A brand new Mirai-based botnet referred to as NoaBot is being utilized by risk actors as a part of a crypto mining marketing campaign because the starting of 2023.
“The capabilities of the brand new botnet, NoaBot, embody a wormable self-spreader and an SSH key backdoor to obtain and execute extra binaries or unfold itself to new victims,” Akamai safety researcher Stiv Kupchik mentioned in a report shared with The Hacker Information.
Mirai, which had its supply code leaked in 2016, has been the progenitor of plenty of botnets, the latest being InfectedSlurs, which is able to mounting distributed denial-of-service (DDoS) assaults.
There are indications that NoaBot could possibly be linked to a different botnet marketing campaign involving a Rust-based malware household often known as P2PInfect, which not too long ago obtained an replace to focus on routers and IoT units.
That is based mostly on the truth that risk actors have additionally experimented with dropping P2PInfect instead of NoaBot in current assaults focusing on SSH servers, indicating seemingly makes an attempt to pivot to customized malware.
Regardless of NaoBot’s Mirai foundations, its spreader module leverages an SSH scanner to seek for servers vulnerable to dictionary assault with a purpose to brute-force them and add an SSH public key within the .ssh/authorized_keys file for distant entry. Optionally, it could additionally obtain and execute extra binaries put up profitable exploitation or propagate itself to new victims.
“NoaBot is compiled with uClibc, which appears to vary how antivirus engines detect the malware,” Kupchik famous. “Whereas different Mirai variants are often detected with a Mirai signature, NoaBot’s antivirus signatures are of an SSH scanner or a generic trojan.”
In addition to incorporating obfuscation techniques to render evaluation difficult, the assault chain in the end leads to the deployment of a modified model of the XMRig coin miner.
What makes the brand new variant a reduce above different related Mirai botnet-based campaigns is that it doesn’t comprise any details about the mining pool or the pockets deal with, thereby making it unattainable to evaluate the profitability of the illicit cryptocurrency mining scheme.
“The miner obfuscates its configuration and in addition makes use of a customized mining pool to keep away from exposing the pockets deal with utilized by the miner,” Kupchik mentioned, highlighting some stage of preparedness of the risk actors.
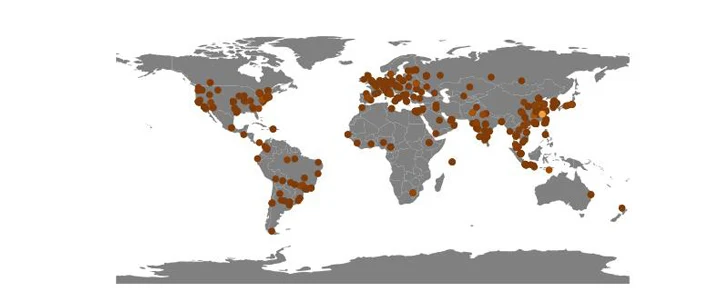
Akamai mentioned it recognized 849 sufferer IP addresses thus far which are unfold geographically internationally, with excessive concentrations reported in China, a lot in order that it quantities to nearly 10% of all assaults in opposition to its honeypots in 2023.
“The malware’s technique of lateral motion is by way of plain previous SSH credentials dictionary assaults,” Kupchik mentioned. “Proscribing arbitrary web SSH entry to your community vastly diminishes the dangers of an infection. As well as, utilizing sturdy (not default or randomly generated) passwords additionally makes your community safer, because the malware makes use of a fundamental checklist of guessable passwords.”