At Microsoft, we proceed to search for inventive methods to guard individuals on-line and that features having no tolerance for many who create fraudulent copies of our merchandise to hurt others. Fraudulent on-line accounts act because the gateway to a bunch of cybercrime, together with mass phishing, identification theft and fraud, and distributed denial of service (DDoS) assaults. That’s the reason at the moment, we, with worthwhile menace intelligence insights from Arkose Labs, a number one cybersecurity protection and bot administration vendor, are going after the primary vendor and creator of fraudulent Microsoft accounts, a bunch we name Storm-1152. We’re sending a robust message to those that search to create, promote or distribute fraudulent Microsoft merchandise for cybercrime: We’re watching, taking discover and can act to guard our clients.
Storm-1152 runs illicit web sites and social media pages, promoting fraudulent Microsoft accounts and instruments to bypass identification verification software program throughout well-known know-how platforms. These providers scale back the effort and time wanted for criminals to conduct a bunch of legal and abusive behaviors on-line. Thus far, Storm-1152 created on the market roughly 750 million fraudulent Microsoft accounts, incomes the group thousands and thousands of {dollars} in illicit income, and costing Microsoft and different firms much more to fight their legal exercise.
With at the moment’s motion, our purpose is to discourage legal conduct. By searching for to sluggish the pace at which cybercriminals launch their assaults, we purpose to lift their price of doing enterprise whereas persevering with our investigation and defending our clients and different on-line customers.
How cybercriminals use Storm-1152’s providers
Storm-1152 performs a big function within the extremely specialised cybercrime-as-a-service ecosystem. Cybercriminals want fraudulent accounts to help their largely automated legal actions. With firms in a position to rapidly determine and shut down fraudulent accounts, criminals require a larger amount of accounts to bypass mitigation efforts. As an alternative of spending time making an attempt to create 1000’s of fraudulent accounts, cybercriminals can merely buy them from Storm-1152 and different teams. This permits criminals to focus their efforts on their final targets of phishing, spamming, ransomware, and different sorts of fraud and abuse. Storm-1152 and teams like them allow scores of cybercriminals to hold out their malicious actions extra effectively and successfully.
Microsoft Menace Intelligence has recognized a number of teams engaged in ransomware, knowledge theft and extortion which have used Storm-1152 accounts. For instance, Octo Tempest, often known as Scattered Spider, obtained fraudulent Microsoft accounts from Storm-1152. Octo Tempest is a financially motivated cybercrime group that leverages broad social engineering campaigns to compromise organizations throughout the globe with the purpose of economic extortion. Microsoft continues to trace a number of different ransomware or extortion menace actors which have bought fraudulent accounts from Storm-1152 to reinforce their assaults, together with Storm-0252 and Storm-0455.
Our disruption technique
On Thursday, December 7, Microsoft obtained a courtroom order from the Southern District of New York to grab U.S.-based infrastructure and take offline web sites utilized by Storm-1152 to hurt Microsoft clients. Whereas our case focuses on fraudulent Microsoft accounts, the web sites impacted additionally offered providers to bypass safety measures on different well-known know-how platforms. As we speak’s motion subsequently has a broader impression, benefiting customers past Microsoft. Particularly, Microsoft’s Digital Crimes Unit disrupted:
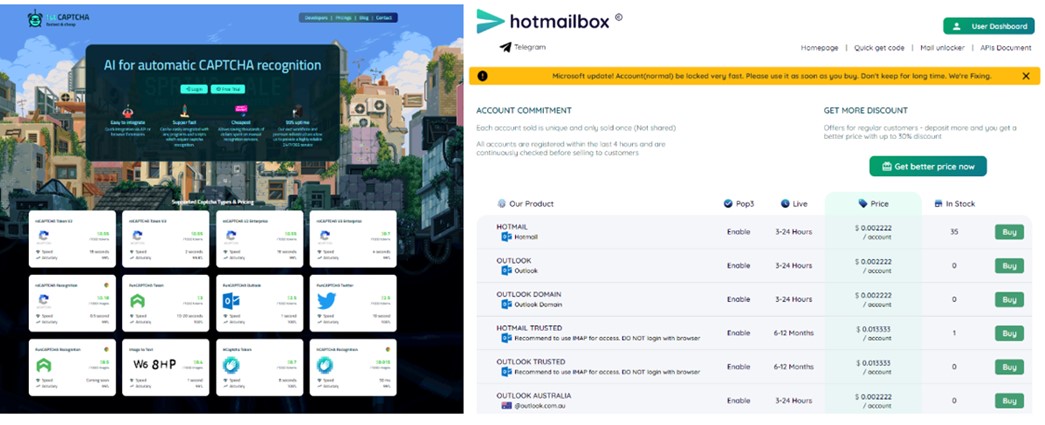
- Hotmailbox.me, a web site promoting fraudulent Microsoft Outlook accounts
- 1stCAPTCHA, AnyCAPTCHA, and NoneCAPTCHA, web sites that facilitate the tooling, infrastructure, and promoting of the CAPTCHA resolve service to bypass the affirmation of use and account setup by an actual individual. These websites offered identification verification bypass instruments for different know-how platforms
- The social media websites actively used to market these providers
Photos of Storm-1152’s illicit web sites
Microsoft is dedicated to offering a protected digital expertise for each individual and group on the planet. We work carefully with Arkose Labs to deploy a next-generation CAPTCHA protection resolution. The answer requires each would-be consumer who needs to open a Microsoft account to symbolize that they’re a human being (not a bot) and confirm the accuracy of that illustration by fixing varied sorts of challenges.
As founder and CEO of Arkose Labs, Kevin Gosschalk says: “Storm-1152 is a formidable foe established with the only objective of getting cash by empowering adversaries to commit advanced assaults. The group is distinguished by the truth that it constructed its CaaS enterprise within the mild of day versus on the darkish internet. Storm-1152 operated as a typical web going-concern, offering coaching for its instruments and even providing full buyer help. In actuality, Storm-1152 was an unlocked gateway to severe fraud.”
Storm-1152’s exercise not solely violates Microsoft’s phrases of providers by promoting fraudulent accounts, however it additionally purposely seeks to hurt clients of Arkose Labs and deceive victims pretending to be reputable customers in an try to bypass safety measures.
What guests to hotmailbox.com, 1stCAPTCHA, AnyCAPTCHA, and NoneCAPTCHA will see in the event that they attempt to entry the web sites
Figuring out the people and infrastructure behind Storm-1152
Our evaluation of Storm-1152’s exercise included detection, evaluation, telemetry, undercover take a look at purchases, and reverse engineering to pinpoint the malicious infrastructure hosted in the USA. Microsoft Menace Intelligence and Arkose Cyber Menace Intelligence Analysis unit (ACTIR) supplied extra knowledge and insights to strengthen our authorized case.
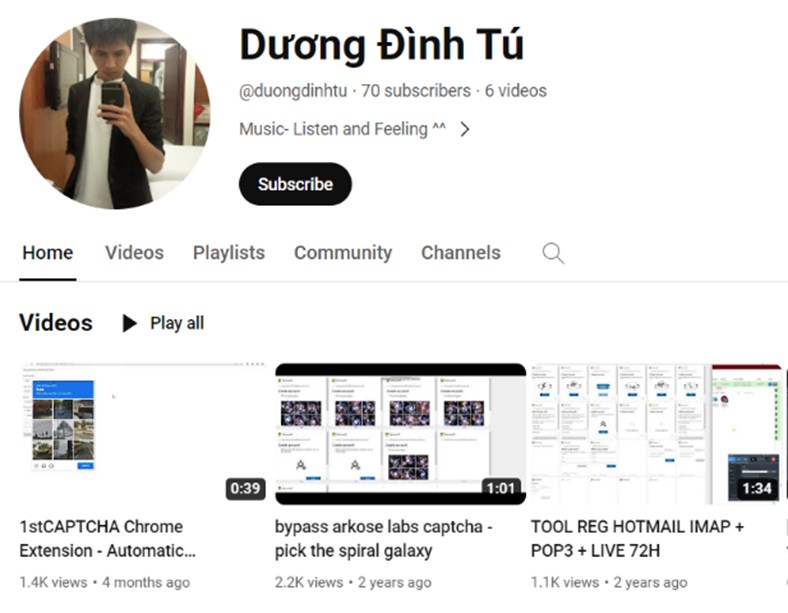
As a part of our investigation, we had been in a position to affirm the identification of the actors main Storm-1152’s operations – Duong Dinh Tu, Linh Van Nguyễn (often known as Nguyễn Van Linh), and Tai Van Nguyen – based mostly in Vietnam. Our findings present these people operated and wrote the code for the illicit web sites, revealed detailed step-by-step directions on how you can use their merchandise through video tutorials and supplied chat providers to help these utilizing their fraudulent providers.
Duong Dinh Tu’s YouTube channel with “how you can movies” to bypass safety measures
Microsoft has since submitted a legal referral to U.S. regulation enforcement. We’re grateful for our partnership with regulation enforcement who can convey these seeking to hurt our clients to justice.
Our ongoing dedication to preventing cybercrime
As we speak’s motion is a continuation of Microsoft’s technique of taking purpose on the broader cybercriminal ecosystem and focusing on the instruments cybercriminals use to launch their assaults. It builds on our enlargement of a authorized technique used efficiently to disrupt malware and nation-state operations. We’ve got additionally partnered with different organizations throughout the business to extend intelligence sharing on fraud and additional improve our synthetic intelligence and machine studying algorithms that rapidly detect and flag fraudulent accounts.
As we’ve stated earlier than, no disruption is full in in the future. Going after cybercrime requires persistence and ongoing vigilance to disrupt new malicious infrastructure. Whereas at the moment’s authorized motion will impression Storm-1152’s operations, we anticipate different menace actors will adapt their strategies consequently. Continued private and non-private sector collaboration, like todays with Arkose Labs and U.S. regulation enforcement, stay important if we wish to meaningfully dent the impression of cybercrime.