Generative AI can be utilized by attackers, however safety professionals should not lose sleep over it, in accordance with a Google Cloud risk intelligence analyst. Discover out why.
Google Cloud’s group just lately spoke about probably the most notable cybersecurity threats of 2023 — multi-faceted extortion and zero-day exploitation — and predicted extra zero-day assaults in 2024, throughout two public, digital classes. Plus, Google predicts that each attackers and defenders will proceed to make use of generative AI. Nonetheless, generative AI most likely received’t create its personal malware in 2024.
Soar to:
Two most notable cybersecurity threats of 2023
The 2 most notable cybersecurity threats of 2023, in accordance with Google Cloud’s Luke McNamara, principal belief and security analyst, have been multi-faceted extortion (also referred to as double extortion) and zero-day exploitation.
Multi-faceted exploitation
Multi-faceted exploitation contains ransomware and information theft, though the variety of ransomware assaults tracked by Google Cloud fell in 2023. The most typical ransomware households utilized in multi-faceted exploitation assaults have been LockBit, Clop and ALPHV.
Most ransomware assaults initially stemmed from stolen credentials. Brute power assaults and phishing have been the subsequent commonest preliminary an infection vectors for ransomware.
SEE: Know the warning indicators if another person has accessed your Google account. (TechRepublic)
Attackers more and more put stolen credentials up on the market on information leak websites, McNamara stated. “This previous quarter (Q3 2023) we noticed the very best variety of postings to DLS websites since we began monitoring this in 2020,” McNamara stated.
Many attackers are industry-agnostic, however “Quarter over quarter, manufacturing appears to be significantly hit and impacted disproportionately,” McNamara stated. “That’s the place we’re seeing quite a lot of the exercise by way of quantity.”
Zero-day exploitation
Zero-day exploitation is outlined by Google Cloud as vulnerabilities with no identified patches that risk actors are actively exploiting. In 2023, Google Cloud Safety tracked 89 such assaults (Determine A), surpassing the earlier excessive of 2021.
Determine A
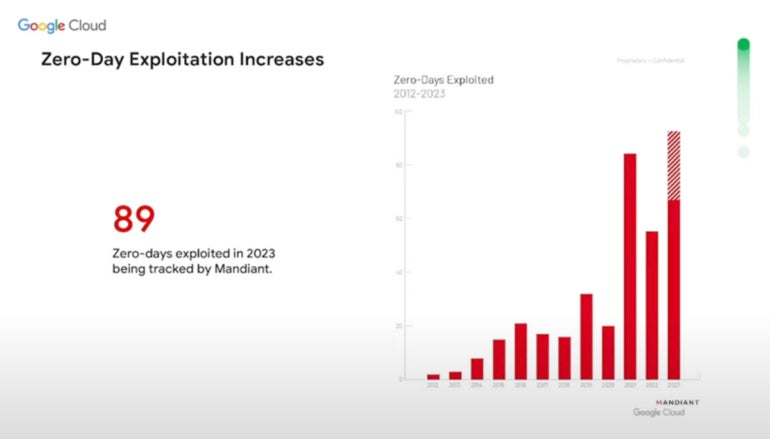
Many zero-day threats are nation-state affiliated or sponsored. The second commonest motivation amongst risk actors utilizing zero-day threats is to accumulate cash.
SEE: What the Cisco Talos 12 months in Overview report revealed (TechRepublic)
Google Cloud’s 2024 cybersecurity forecast
Andrew Kopcienski, principal risk intelligence analyst at Google’s Mandiant Communication Middle, talked about nation-state risk actors, zero-day assaults, motion between cloud environments and credential theft throughout his presentation about cyber threats in 2024. Particularly, China and Russia are specializing in zero-day assaults, he stated.
“We absolutely anticipate to see much more zero day use in 2024 by not simply nation-state sponsored attackers however cyber criminals as effectively,” stated Kopcienski. “Zero days are top-of-the-line strategies attackers have to stay undetected as soon as they get right into a community.”
China-sponsored risk actors
China-sponsored actors have targeted on growing capabilities find and utilizing zero days and botnets to stay undetected, Kopcienski stated. Google Cloud expects China’s cyber risk efforts to give attention to high-tech fields like chip growth.
Russian-sponsored espionage
Russian espionage targeted on Ukraine has been an issue, he stated. Google Cloud discovered Russia has performed campaigns outdoors Ukraine as effectively, however these principally give attention to gaining strategic info concerning Ukraine, Kopcienski stated. Russian-sponsored attackers use “dwelling off the land” assaults that don’t require malware; as a substitute, they abuse native capabilities, and their site visitors appears like native site visitors. Google Cloud expects extra assaults from Russian-backed actors in 2024, principally targeted on victims inside Ukraine or associated to Ukraine.
North Korean-sponsored risk actors
Google Cloud additionally appeared carefully at nation-state actors related to North Korea.
“They’ve developed a scrappy functionality to launch software program provide chain assaults,” Kopcienski stated.
North Korea was the primary identified nation-state actor to make use of “cascading” software program provide chain assaults, which piggybacked off one another. Many of those assaults are about stealing cryptocurrency or corporations conducting cryptocurrency operations. Google Cloud expects to see North Korea-affiliated risk actors’ assaults broaden in 2024.
Credential theft and extortion
One other concern for 2024 is extortion. “Credential theft (Determine B) is the secret … that has change into probably the most drastic and hottest measure quite a lot of these attackers are utilizing,” Kopcienski stated.
Determine B
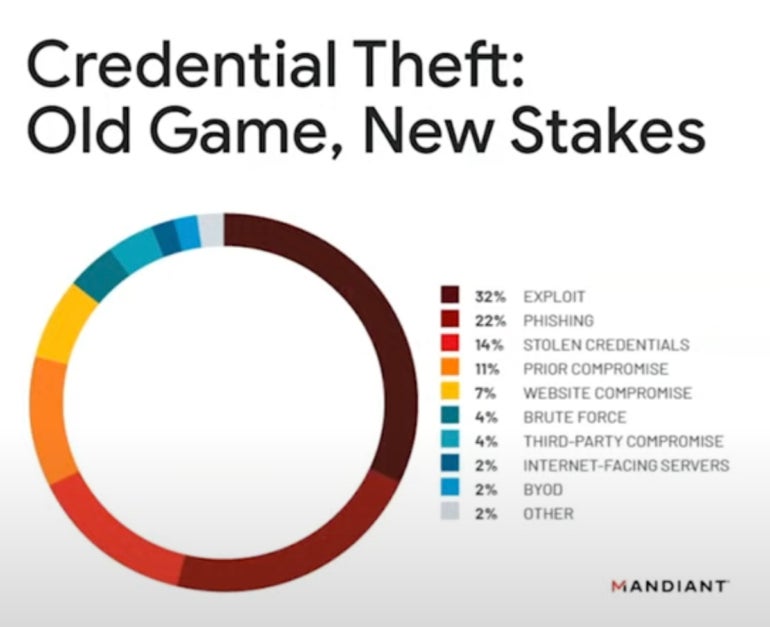
“Into 2024, we anticipate to see a give attention to information leak websites, particularly by extortion actors,” he stated.
Motion between cloud environments
Attackers in 2024 could use techniques, strategies and procedures that permit them to journey throughout completely different cloud environments, seemingly because of the growing use of cloud and hybrid environments.
How generative AI has and can have an effect on cybersecurity in 2023 and 2024
Attackers can use generative AI to create textual content, voice messages and imagery, and Google Cloud expects this to change into extra widespread.
“AI is enabling explicit sorts of malicious attackers, principally in disinformation campaigns. We’re very involved going into subsequent yr in regards to the influence of disinformation that has been augmented by AI, particularly with regards to the 2024 election,” stated Kopcienski.
In 2023, generative AI has been utilized by attackers and defenders. In 2024, AI could also be used to extend the size of assaults, reminiscent of by adopting AI in name facilities operating ransomware negotiations.
Generative AI would possibly be capable to create malware in some unspecified time in the future sooner or later, however Kopcuenski stated to not anticipate that to occur as quickly as 2024. He recommends cybersecurity professionals “stay grounded” and never lose sleep with regards to generative AI. A lot of its threats are “hypothetical,” he stated.
“There’s quite a lot of hype and disinformation on the market already about what AI can and might’t do. … (AI is) not an awesome revolution by way of the threats being posed,” he stated.



