Cybersecurity researchers have disclosed a brand new subtle Android malware known as FjordPhantom that has been noticed focusing on customers in Southeast Asian international locations like Indonesia, Thailand, and Vietnam since early September 2023.
“Spreading primarily via messaging companies, it combines app-based malware with social engineering to defraud banking prospects,” Oslo-based cellular app safety agency Promon mentioned in an evaluation revealed Thursday.
Propagated primarily through e-mail, SMS, and messaging apps, assault chains trick recipients into downloading a purported banking app that comes fitted with professional options but in addition incorporates rogue elements.
Victims are then subjected to a social engineering approach akin to telephone-oriented assault supply (TOAD), which entails calling a bogus name heart to obtain step-by-step directions for operating the app.
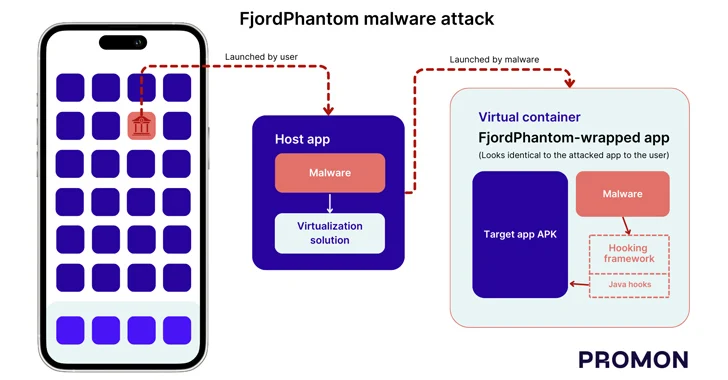
A key attribute of the malware that units it aside from different banking trojans of its variety is using virtualization to run malicious code in a container and fly underneath the radar.
The sneaky technique, Promon mentioned, breaks Android’s sandbox protections because it permits completely different apps to be run on the identical sandbox, enabling the malware to entry delicate information with out requiring root entry.
“Virtualization options just like the one utilized by the malware will also be used to inject code into an utility as a result of the virtualization answer first masses its personal code (and the whole lot else present in its app) into a brand new course of after which masses the code of the hosted utility,” safety researcher Benjamin Adolphi mentioned.
Within the case of FjordPhantom, the host app downloaded features a malicious module and the virtualization aspect that is then used to put in and launch the embedded app of the focused financial institution in a digital container.
In different phrases, the bogus app is engineered to load the financial institution’s professional app in a digital container whereas additionally using a hooking framework inside the setting to change the habits of key APIs to seize delicate data from the applying’s display programmatically and shut dialog bins used to warn malicious exercise on customers’ gadgets.
“FjordPhantom itself is written in a modular strategy to assault completely different banking apps,” Adolphi mentioned. “Relying on which banking app is embedded into the malware, it is going to carry out numerous assaults on these apps.”