
CISA warns {that a} important authentication bypass vulnerability in Ivanti’s Endpoint Supervisor Cellular (EPMM) and MobileIron Core gadget administration software program (patched in August 2023) is now beneath lively exploitation.
Tracked as CVE-2023-35082, the flaw is a distant unauthenticated API entry vulnerability affecting all variations of EPMM 11.10, 11.9, and 11.8 and MobileIron Core 11.7 and beneath,.
Profitable exploitation supplies attackers entry to personally identifiable data (PII) of cell gadget customers and may allow them to backdoor compromised servers when chaining the bug with different flaws.
“Ivanti has an RPM script out there now. We advocate prospects first improve to a supported model after which apply the RPM script,” the corporate stated in August. “Extra detailed data will be discovered on this Information Base articleon the Ivanti Group portal.”
Cybersecurity firm Rapid7, which found and reported the vulnerability, supplies indicators of compromise(IOCs) to assist admins detect indicators of a CVE-2023-35082 assault.
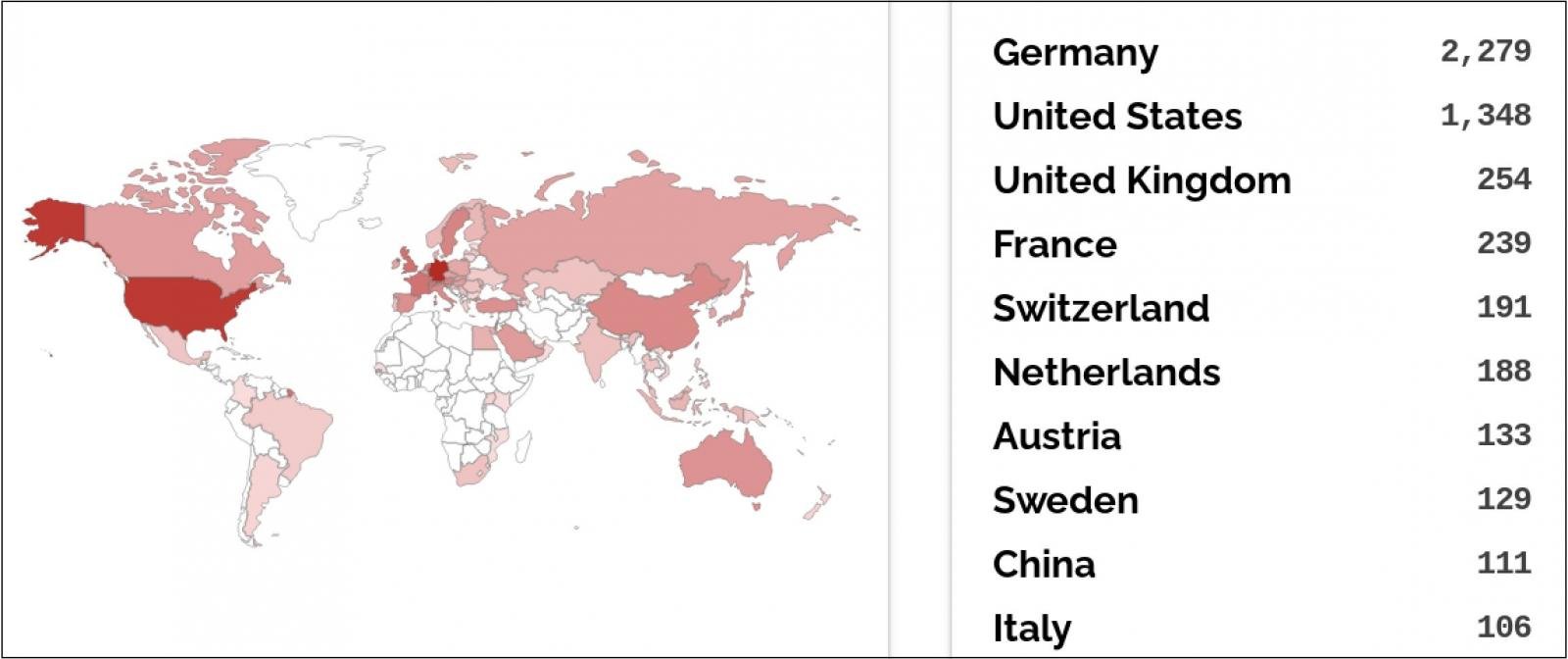
In keeping with Shodan, 6,300 Ivanti EPMM consumer portals are presently uncovered on-line, whereas the Shadowserver risk monitoring platform tracks 3,420 Web-exposed EPMM home equipment.
Shodan’s information additionally reveals that the greater than 150 cases linked to authorities companies worldwide will be straight accessed by way of the Web.
Whereas it has but to offer additional particulars on CVE-2023-35082 lively exploitation, CISA added the vulnerability to its Identified Exploited Vulnerabilities Catalog primarily based on proof of lively exploitation and says there isn’t any proof of abuse in ransomware assaults.
The cybersecurity company additionally ordered U.S. federal companies to patch it by February 2, as required by a binding operational directive (BOD 22-01) issued three years in the past.
Ivanti has but to replace its August advisories or subject one other notification warning that attackers are utilizing this safety vulnerability within the wild.
Two different Ivanti Join Safe (ICS) zero-days, an auth bypass (CVE-2023-46805) and a command injection (CVE-2024-21887) at the moment are additionally beneath mass exploitation by a number of risk teams, beginning January 11.
Victims compromised thus far vary from small companies to a number of Fortune 500 firms from numerous trade sectors, with the attackers having already backdoored over 1,700 ICS VPN home equipment utilizing a GIFTEDVISITOR webshell variant.
A number of different Ivanti zero-days (i.e., CVE-2021-22893, CVE-2023-35078, CVE-2023-35081, CVE-2023-38035) have been exploited in recent times to breach dozens of presidency, protection, and monetary organizations throughout the USA and Europe, a number of Norwegian authorities organizations, in addition to in focused assaults.


