
Exploit code is now accessible for a important authentication bypass vulnerability in Fortra’s GoAnywhere MFT (Managed File Switch) software program that enables attackers to create new admin customers on unpatched cases by way of the administration portal.
GoAnywhere MFT is a web-based managed file switch device that helps organizations switch information securely with companions and hold audit logs of who accessed all shared information.
Whereas Fortra silently patched the bug (CVE-2024-0204) on December 7 with the discharge of GoAnywhere MFT 7.4.1, the corporate solely publicly disclosed it at present in an advisory providing restricted info (extra particulars can be found in a personal buyer advisory).
Nevertheless, Fortra additionally issued personal advisories to prospects on December 4 earlier than fixing the flaw, urging them to safe their MFT companies to maintain their information protected.
Admins who have not but and may’t instantly improve to the final model are suggested to take away the assault vector by:
- Deleting the InitialAccountSetup.xhtml file within the set up listing and restarting the companies.
- Changing the InitialAccountSetup.xhtml file with an empty file and restarting the companies.
The corporate advised BleepingComputer on Tuesday that there have been no reviews of assaults exploiting this vulnerability.
As we speak, nearly seven weeks later, safety researchers with Horizon3’s Assault Workforce revealed a technical evaluation of the vulnerability and shared a proof-of-concept (PoC) exploit that helps create new admin customers on weak GoAnywhere MFT cases uncovered on-line.
Their exploit takes benefit of the trail traversal subject on the root of CVE-2024-0204 to entry the weak /InitialAccountSetup.xhtml endpoint and begin the preliminary account setup display (that should not be accessible after the server’s setup course of) to create a brand new administrator account.
“The best indicator of compromise that may be analyzed is for any new additions to the ‘Admin customers’ group within the GoAnywhere administrator portal Customers -> Admin Customers part,” stated Zach Hanley, Chief Assault Engineer at Horizon3.
“If the attacker has left this person right here you might be able to observe its final logon exercise right here to gauge an approximate date of compromise.”
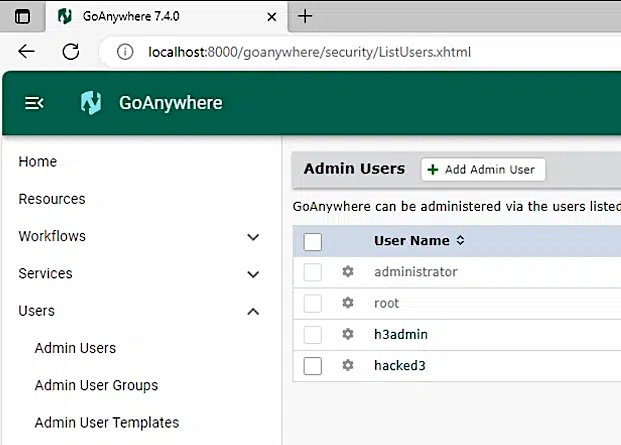
Nevertheless, now that Horizon3 has launched a PoC exploit, it is very seemingly that risk actors will begin scanning for and compromise all GoAnywhere MFT cases left unpatched.
Clop’s GoAnywhere MFT breach marketing campaign
The Clop ransomware gang breached over 100 organizations by exploiting a important distant code execution flaw (CVE-2023-0669) within the GoAnywhere MFT software program.
Clop’s assaults started on January 18, 2023, and Fortra found that the flaw was being weaponized to breach its prospects’ safe file servers on February 3.
The checklist of victims who got here ahead after being breached and extorted by Clop consists of however just isn’t restricted to healthcare large Neighborhood Well being Programs (CHS), Client items large Procter & Gamble, cybersecurity agency Rubrik, Hitachi Vitality, fintech platform Hatch Financial institution, luxurious model retailer Saks Fifth Avenue, and the Metropolis of Toronto, Canada.
Clop’s involvement in final 12 months’s information theft marketing campaign is a part of a much wider sample of concentrating on MFT platforms lately.
Different cases embrace the breach of Accellion FTA servers in December 2020, SolarWinds Serv-U servers in 2021, and the widespread exploitation of MOVEit Switch servers beginning June 2023.


