utility. Phishing messages are virtually the identical as in earlier campaigns:
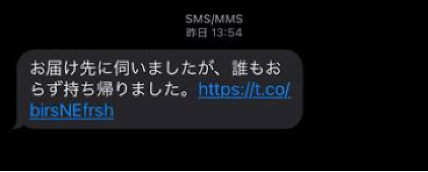
Determine 1. Smishing message impersonating a notification from a courier service.
Japanese message: I went to the supply deal with, however nobody was there. So, I introduced it again.
One noticeable change is that they now use URL shortener companies. If the malware authors use their very own area, it may be rapidly blocked but when they use authentic URL shortener companies, it’s tough to dam the brief area as a result of it might have an effect on all of the URLs utilized by that service. When a consumer clicks on the hyperlink within the message, will probably be redirected to the precise malicious web site by the URL shortener service.
What’s new on this variant
As talked about at first, this variant behaves otherwise from earlier ones. Typical MoqHao should be launched manually by the consumer after it’s put in however this variant launches robotically after set up with out consumer interplay:
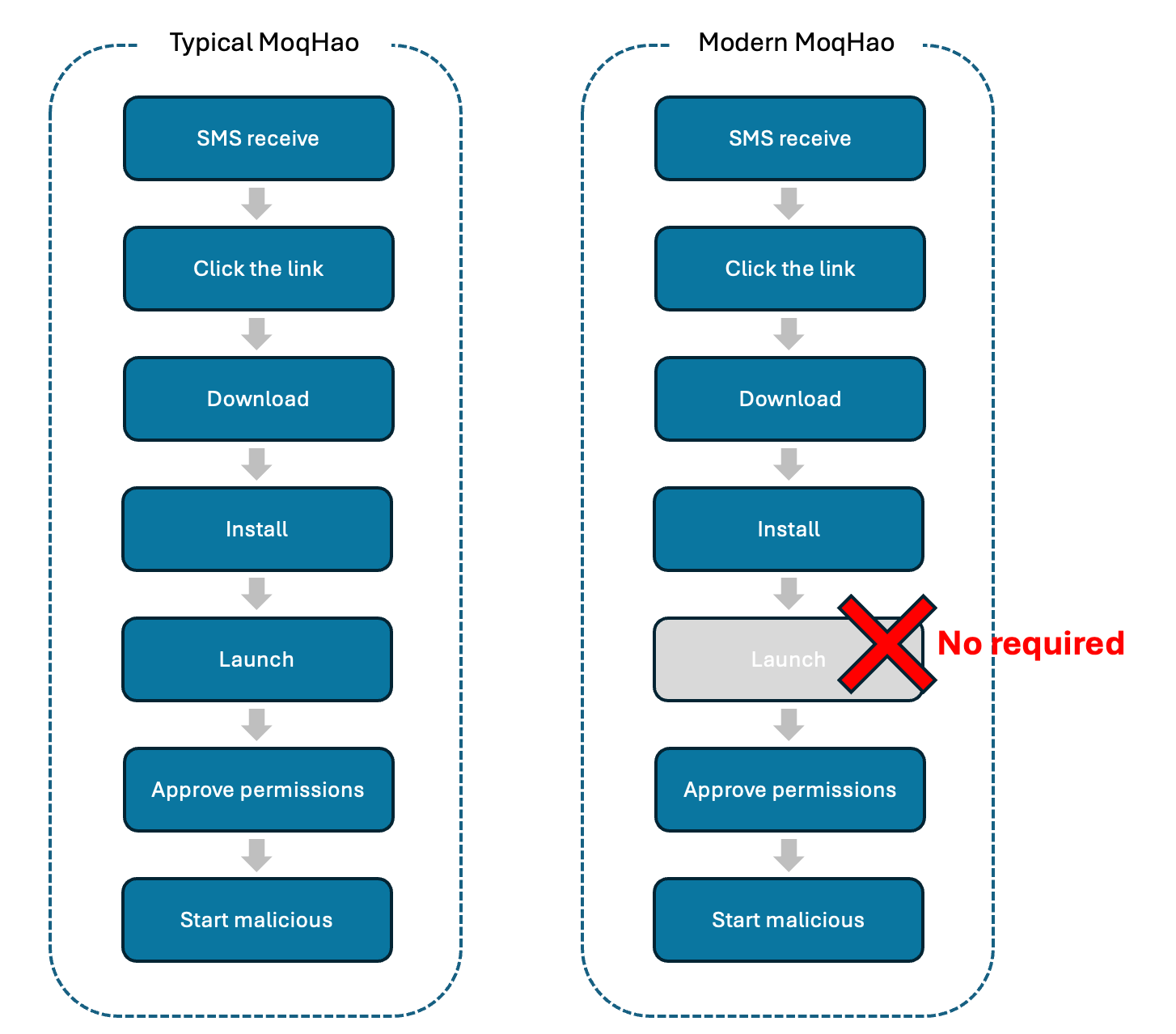
Determine 2. Variations between typical MoqHao and Trendy MoqHao
We defined this auto-execution method intimately in a earlier publish however to briefly summarize it right here, Android is designed so when an app is put in and a particular worth utilized by the app is about to be distinctive, the code runs to test whether or not the worth is exclusive upon set up. This function is the one that’s being abused by the extremely lively Trojan household MoqHao to auto-execute itself with out consumer interplay. The distribution, set up, and auto-execution of this latest MoqHao variant may be seen within the following video:
On the opposite hand, this latest MoqHao variant makes use of Unicode strings in app names otherwise than earlier than. This method makes some characters seem daring, however customers visually acknowledge it as “Chrome”. This may increasingly have an effect on app name-based detection methods that evaluate app title (Chrome) and package deal title (com.android.chrome):

Determine 3. App title utilizing Unicode strings.
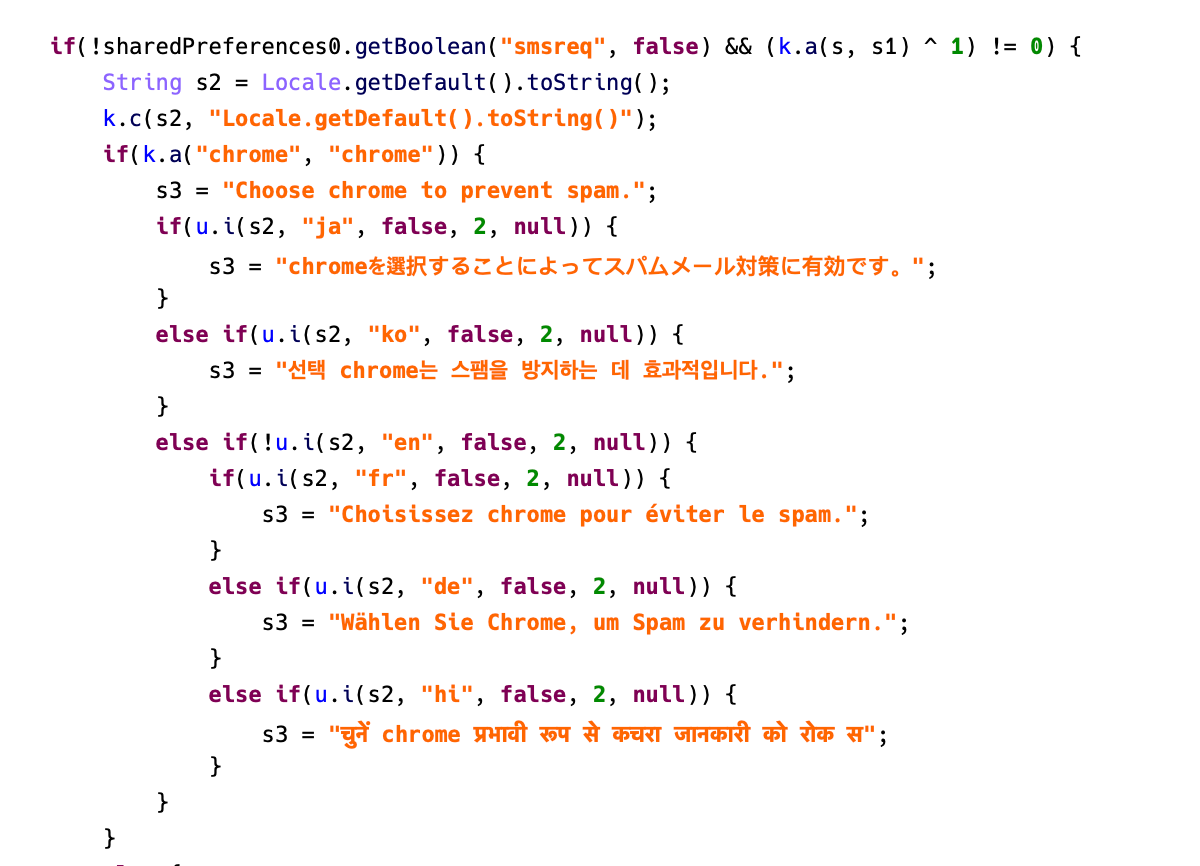
Moreover, additionally they use social engineering methods to set malicious apps because the default SMS app. Earlier than the settings window seems, they present a message telling you to arrange the app to stop spam, but this message is faux:

Determine 4. Pretend message utilizing social engineering methods.
Additionally, the completely different languages used within the textual content related to this conduct means that, along with Japan, they are additionally focusing on South Korea, France, Germany, and India:
Determine 5. Pretend messages designed to focus on completely different nations.
After the initialization of the malware is accomplished, it will create a notification channel that will likely be used to show phishing messages:
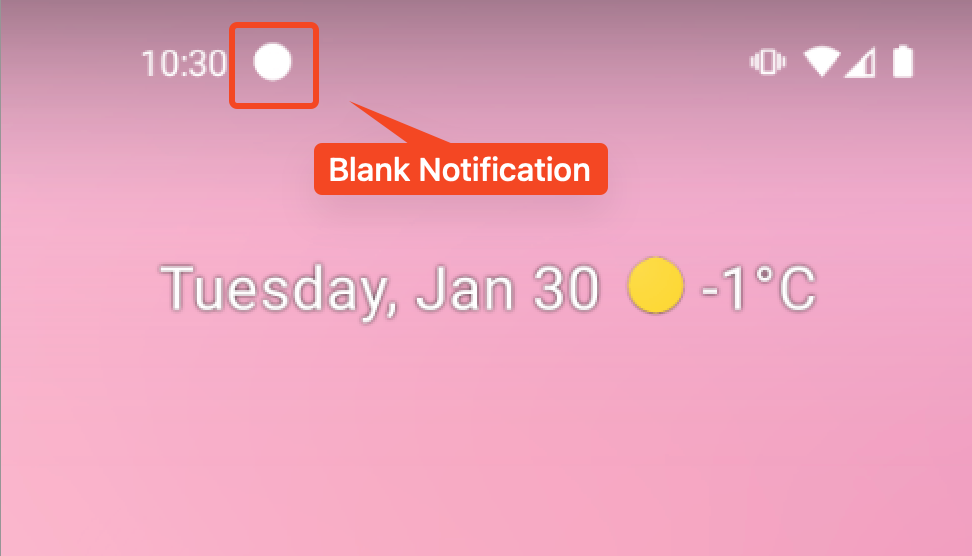
Determine 6. Create a notification channel for the subsequent phishing assault.
The malware checks the gadget’s provider and makes use of this notification to ship phishing messages accordingly to trick customers into click oning on them. MoqHao will get the phishing message and the phishing URL from Pinterest profiles.
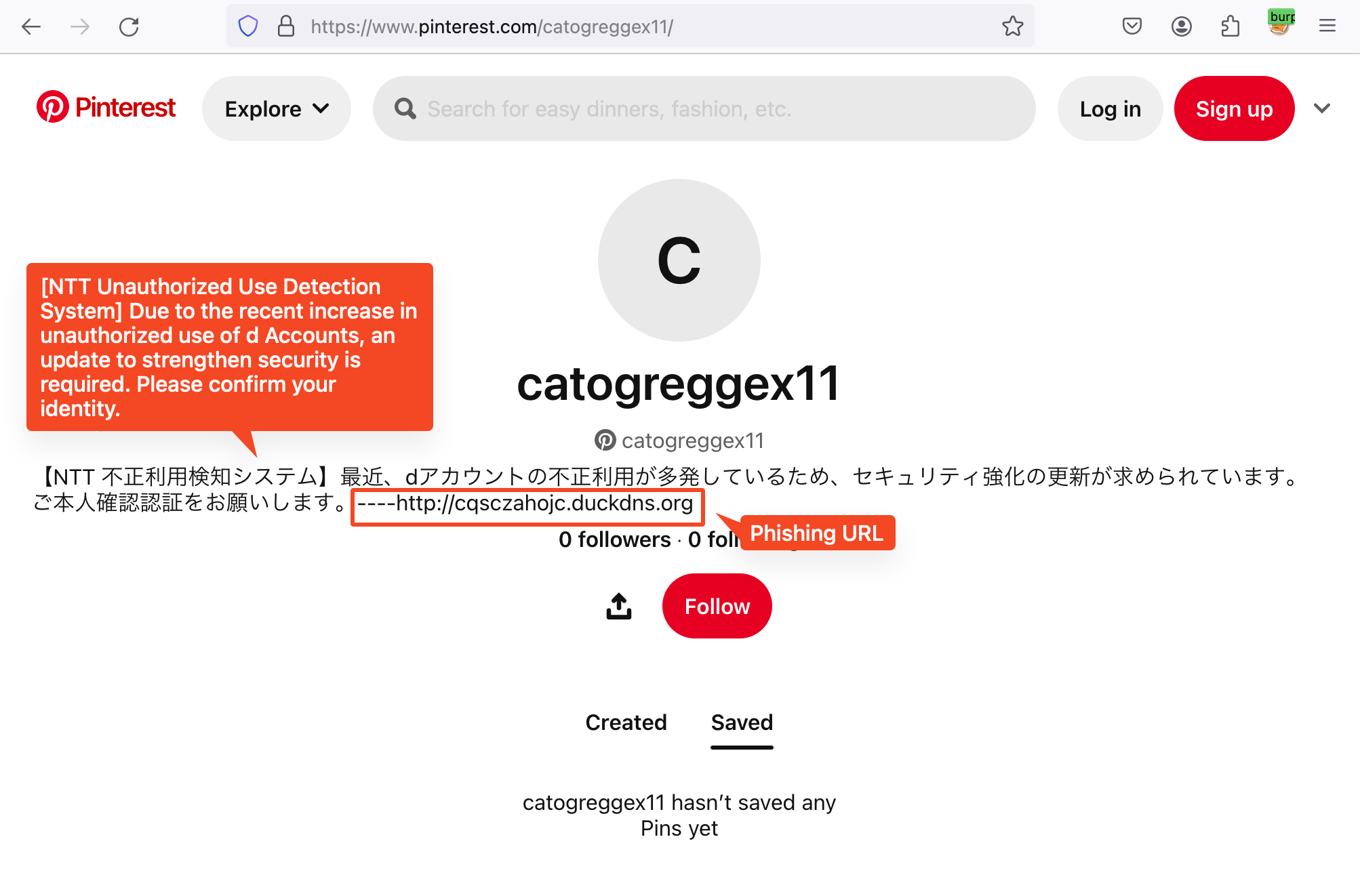
Determine 7. Phishing message and URL in Pinterest profile
If the phishing string is empty, MoqHao will use the phishing message within the code:
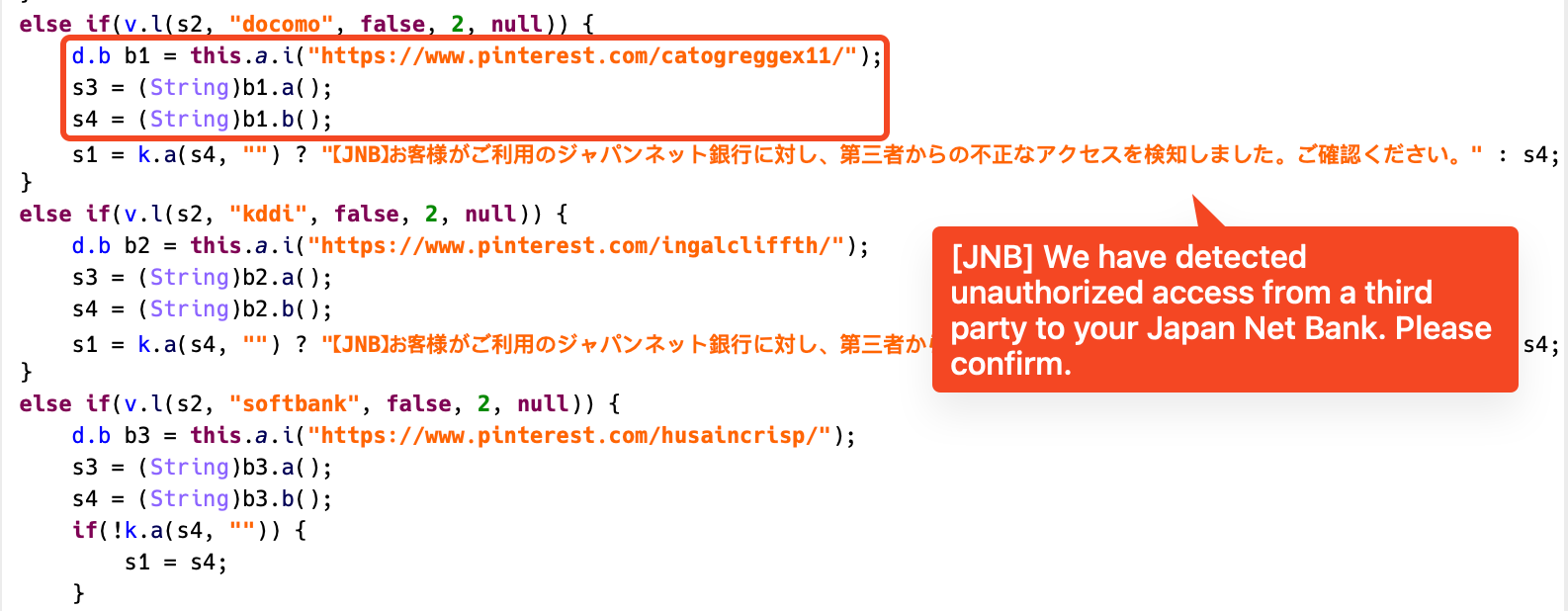
Determine 8. Phishing notification code for every provider
This variant additionally connects to the C2 server by way of WebSocket. Nonetheless, it has been confirmed that a number of different instructions have been added along with the instructions launched in the earlier publish:
| Command | Description |
| getSmsKW | Ship all SMS messages to C2 server |
| sendSms | Ship SMS messages to somebody |
| setWifi | Allow/disable Wifi |
| gcont | Ship complete contacts to C2 server |
| lock | Retailer Boolean worth in “lock” key in SharedPreferences |
| bc | Verify SIM state |
| setForward | Retailer String worth in “fs” key in SharedPreferences |
| getForward | Get String worth in “fs” key in SharedPreferences |
| hasPkg | Verify particular package deal put in on gadget |
| setRingerMode | Set Sound/Vibrate/Silent mode |
| setRecEnable | Set Vibrate/Silent mode in response to SDK model |
| reqState | Ship gadget data (Community, Energy, MAC, Permission) to C2 server |
| showHome | Emulate Dwelling button click on |
| getnpki | Ship Korean Public Certificates (NPKI) to C2 server |
| http | Ship HTTP requests |
| name | Name a particular quantity with Silent mode |
| get_apps | Get listing of put in packages |
| ping | Verify C2 server standing |
| getPhoneState | Get distinctive data similar to IMEI, SIM quantity, Android ID, and serial quantity |
| get_photo | Ship all images to C2 server |
MoqHao malware household is an lively malware that has been round for years. Though a few years have handed, they’re utilizing increasingly more other ways to cover and attain customers. We’re seeing a a lot larger variety of C2 instructions than in earlier, the lively use of authentic websites like Pinterest to retailer and replace phishing knowledge, and code with the potential to focus on Asian nations like Japan and South Korea, in addition to nations like France, Germany, and India. Furthermore, we count on this new variant to be extremely impactful as a result of it infects gadgets just by being put in with out execution.
It’s tough for basic customers to seek out faux apps utilizing authentic icons and utility names, so we advocate customers to put in safe software program to guard their gadgets. For extra data, go to McAfee Cellular Safety.
Indicators of Compromise (IOCs)
| SHA256 | Utility Title | Package deal Title |
| 2576a166d3b18eafc2e35a7de3e5549419d10ce62e0eeb24bad5a1daaa257528 | chom | gb.pi.xcxr.xd |
| 61b4cca67762a4cf31209056ea17b6fb212e175ca330015d804122ee6481688e | hm | malmkb.zdbd.ivakf.lrhrgf |
| b044804cf731cd7dd79000b7c6abce7b642402b275c1eb25712607fc1e5e3d2b | cm | vfqhqd.msk.xux.njs |
| bf102125a6fca5e96aed855b45bbed9aa0bc964198ce207f2e63a71487ad793a | chro | hohoj.vlcwu.lm.ext |
| e72f46f15e50ce7cee5c4c0c5a5277e8be4bb3dd23d08ea79e1deacb8f004136 | hroe | enech.hg.rrfy.wrlpp |
| f6323f8d8cfa4b5053c65f8c1862a8e6844b35b260f61735b3cf8d19990fef42 | chre | gqjoyp.cixq.zbh.llr |



