
A marketing campaign delivering the AsyncRAT malware to pick targets has been lively for not less than the previous 11 months, utilizing a whole lot of distinctive loader samples and greater than 100 domains.
AsyncRAT is an open-source distant entry instrument (RAT) for Home windows, publicly obtainable since 2019, with features for distant command execution, keylogging, knowledge exfiltration, and dropping extra payloads.
The instrument has been closely utilized by cybercriminals over time, both as is or in modified type, for establishing a foothold on the goal, stealing information and knowledge, and deploying extra malware.
Microsoft safety researcher Igal Lytzki noticed the assaults delivered over hijacked e mail threads final summer season however could not retrieve the ultimate payload.
In September, AT&T’s Alien Labs crew of researchers observed “a spike in phishing emails, focusing on particular people in sure corporations” and began to research.
The assaults start with a malicious e mail carrying a GIF attachment that results in an SVG file that downloads an obfuscated JavaScript and PowerShell scripts.
After spending some anti-sandboxing checks, the loader communicates with the command and management (C2) server and determines if the sufferer is eligible for the AsyncRAT an infection.
The hardcoded C2 domains are hosted on BitLaunch, a service that permits nameless funds in cryptocurrency, a helpful choice for cybercriminals.
If the loader determines that it runs in an evaluation surroundings, it deploys decoy payloads, possible in an try to mislead safety researchers and menace detection instruments.
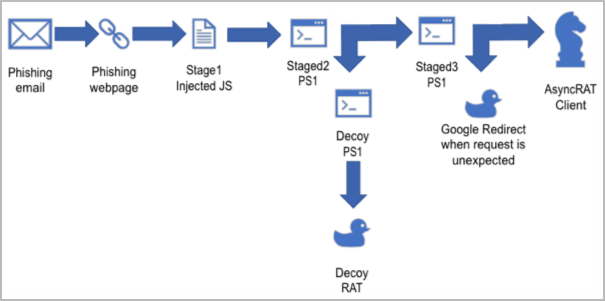
The anti-sandboxing system employed by the loader entails a sequence of verifications carried out through PowerShell instructions that retrieve system data particulars and calculate a rating that signifies if it runs in a digital machine.
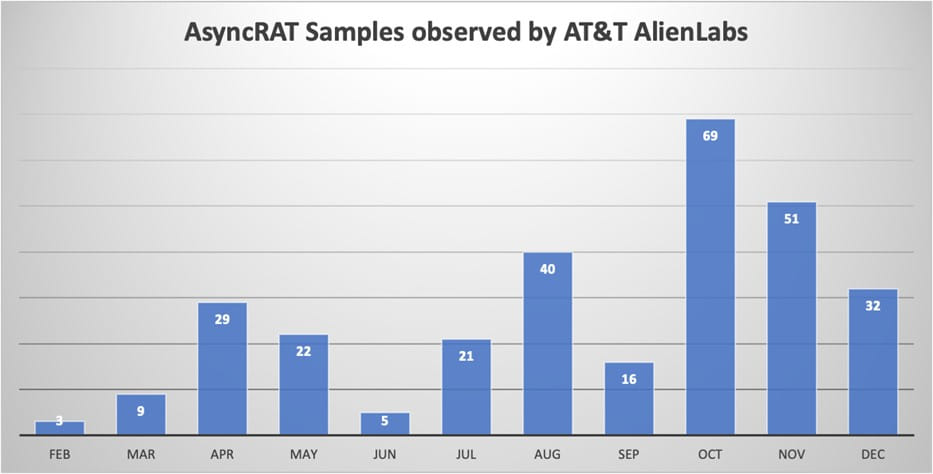
AT&T Alien Labs decided that the menace actor used 300 distinctive samples of the loader previously 11 months, every with minor alterations within the code construction, obfuscation, and variable names and values.
One other remark from the researchers is using a website era algorithm (DGA) that generates new C2 domains each Sunday.
Based on AT&T Alien Labs’ findings, the domains used within the marketing campaign observe a particular construction: are within the “high” TLD, use eight random alphanumeric characters, are registered in Nicenic.internet, use South Africa for the nation code, and are hosted on DigitalOcean.
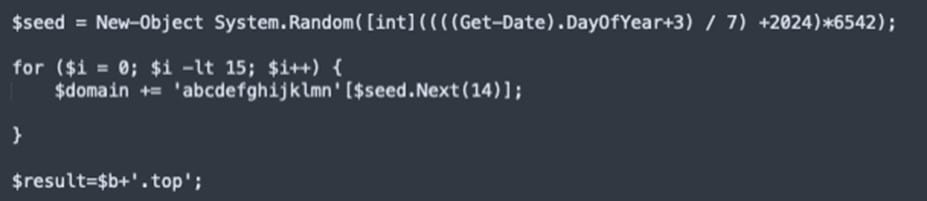
AT&T was capable of decode the logic behind the area era system, and even predicted the domains that will probably be generated and assigned to the malware all through January 2024.
The researchers didn’t attribute the assaults to a particular adversary however notice that these “menace actors worth discretion,” as indicated by the hassle to obfuscate the samples.
The Alien Labs crew present a set of indicators of compromise together with signatures for the Suricata community evaluation and menace detection software program that corporations can use to detect intrusions related to this AsyncRAT marketing campaign.


