
A blockchain developer shares his ordeal over the vacations when he was approached on LinkedIn by a “recruiter” for an online growth job.
The recruiter in query requested the developer to obtain npm packages from a GitHub repository, and hours later the developer found his MetaMask pockets had been emptied.
Take-home job train empties dev’s crypto pockets
Antalya-based Murat Çeliktepe, a blockchain and internet developer, shared this week how he was approached by a “recruiter” on LinkedIn with an Upwork job posting that appeared legit.
As part of the job interview, the recruiter requested Çeliktepe to obtain and debug the code in two npm packages—”web3_nextjs” and “web3_nextjs_backend” hosted on a GitHub repository. Nevertheless, moments later, the developer found that his MetaMask pockets had been drained—with upwards of $500 siphoned out of his account, primarily based on the data seen by BleepingComputer.
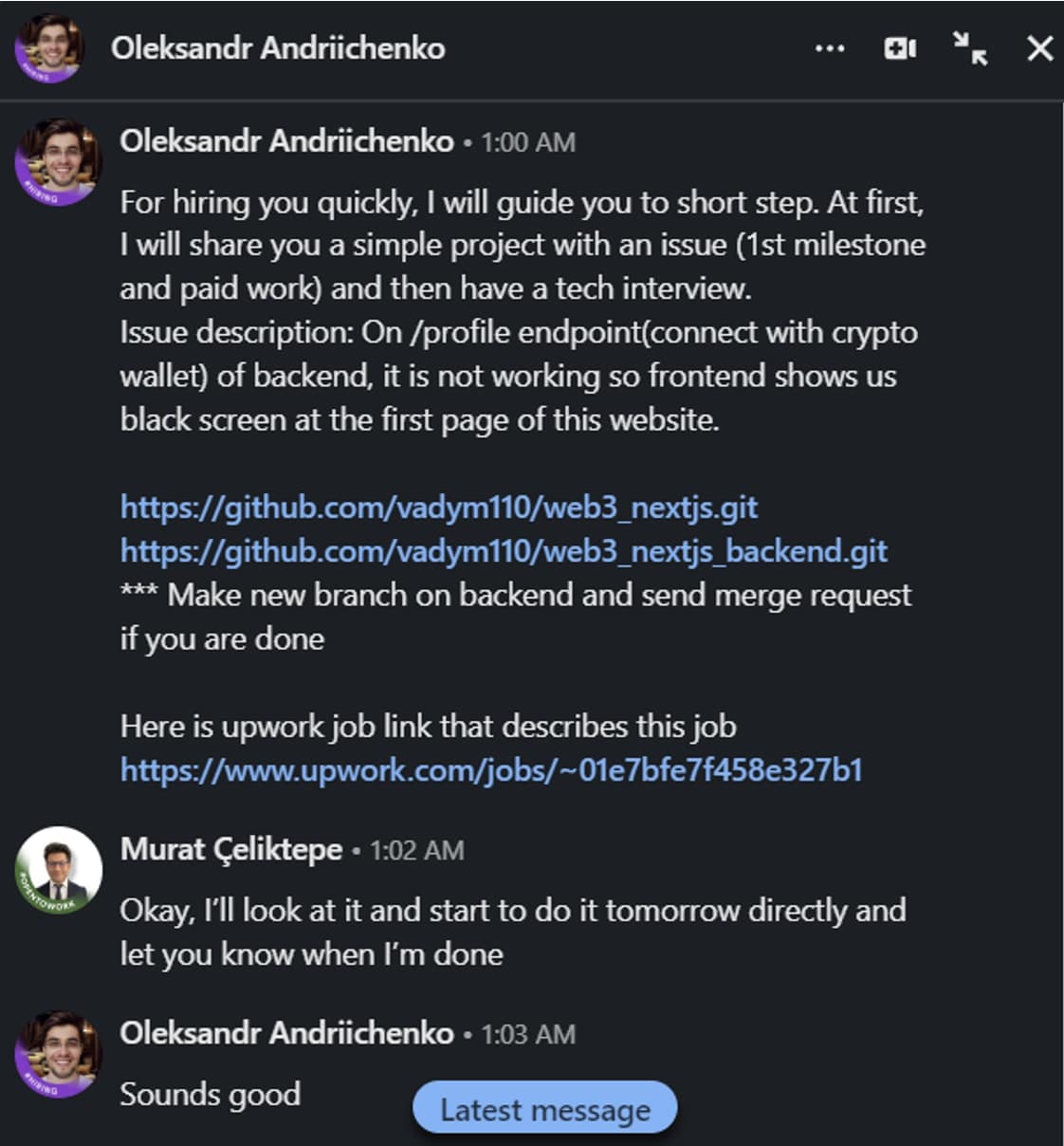
The Upwork job posting asks the applicant to “repair bugs and resopnsiveness [sic] on web site” and claims to pay between $15 and $20 hourly for a job anticipated to take beneath a month.
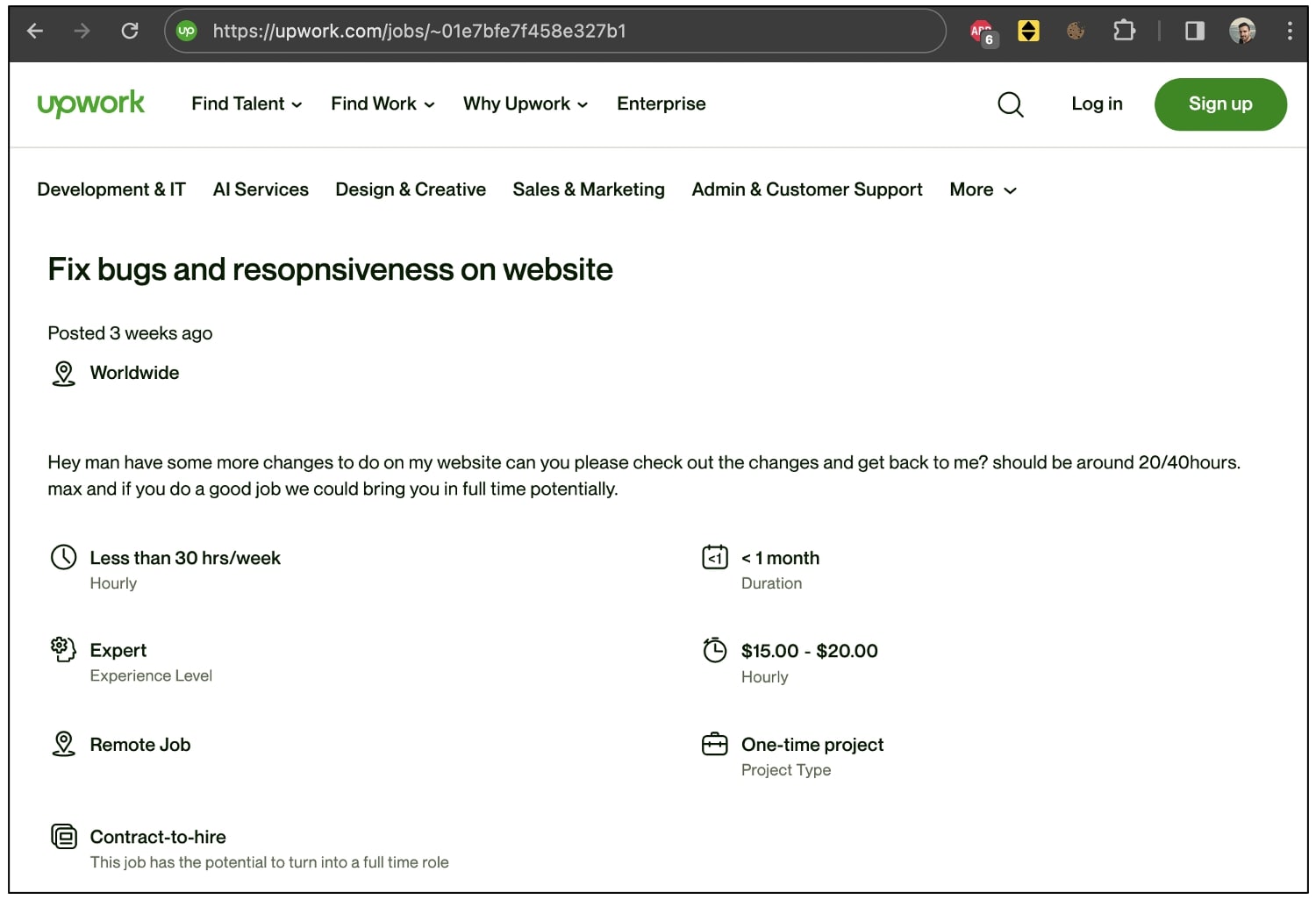
Çeliktepe, whose LinkedIn profile image bears the “#OpenToWork” tag, determined to offer this problem a go and downloaded the GitHub repositories shared by the recruiter, as part of the “tech interview.”
It is not uncommon for legit tech interviews to contain some type of take-home train or proof-of-concept (PoC) task involving code writing or debugging, which makes the lure extremely convincing even for technically savvy individuals, like builders.
(BleepingComputer)
Observe that the apps current within the mentioned GitHub repos [1, 2] are legitimate npm initiatives, given their format and the included package deal.json manifest, however these don’t seem to have ever been revealed to npmjs.com, the biggest open-source registry of JavaScript initiatives.
“My MetaMask pockets was utterly emptied… beneath the pretext of the interview course of and job task, my complete pockets was utterly emptied in a manner that I do not but perceive precisely how,” wrote Çeliktepe in Turkish on social media.
“I’ll share the codes beneath, I might be very joyful if somebody might assist me perceive how.”
As per the task directions, the developer cloned each GitHub repositories and began to debug his occasion to search out the issue whereas operating each the frontend and backend functions domestically on his machine.
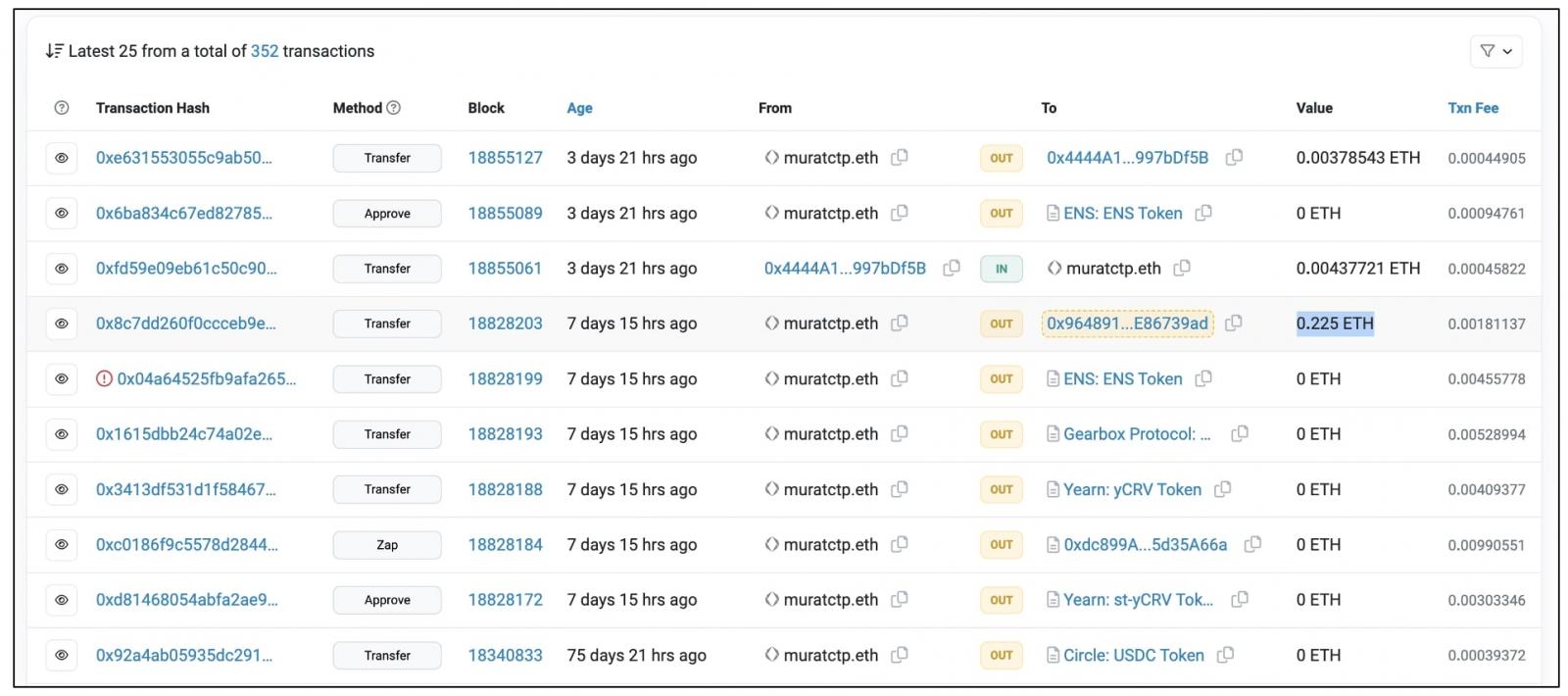
Following the duty, he attended a Google Meet session with the person who had approached him on LinkedIn, and defined the answer—and this was it, or so the developer thought. Besides, a couple of hours later, the developer seen, his Ethereum stability had been drained.
Amongst latest transactions shared by the developer and seen by BleepingComputer, is an outbound one for 0.225 ETH—roughly US$538 despatched to a different crypto deal with within the final week.
Extra devs focused in identical rip-off
Regardless of trying by means of the code current in each repositories, the developer remains to be not sure in regards to the actual mechanics of this assault that led him to lose cash and is in search of assist from the neighborhood to grasp the identical.
His attraction was rapidly adopted up by, what seemed to be opportunistic crypto bots and rip-off accounts, attractive him to get in contact with bogus “MetaMask assist” Gmail addresses and Google varieties.
Some legitimately involved neighborhood members stepped up, nonetheless, to supply their insights.
An Istanbul-based bug bounty hunter hypothesized that the npm initiatives ran by the developer successfully paved the means for the attacker to deploy a reverse shell, by opening up port 5000 on his machine that started “listening” for connections.
BleepingComputer did affirm the presence of the described code throughout the backend app [1, 2] “web3_nextjs_backend,” however we now have not been in a position to independently affirm if attackers certainly gained entry to the developer’s machine by way of this assault vector.
Moreover, Çeliktepe says he by no means saved the key “12 phrases” or what’s formally generally known as MetaMask’s Secret Restoration Phrase (SRP) on his pc and due to this fact doesn’t perceive how his MetaMask pockets was breached, even when attackers would have gained entry to his machine.
BleepingComputer additional noticed the presence of a “grasp public key” or an prolonged public key within the package deal which seems to assist generate Bitcoin addresses.
There are additionally community requests with information being made to flickthebean.onrender[.]com by a number of recordsdata inside web3_nextjs. However as soon as once more, whether or not these are all a part of a easy quasi-job interview train, or the crypto-stealing assault stays unclear.
Different theories proposed by the neighborhood members contain, moderately than the developer’s machine getting contaminated with malware, the illicit npm venture copied his passwords from an online browser that had auto-fill enabled, or that his community visitors was intercepted by the code he voluntarily ran in the course of the “tech interview.”
Regardless of the assault vector could also be, Çeliktepe is just not the one one who has been focused on this trend, and that too by the identical “recruiter.”
One other blockchain dev and safety researcher Bartu Bozkurt says he had additionally been approached for the “job” on LinkedIn, simply days prior, and calls this a “very well-known kind of hack.”
Yet one more developer, Mehmet Selim, additionally confirms being messaged by the identical recruiter who had reached out to Çeliktepe.
As such, internet builders and safety researchers ought to maintain a watch out for bogus job provides on profession growth platforms as these may very well be scams. It’s a good suggestion to finish any take-home job workout routines—regardless of how seemingly benign, on a (digital) machine that’s separate out of your major system.
h/t @KutluSoz for the tip-off.


