
A number of info stealers for the macOS platform have demonstrated the potential to evade detection even when safety firms observe and report about new variants continuously.
A report by SentinelOne highlights the issue by means of three notable malware examples that may evade macOS’s built-in anti-malware system, XProtect.
XProtect works within the background whereas scanning downloaded recordsdata and apps for identified malware signatures.
Regardless of Apple continuously updating the software’s malware database, SentinelOne says info-stealers bypass it nearly immediately due to the fast response of the malware authors.
Evading XProtect
The primary instance in SentinelOne’s report is KeySteal, a malware first documented in 2021, which has advanced considerably since then.
Presently, it’s distributed as an Xcode-built Mach-O binary, named ‘UnixProject’ or ‘ChatGPT,’ and makes an attempt to determine persistence and steal Keychain info.
Keychain is macOS’s native password administration system serving as a safe storage for credentials, non-public keys, certificates, and notes.
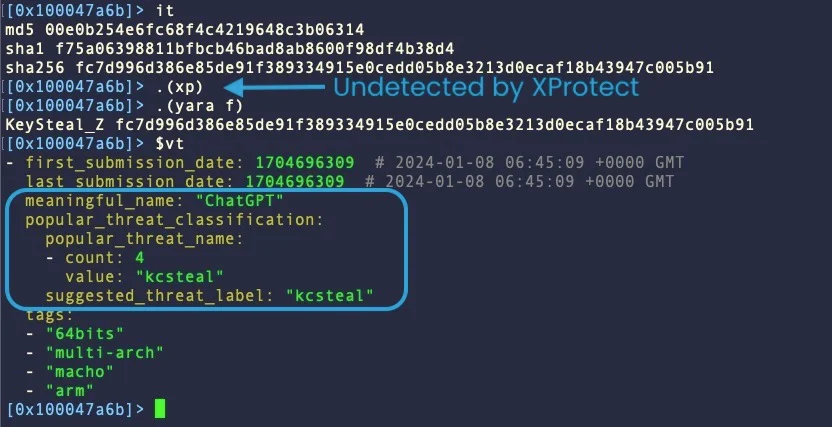
Apple final up to date its signature for KeySteal in February 2023, however the malware has obtained sufficient adjustments since then to go undetected by XProtect and most AV engines.
Its solely present weak spot is utilizing hardcoded command and management (C2) addresses, however SentinelOne believes it is solely a matter of time earlier than KeySteal’s creators implement a rotation mechanism.
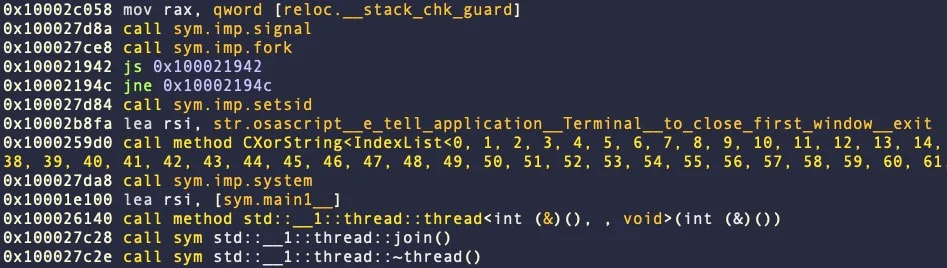
The subsequent malware highlighted for instance of evasion is Atomic Stealer, first documented by SentinelOne in Might 2023 as a brand new Go-based stealer and revisited by Malwarebytes in November 2023.
Apple final up to date XProtect’s signatures and detection guidelines this month, however SentinelOne experiences already observing C++ variants that may evade detection.
The most recent Atomic Stealer model has changed code obfuscation with cleartext AppleScript that exposes its data-stealing logic, contains anti-VM checks, and prevents executing the Terminal alongside it.
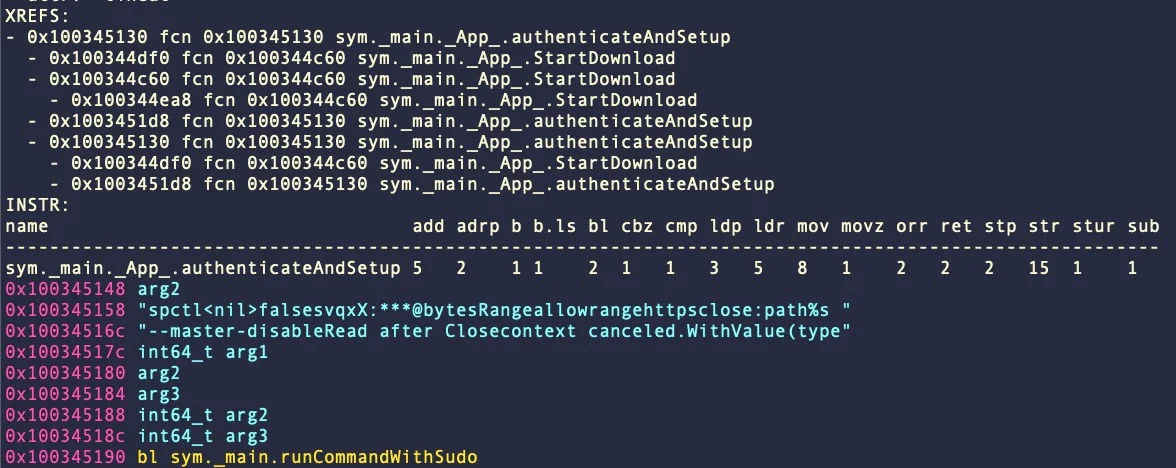
The third instance within the report is CherryPie, also called ‘Gary Stealer’ or ‘JaskaGo,’ first seen within the wild on September 9, 2023.
The Go-based cross-platform malware options anti-analysis and digital machine detection, Wails wrapping, advert hoc signatures, and a system that disables Gatekeeper utilizing admin privileges.
The excellent news is that Apple up to date its XProtect signatures for CherryPie in early December 2023, which work rather well even for newer iterations. Nevertheless, malware detections don’t fare as effectively on Virus Complete.
It turns into clear from the above that the continuous improvement of malware with the aim of evading detection makes this a dangerous recreation of whack-a-mole for customers and working system distributors alike.
Relying solely on static detection for safety is insufficient and probably dangerous. A extra sturdy method ought to incorporate antivirus software program outfitted with superior dynamic or heuristic evaluation capabilities.
Moreover, vigilant monitoring of community visitors, implementing firewalls, and constantly making use of the newest safety updates are important parts of a complete cybersecurity technique.


