
A financially motivated risk actor utilizing USB units for preliminary an infection has been discovered abusing authentic on-line platforms, together with GitHub, Vimeo, and Ars Technica, to host encoded payloads embedded in seemingly benign content material.
The attackers cover these payloads in plain sight, inserting them in discussion board consumer profiles on tech information websites or video descriptions on media internet hosting platforms.
These payloads pose no dangers to customers visiting these net pages, as they’re merely textual content strings. Nevertheless, when built-in into the marketing campaign’s assault chain, they’re pivotal in downloading and executing malware in assaults.
The hackers liable for this marketing campaign are tracked by Mandiant as UNC4990 and have been lively since 2020, predominately concentrating on customers in Italy.
Involuntary payload internet hosting
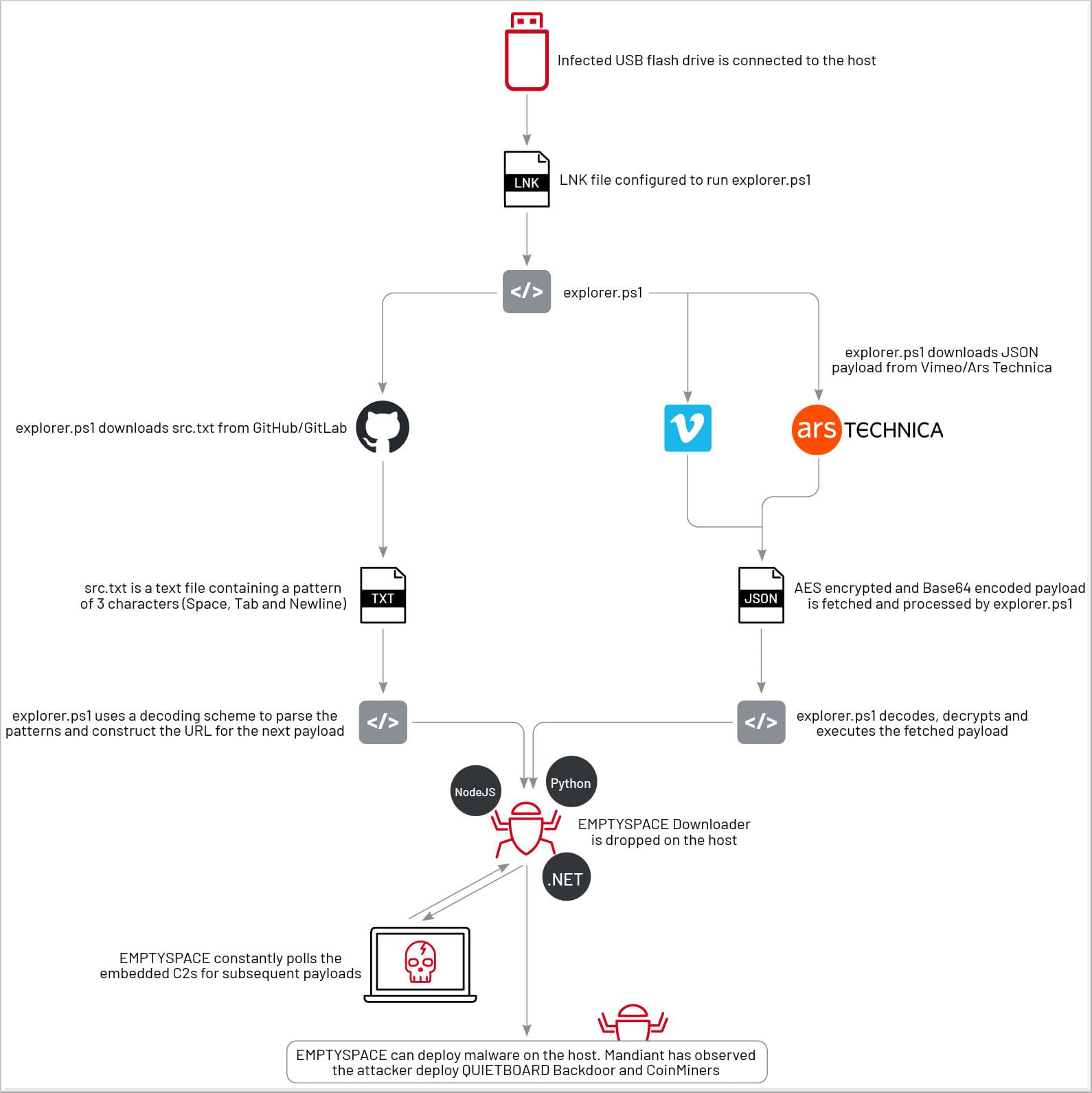
The assault begins with victims double-clicking a malicious LNK shortcut file on a USB drive. It’s not recognized how the malicious USB units make it to focused victims to start out the assault chain.
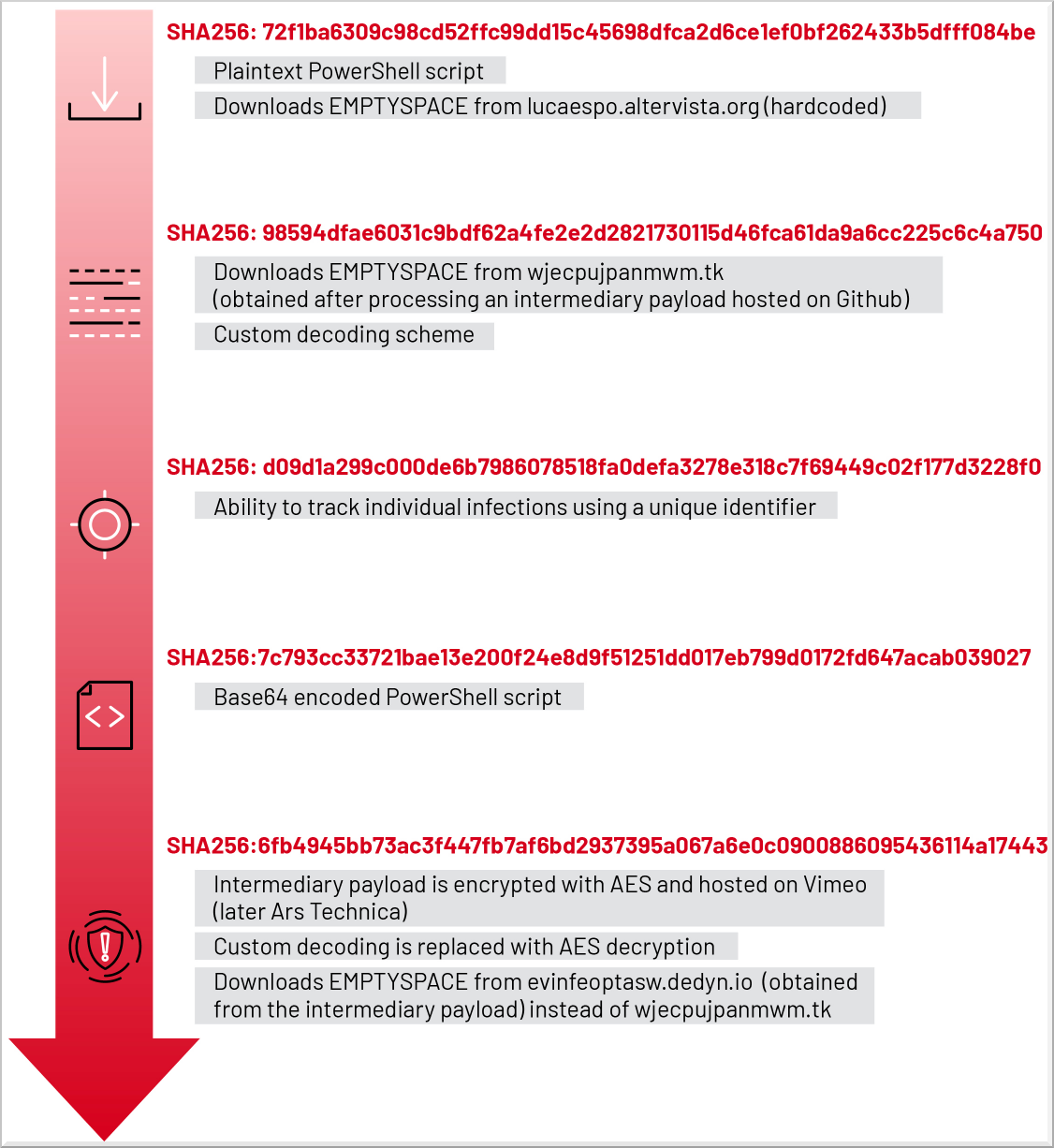
When the shortcut is launched, it executes a PowerShell script explorer.ps1, which in flip downloads an middleman payload that decodes to a URL used to obtain and set up the malware downloader named ‘EMPTYSPACE.’
These middleman payloads are textual content strings that decode right into a URL to obtain the following payload: EMPTYSPACE.
UNC4990 has tried out a number of approaches to internet hosting middleman payloads, initially utilizing encoded textual content information on GitHub and GitLab and later switching to abusing Vimeo and Ars Technica for internet hosting Base64 encoded and AES-encrypted string payloads.
Mandiant notes that the attackers don’t exploit a vulnerability in these websites however merely make use of common website options, like an About web page in an Ars Technica discussion board profile or a Vimeo video description, to covertly host the obfuscated payload with out elevating suspicion.
.png)
Supply: Mandiant
Additionally, these payloads don’t immediately threaten the guests of the abused websites as they’re simply innocent textual content strings, and all circumstances documented by Mandiant have now been faraway from the impacted middleman platforms.
The benefit of internet hosting the payloads on authentic and respected platforms is that they’re trusted by safety methods, decreasing the probability of them being flagged as suspicious.
Furthermore, the risk actors profit from these platforms’ strong content material supply networks and luxuriate in resilience to takedowns.
Embedding the payloads inside authentic content material and mixing it with excessive volumes of authentic site visitors makes it harder to pinpoint and take away the malicious code.
Even then, the attackers may simply re-introduce it on a special platform that helps publicly viewable feedback or profiles.
Supply: Mandiant
Loading Quietboard
The PowerShell script decodes, decrypts, and executes the intermediate payload fetched from the authentic websites and drops EMPTYSPACE on the contaminated system, which establishes communication with the marketing campaign’s command and management (C2) server.
Supply: Mandiant
Within the subsequent phases of the assault, EMPTYSPACE downloads a backdoor named ‘QUIETBOARD,’ in addition to crypto coin miners that mine Monero, Ethereum, Dogecoin, and Bitcoin.
The pockets addresses linked to this marketing campaign have made a revenue that surpasses $55,000, not accounting for Monero, which is hidden.
QUIETBOARD is a classy, multi-component backdoor utilized by UNC4990, providing a variety of capabilities, together with:
- Executing instructions or scripts acquired from the C2 server
- Executing Python code acquired from the C2
- Altering clipboard content material for cryptocurrency theft
- Infecting USB/detachable drives to unfold malware on different methods
- Capturing screenshots for info theft
- Gathering detailed system and community info
- Figuring out the geographical location of the contaminated system
QUIETBOARD additionally establishes persistence throughout system reboots and helps dynamically including new functionalities by way of further modules.
Mandiant concludes by underlining how UNC4990 likes to conduct experiments with its campaigns to find optimum pathways for its assault chain and refinement of its methodologies.
Regardless of the seemingly easy prevention measures, USB-based malware continues to pose a major risk and serve cybercriminals as an efficient propagation medium.
As for the tactic of abusing authentic websites to plant intermediate payloads, this exhibits that threats can lurk in sudden, seemingly innocuous areas, difficult typical safety paradigms.


