
Have I Been Pwned has added nearly 71 million electronic mail addresses related to stolen accounts within the Naz.API dataset to its knowledge breach notification service.
The Naz.API dataset is an enormous assortment of 1 billion credentials compiled utilizing credential stuffing lists and knowledge stolen by information-stealing malware.
Credential stuffing lists are collections of login identify and password pairs stolen from earlier knowledge breaches which might be used to breach accounts on different websites.
Info-stealing malware makes an attempt to steal all kinds of knowledge from an contaminated pc, together with credentials saved in browsers, VPN shoppers, and FTP shoppers. The sort of malware additionally makes an attempt to steal SSH keys, bank cards, cookies, looking historical past, and cryptocurrency wallets.
The stolen knowledge is collected in textual content information and pictures, that are saved in archives referred to as “logs.” These logs are then uploaded to a distant server to be collected later by the attacker.
No matter how the credentials are stolen, they’re then used to breach accounts owned by the sufferer, offered to different risk actors on cybercrime marketplaces, or launched totally free on hacker boards to realize fame amongst the hacking neighborhood.
The Naz.API dataset
The Naz.API is a dataset allegedly containing over 1 billion strains of stolen credentials compiled from credential stuffing lists and from information-stealing malware logs. It ought to be famous that whereas the Naz.API dataset identify consists of the phrase “Naz,” it’s not associated to community connected storage (NAS) gadgets.
This dataset has been floating across the knowledge breach neighborhood for fairly some time however rose to notoriety after it was used to gas an open-source intelligence (OSINT) platform referred to as illicit.companies.
This service permits guests to look a database of stolen info, together with names, cellphone numbers, electronic mail addresses, and different private knowledge.
The service shut down in July 2023 out of considerations it was getting used for Doxxing and SIM-swapping assaults. Nonetheless, the operator enabled the service once more in September.
Illicit.companies use knowledge from varied sources, however one among its largest sources of knowledge got here from the Naz.API dataset, which was shared privately amongst a small variety of folks.
Every line within the Naz.API knowledge consists of a login URL, its login identify, and an related password stolen from an individual’s gadget, as proven under.
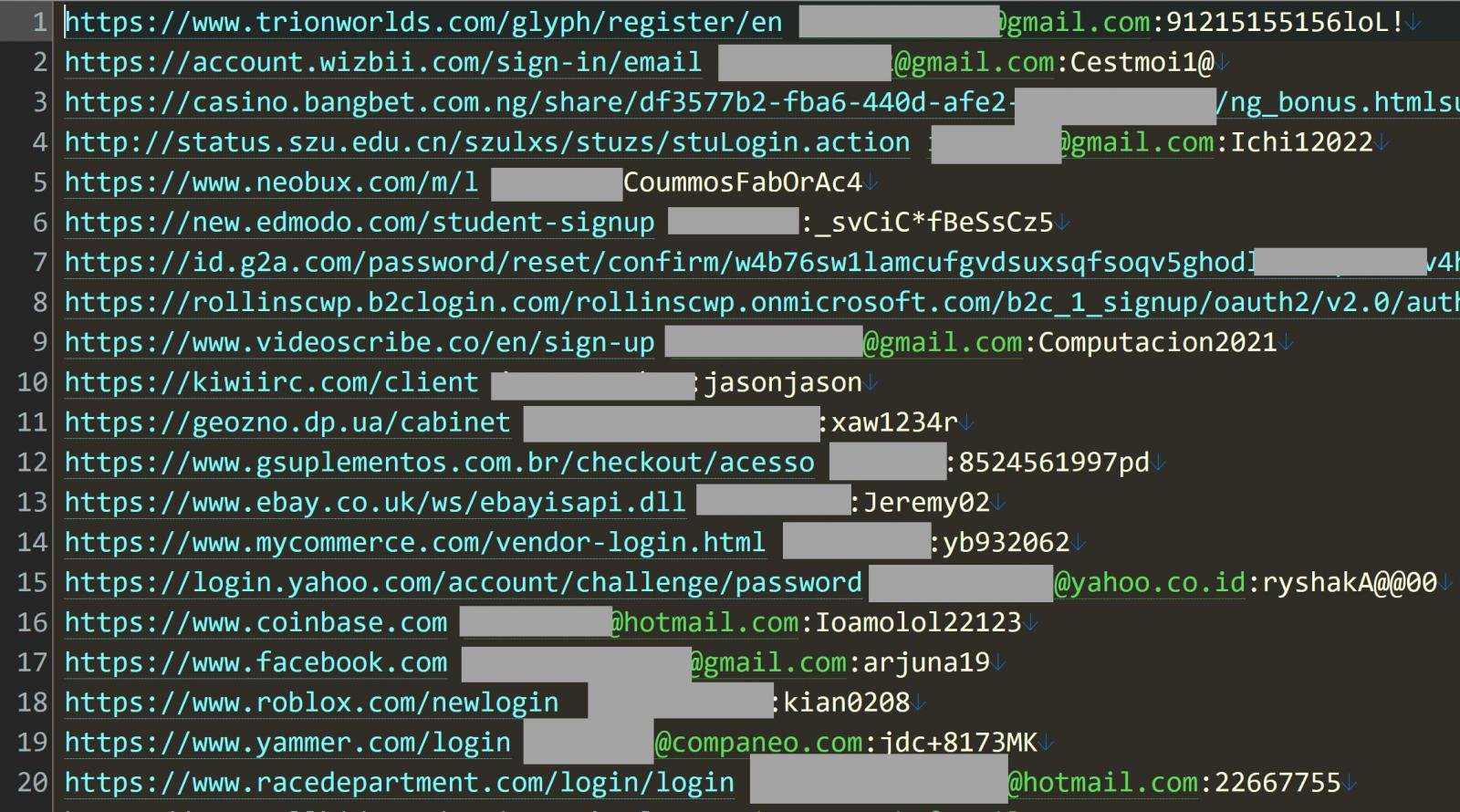
Supply: Troy Hunt
Naz.API added to HIBP
Right now, Troy Hunt, the creator of Have I Been Pwned, introduced he added the Naz.API dataset to his knowledge breach notification service after he obtained it from a widely known tech firm.
“Here is the again story: this week I used to be contacted by a widely known tech firm that had obtained a bug bounty submission primarily based on a credential stuffing checklist posted to a well-liked hacking discussion board,” defined a weblog submit by Hunt.
“While this submit dates again nearly 4 months, it hadn’t come throughout my radar till now and inevitably, additionally hadn’t been despatched to the aforementioned tech firm.”
“They took it critically sufficient to take applicable motion towards their (very sizeable) person base which gave me sufficient trigger to analyze it additional than your common cred stuffing checklist.”
Supply: BleepingComputer
Based on Hunt, the Naz.API dataset consists of 319 information totaling 104GB and containing 70,840,771 distinctive electronic mail addresses.
Nonetheless, whereas there are near 71 million distinctive emails, for every electronic mail deal with, there are doubtless many different information for the completely different websites’ credentials have been stolen from.
Hunt says the Naz.API knowledge is probably going outdated, because it contained one among his and different HIBP subscribers’ passwords that have been used previously. Hunt says his password was utilized in 2011, which means that a number of the knowledge is over 13 years outdated.
To examine in case your credentials are within the Naz.API dataset, you possibly can carry out a search at Have I Been Pwned. In case your electronic mail is discovered to be related to Naz.API, the positioning will warn you, indicating that your pc was contaminated with information-stealing malware at one level.
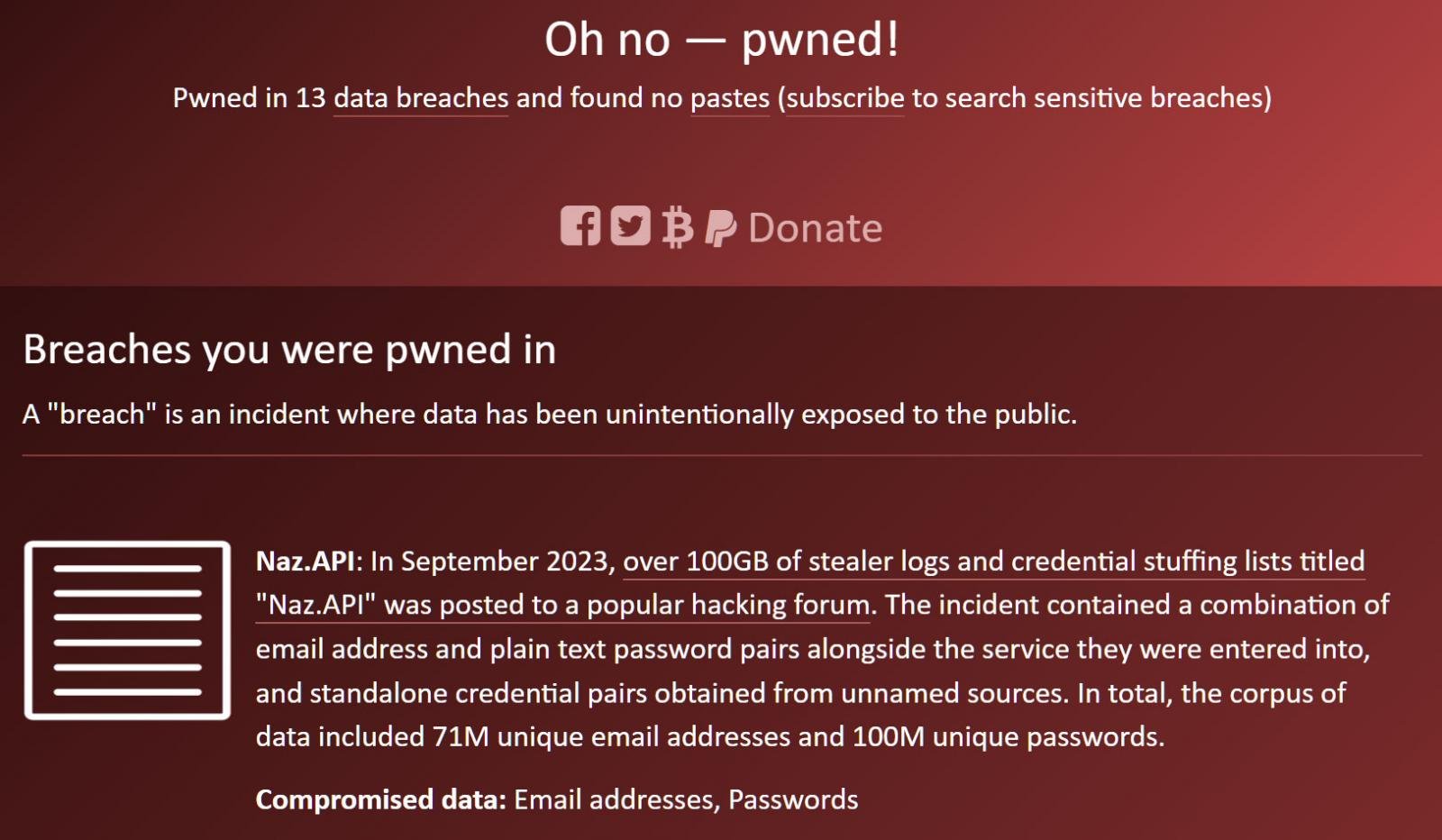
Source: BleepingComputer
Sadly, even when HIBP warns you that your electronic mail was within the Naz.API, it doesn’t inform you for what particular web site credentials have been stolen.
As this dataset is partially linked to information-stealing malware, it’s really helpful to vary passwords for all of your saved accounts.
This consists of passwords for company VPNs, electronic mail accounts, financial institution accounts, and another private accounts.
Moreover, as info-stealers try to steal cryptocurrency wallets, it’s best to instantly switch any crypto to a different pockets for those who personal any.
For extra detailed details about what accounts have been uncovered, you possibly can strive the Illicit.Companies web site, which is at the moment overwhelmed with everybody trying to make use of it.


