The Pc Emergency Response Workforce of Ukraine (CERT-UA) has warned that greater than 2,000 computer systems within the nation have been contaminated by a pressure of malware known as DirtyMoe.
The company attributed the marketing campaign to a risk actor it calls UAC-0027.
DirtyMoe, energetic since not less than 2016, is able to finishing up cryptojacking and distributed denial-of-service (DDoS) assaults. In March 2022, cybersecurity agency Avast revealed the malware’s potential to propagate in a worm-like style by making the most of recognized safety flaws.
The DDoS botnet is thought to be delivered by the use of one other malware known as Purple Fox or by way of bogus MSI installer packages for standard software program resembling Telegram. Purple Fox can also be outfitted with a rootkit that enables the risk actors to cover the malware on the machine and make it troublesome to detect and take away.
The precise preliminary entry vector used within the marketing campaign focusing on Ukraine is at present unknown. CERT-UA is recommending that organizations hold their programs up-to-date, implement community segmentation, and monitor community site visitors for any anomalous exercise.
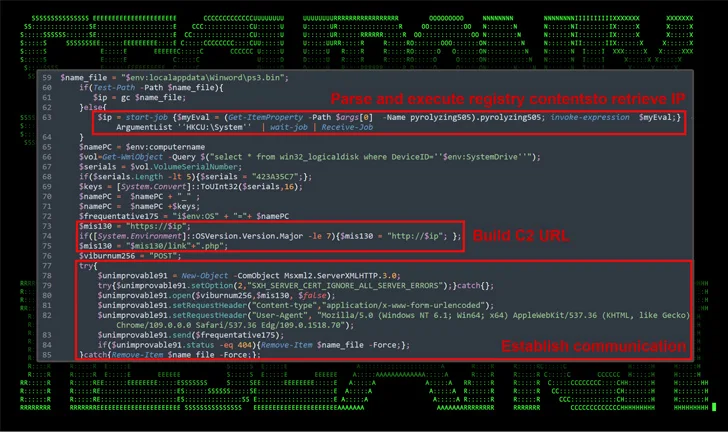
The disclosure comes as Securonix detailed an ongoing phishing marketing campaign often known as STEADY#URSA focusing on Ukrainian navy personnel with the aim of delivering a bespoke PowerShell backdoor dubbed SUBTLE-PAWS.
“The exploitation chain is comparatively easy: it entails the goal executing a malicious shortcut (.lnk) file which masses and executes a brand new PowerShell backdoor payload code (discovered inside one other file contained throughout the identical archive),” safety researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned.
The assault is alleged to be associated to a risk actor often known as Shuckworm, which is often known as Aqua Blizzard (previously Actinium), Armageddon, Gamaredon, Iron Tilden, Primitive Bear, Trident Ursa, UNC530, and Winterflounder. Lively since not less than 2013, it is assessed to be a part of Russia’s Federal Safety Service (FSB).
SUBTLE-PAWS, along with establishing persistence on the host, makes use of Telegram’s running a blog platform known as Telegraph to retrieve the command-and-control (C2) info, a method beforehand recognized as related with the adversary since early 2023, and might propagate by way of detachable connected drives.
Gamaredon’s potential to unfold by way of USB drives was additionally documented by Examine Level in November 2023, which named the PowerShell-based USB worm LitterDrifter.
“The brand new SUBTLE-PAWS assault payload may be considered as an evolution of the assault payloads by the malicious risk actor concerned within the [LitterDrifter] marketing campaign,” Kolesnikov, vp of risk analysis and information science/AI at Securonix, instructed The Hacker Information.
“For example, LitterDrifter is vbscript-based. SUBTLE-PAWS is PowerShell. There are additionally variations in how these payloads work, SUBTLE-PAWS makes use of a distinct persistence mechanism, for instance.”
“The SUBTLE-PAWS backdoor makes use of superior strategies to execute malicious payloads dynamically,” the researchers mentioned.
“They retailer and retrieve executable PowerShell code from the Home windows Registry which may help in evading conventional file-based detection strategies. This method additionally aids in sustaining persistence on the contaminated system, because the malware can provoke itself once more after reboots or different interruptions.”