
A beforehand unknown visitors distribution system (TDS) named ‘VexTrio’ has been energetic since at the least 2017, aiding 60 associates of their cybercrime operations via an enormous community of 70,000 websites.
Visitors Distribution Methods (TDS) are providers that take incoming visitors and redirect the person to a different web site relying on the customer’s working system, IP deal with, gadget, geographic area, and different standards.
For reputable causes, a TDS is often utilized in affiliate marketing online. Nonetheless, in cybercrime, they redirect unsuspecting customers to malicious locations like phishing pages, exploit kits, and malware-dropping websites.
One such case is Parrot TDS, highlighted just lately in a Unit 42 report that introduced proof of the operation remaining energetic and growing.
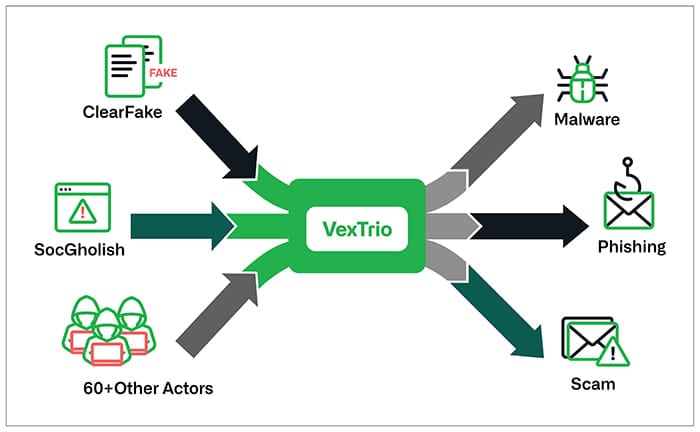
A brand new report by Infoblox focuses on a a lot larger-scale TDS operation named VexTrio, which works with infamous cybercrime campaigns and operators like ClearFake and SocGholish, amongst others.
Serving cybercrime since 2017
VexTrio has been recognized by Infoblox as a extremely pervasive entity throughout the cybercrime panorama, commanding an enormous community that performs a central function within the distribution of malicious content material.
VexTrio controls over 70,000 compromised websites, a testomony to its intensive attain, enabling the platform to distribute malicious content material to guests throughout a big selection of internet sites and providers.
Usually, websites are hacked to inject malicious redirection scripts into the HTML of weak websites. In different instances, the risk actors merely create their very own web sites and make the most of blackhat search engine optimization ways to generate visitors.
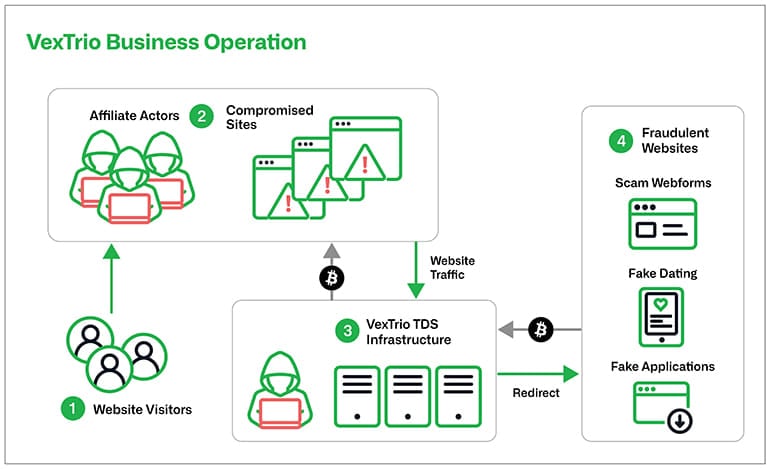
The platform acts as an middleman visitors dealer in alternate for cash from cybercrime teams, redirecting guests of the websites underneath its management to prospects’ malicious locations.
VexTrio additionally extends its attain by partnering with at the least 60 entities, or associates, who ahead visitors from their sources, comparable to compromised web sites, to VexTrio’s TDS servers.
Supply: Infoblox
Infoblox notes that these partnerships don’t seem short-lived, as they noticed instances that prolonged for as much as 4 years, exhibiting a excessive stage of belief and mutual profit.
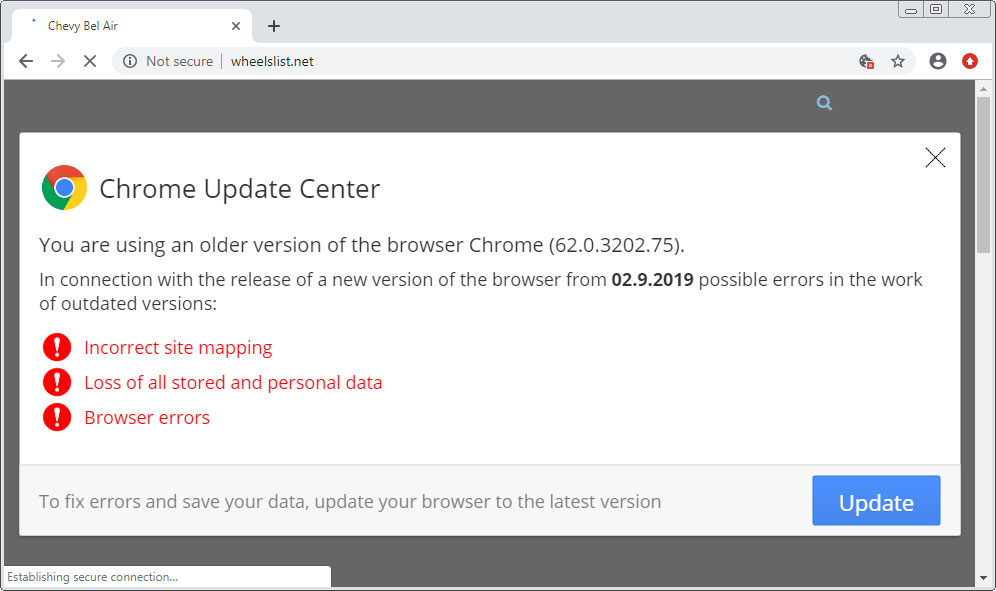
One in all VexTrio’s companions is ClearFake, a malware marketing campaign that shows prompts on hacked websites telling guests to put in faux browser updates, which set up malware on the gadget.
ClearFake has been a VexTrio affiliate for 5 months, however as a substitute of straight forwarding visitors to the platform’s TDS servers, it makes use of the Keitaro service as an intermediate redirection level.
The SocGholish malware marketing campaign has additionally collaborated with VexTrio since at the least April 2022, in keeping with Infoblox, additionally counting on the Keitaro TDS service for a midpoint bounce. Traditionally, SocGholish was utilized by ransomware gangs to realize preliminary entry to company networks.
Supply: BleepingComputer
The range and complexity within the assault chains, which concerned a number of risk actors, make VexTrio exercise onerous to map, detect, and mitigate.
Various income sources
Furthermore, the analysts have discovered that VexTrio and its associates typically abuse referral applications from reputable platforms to generate income by redirecting victims to trusted websites through affiliate hyperlinks.
By intertwining their operations with reputable providers, VexTrio and its associates make it tougher for each customers and safety methods to discern their malicious actions.
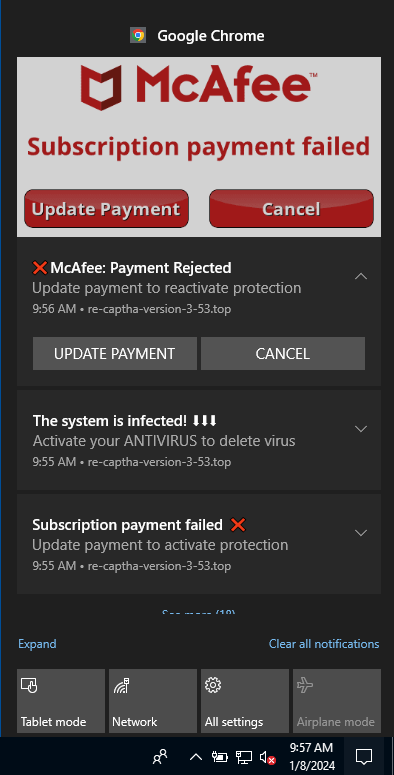
Infoblox’s report highlights a crafty and misleading VexTrio marketing campaign named ‘robotic CAPTCHA,’ which the group makes use of in its referral era efforts.
On this marketing campaign, customers visiting compromised websites are redirected to what seems as a reputable CAPTCHA check, which methods the person into clicking an ‘Enable’ button, inadvertently granting the web site permission to ship push notifications via the person’s browser.
Then, VexTrio’s servers can push bogus notifications to the sufferer anytime, masquerading as system warnings, AV alerts, and different seemingly credible alerts. VexTrio even ensures these alerts are within the right language by utilizing JS modules to dynamically alter the language primarily based on the person’s browser knowledge.
Supply: Infoblox
Clicking on the misleading notifications might lead victims to touchdown pages that generate referral income for VexTrio.
Contemplating the complexity, resilience, and variety in income streams and an infection chains, VexTrio shall be very onerous to eradicate, though figuring out and mapping its websites is a strong first step.
Infoblox means that customers mitigate the risk by limiting their searching solely to SSL-certified websites, blocking push notifications on their browsers, and utilizing ad-blocking instruments that may stop popup adverts from loading.


