Menace hunters have unmasked the newest methods adopted by a malware pressure known as GuLoader in an effort to make evaluation tougher.
“Whereas GuLoader’s core performance hasn’t modified drastically over the previous few years, these fixed updates of their obfuscation strategies make analyzing GuLoader a time-consuming and resource-intensive course of,” Elastic Safety Labs researcher Daniel Stepanic stated in a report revealed this week.
First noticed in late 2019, GuLoader (aka CloudEyE) is a sophisticated shellcode-based malware downloader that is used to distribute a variety of payloads, reminiscent of info stealers, whereas incorporating a bevy of subtle anti-analysis strategies to dodge conventional safety options.
A regular stream of open-source reporting into the malware in current months has revealed the menace actors behind it have continued to enhance its means to bypass present or new safety features alongside different carried out options.
GuLoader is often unfold via phishing campaigns, the place victims are tricked into downloading and putting in the malware via emails bearing ZIP archives or hyperlinks containing a Visible Fundamental Script (VBScript) file.
Cracking the Code: Study How Cyber Attackers Exploit Human Psychology
Ever puzzled why social engineering is so efficient? Dive deep into the psychology of cyber attackers in our upcoming webinar.
Israeli cybersecurity firm Verify Level, in September 2023, revealed that “GuLoader is now offered beneath a brand new identify on the identical platform as Remcos and is implicitly promoted as a crypter that makes its payload totally undetectable by antiviruses.”
One of many current adjustments to the malware is an enchancment of an anti-analysis approach first disclosed by CrowdStroke in December 2022 and which is centered round its Vectored Exception Dealing with (VEH) functionality.
It is value mentioning that the mechanism was beforehand detailed by each McAfee Labs and Verify Level in Could 2023, with the previous stating that “GuLoader employs the VEH primarily for obfuscating the execution circulate and to decelerate the evaluation.”
The strategy “consists of breaking the traditional circulate of code execution by intentionally throwing a lot of exceptions and dealing with them in a vector exception handler that transfers management to a dynamically calculated handle,” Verify Level stated.
GuLoader is way from the one malware household to have obtained fixed updates. One other notable instance is DarkGate, a distant entry trojan (RAT) that allows attackers to completely compromise sufferer techniques.
Offered as malware-as-a-service (MaaS) by an actor often known as RastaFarEye on underground boards for a month-to-month payment of $15,000, the malware makes use of phishing emails containing hyperlinks to distribute the preliminary an infection vector: a VBScript or Microsoft Software program Installer (MSI) file.
Trellix, which analyzed the newest model of DarkGate (5.0.19), stated it “introduces a brand new execution chain utilizing DLL side-loading and enhanced shellcodes and loaders.” Additional, it comes with a whole rework of the RDP password theft characteristic.
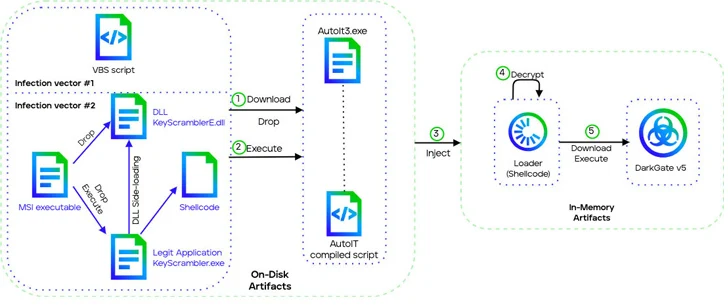 |
| (Supply: Trellix) Overview of the DarkGate v5 multi-stage set up chain |
“The menace actor has been actively monitoring menace studies to carry out fast adjustments thus evading detections,” safety researchers Ernesto Fernández Provecho, Pham Duy Phuc, Ciana Driscoll, and Vinoo Thomas stated.
“Its adaptability, the velocity with which it iterates, and the depth of its evasion strategies attest to the sophistication of recent malware threats.”
The event comes as distant entry trojans like Agent Tesla and AsyncRAT have been noticed being propagated utilizing novel email-based an infection chains that leverage steganography and unusual file varieties in an try to bypass antivirus detection measures.
It additionally follows a report from the HUMAN Satori Menace Intelligence Group about how an up to date model of a malware obfuscation engine known as ScrubCrypt (aka BatCloak) is getting used to ship the RedLine stealer malware.
“The brand new ScrubCrypt construct was offered to menace actors on a small handful of darkish net marketplaces, together with Nulled Discussion board, Cracked Discussion board, and Hack Boards,” the corporate stated.




